DROWN (Decrypting RSA with Obsolete and Weakened Encryption):
OpenSSL is an open source application which contains implementation of SSL (Secure Sockets Layer) and TLS (Transport Layer Security) protocols. libcrypto and libssl are 2 primary libraries of OpenSSL.
Libcrypto library is used for general-purpose cryptography, libssl provides SSL and TLS protocol support and depends on libcrypto.
DROWN stands for “Decrypting RSA using Obsolete and Weakened eNcryption.” The principle behind this attack is SSLv2 implementation against TLS known as cross-protocol attack, which uses weaknesses in SSLv2 on an improperly configured server. A reliable vulnerability management solution can stop this attack.
However, a patch management solution is needed to help prevent this attack by patching the vulnerabilities.
There are mainly 2 types of attacks:
1) Bleichenbacher’s padding oracle attack SSLv2: Bleichenbacher’s padding oracle attack is a flexible chosen ciphertext attack against RSA PKCS#1 v1.5, the RSA padding standard used in TLS. SSLv2 is completely vulnerable to Bleichenbacher attack which allows decryption of RSA ciphertexts. It’s a protocol level flaw in SSLv2 that allows attack for 40bit export ciphers.
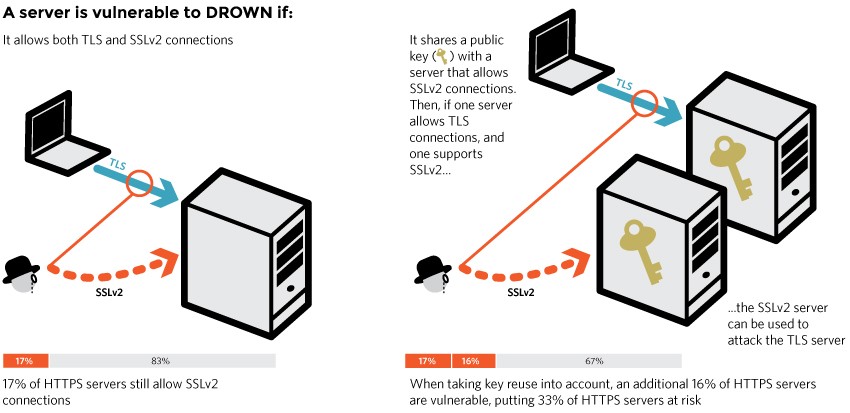
2) DROWN – Use SSLv2 to break TLS: This is a cross protocol attack which allows attacker to decrypt TLS connections by making crafted connection to an SSLv2 (possibly on different) server which uses the same RSA private key.
The DROWN attack conditions for server:
1) Communication between client and server by an attacker when SSLv2 enables on server along with TLS connection. Users using a server supporting SSLv2 protocol are vulnerable to SSLv2 DROWN Attack Vulnerability.
2) Users who have installed vulnerable version of OpenSSL or enabled SSLv2 on their server machines are prone to attack.
3) SSLv2 disables in some servers even though shared private key with other servers having SSLv2, also prone to attack.
SSLv2 implementation that export ciphersuites uses to decrypt the contents of a normal TLS-based RSA ciphertext, if both SSLv2 and TLS protocols use the same secret key. Also, This attack works only one out of a thousand TLS handshake, not every time.
(image:drownattack.com)
CVE-2016-0800 assigned for DROWN attack.
The OpenSSL addressed seven more vulnerabilities.
CVE-2016-0705, CVE-2016-0798, CVE-2016-0797, CVE-2016-0799, CVE-2016-0702 vulnerabilities addressed in OpenSSL version 1.0.1s and 1.0.2g. However, by default, SSLv2 disabled at the time of build in patched versions of OpenSSL like 1.0.2g and 1.0.1s.
CVE-2016-0703, CVE-2016-0704 vulnerabilities addressed in OpenSSL version 0.9.8zf, 1.0.0r, 1.0.1m and 1.0.2a.
Also, Support for OpenSSL 0.9.8 and 1.0.0 ended users recommended to uninstall or upgrade to latest OpenSSL version.
Online Test for DROWN Vulnerability
1. Visit website https://test.drownattack.com
2. Enter the domain name or IP address tested for DROWN vulnerability.
Test for DROWN Vulnerability using tlsfuzzer tool
tlsfuzzer tool used to find DROWN Vulnerability and automated.
1) Download the tools tlsfuzzer
2) Follow the instructions provided in the website to install the tools
3) Run following commands
– python scripts/test-sslv2-force-export-cipher.py -h your_website.com -p 443
– python scripts/test-sslv2-force-cipher.py -h your_website.com -p 443
4) In both cases all the individual tests in the scripts should print “OK” status
OR
follow the instructions provided here.
Solution to DROWN:
Apache:
Apache httpd 2.2.x supports SSLv2 by default hence it is vulnerable.
– Add the following line in Apache’s httpd.conf,
SSLProtocol All -SSLv2 -SSLv3
NginX:
Users who have explicitly turned on SSLv2 or use an NGINX version earlier than 0.8.19 are vulnerable, SSL and TLS protocols are controlled by the ssl_protocols configuration directive, In order to enable recent TLS only, and disable SSL v2 and SSL v3, use the following syntax
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
and make sure the sