(Image source: WordPress )
WordPress, the easiest and most powerful blogging and website content management system, has silently fixed a dangerous vulnerability in WordPress REST API Endpoint, which adds to WordPress version 4.7.0 and enables it by default. In WordPress Vulnerability, an unauthenticated privilege escalation vulnerability has affected the REST API. It potentially leads to Remote Code Execution depending on the plugins installed on a site. Using a patch management software, we can patch the vulnerability.
The REST API (Representational State Transfer Application Programming Interface) enables WP to easily communicate with other websites and services, as it is JSON based and allows to exchange of content and data with other web properties regardless of writing in different programming languages. A vulnerability management tool can detect this vulnerability.
Where does the WordPress Vulnerability exist?
The “./wp-includes/rest-api/endpoints/class-wp-rest-posts-controller.php” script in WordPress 4.7.0 has a function register_rest_route which is designed to set ID parameter with digits. “/wp/v2/posts/” is the endpoint for creating, deleting or updating WP posts. If we want to update any post on WordPress, send a request to the endpoint API with the ID as 111, the endpoint for updating the post will be “/wp-json/wp/v2/posts/111“.
Please refer to the image below for register_rest_route function implementation.
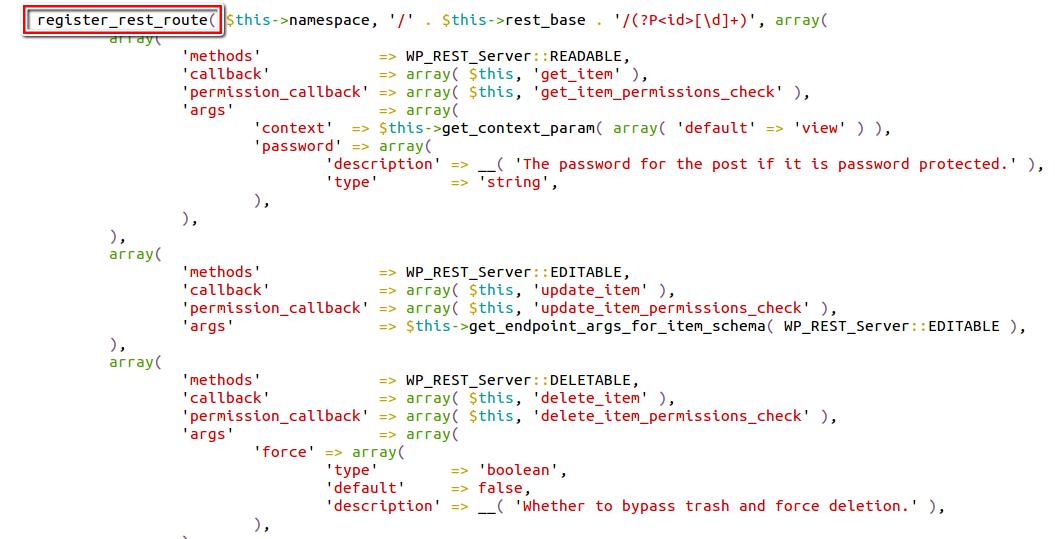 Adding an id to the end of an endpoint alone can avoid adding a malicious id, but the ‘id’ parameter in REST API accepts non-numeric digits which are key to exploit the vulnerability further.
Adding an id to the end of an endpoint alone can avoid adding a malicious id, but the ‘id’ parameter in REST API accepts non-numeric digits which are key to exploit the vulnerability further.
i.e a crafted request like “/wp-json/wp/v2/posts/111?id=111SecPodTest, will assign parameter ‘id’ value with ‘111SecPodTest‘ which has both digits and letters .
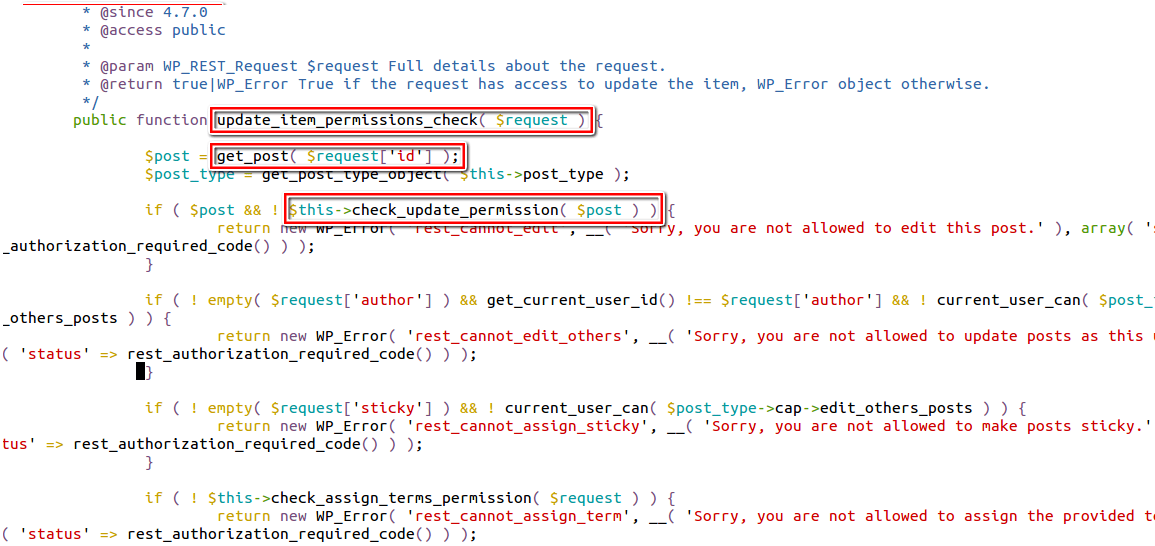
Now our alphanumeric id (111SecPodTest) will be sent to function update_item_permissions_check (as seen in the above image) to check whether the post with the corresponding id exists and has proper permissions to edit the post. The only case where it stops you from continuing further is when the bar with the given crafted id exists and consent to edit the post doesn’t exist. But in our case, the post id assigned does not exist, and we can pass through to continue execution with the update_item method without being stopped because all WordPress posts have numeric IDs.
The image below shows the implementation of the `update_item` method.
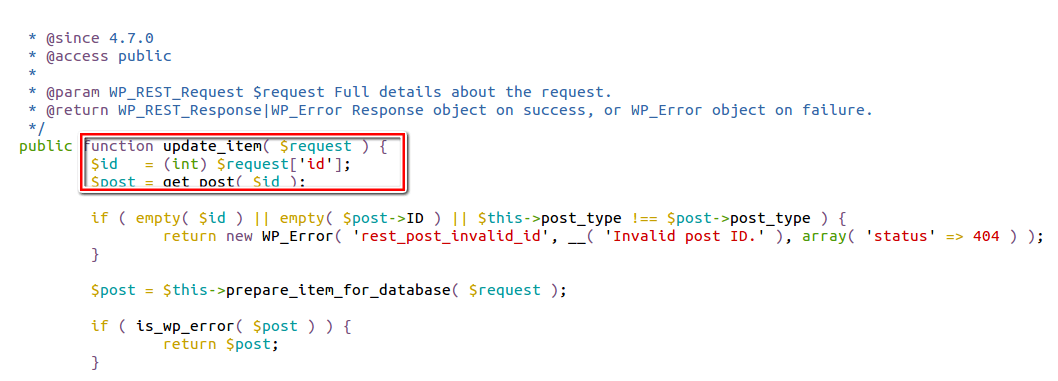
The update_item method accepts the non-numeric id where it uses PHP’s int casting (as seen in the above image) to convert the accepted id to an integer. The system will convert the crafted id parameter containing the value ‘111SecPodTest’ to ‘111’. This represents an existing valid post id.
An example code demonstration on how PHP’s int casting works.
php > $id = "111SecPodTest";
php > echo (int) $id .PHP_EOL;
111
php >
Once the system converts the id to an integer. It finds the post with the corresponding converted id, the update will be applied successfully. Attackers can also perform something like /wp-json/wp/v2/posts/111?id=222SecPodTest to change the post whose ID is 222.
How Dangerous is this Vulnerability?
Using this Content Injection vulnerability attackers can run automated attacks with random id’s (1 to n) to edit the posts, which can add advertisements to posts, or modify the contents of the post.
However, in WordPress Vulnerability, an unauthenticated attacker can inject malicious JavaScript, HTML code into the posts. Just clicking the link may redirect the target to a malicious site hosted by the malware. Or if an exploit kit is residing on the website it will exploit the browser-related vulnerabilities. However, This may lead to the automatic download of malware into the user’s machines and compromise the systems.
Moreover, depending on the plugins installed on the site, attackers can execute even PHP code very quickly.
Moreover, just an automated attack of the WordPress Vulnerability can compromise thousands of posts at a single shot. , successfully exploiting this vulnerability could lead to content injection and code execution. It is critical since most of the world’s top websites run WordPress.
Affected Versions:
WordPress Versions 4.7.0 and 4.7.1
What to do?
In addition, WordPress has successfully patched the vulnerability in its latest release. Further, the auto-update system in WordPress automatically updates sites to version 4.7.2. If you haven’t enabled the auto update feature, then please do it asap.
WordPress security advisory states:
We believe transparency is in the public’s best interest. It is our stance that security issues should always be disclosed. In this case, we intentionally delayed disclosing this issue by one week to ensure the safety of millions of additional WordPress sites.
WordPress 4.7.2 released to the world. The release went out over our auto update system and, over a couple of hours, millions of WordPress 4.7.x users were protected without knowing about the issue or taking any action at all.
Kashinath T
Security Research Engineer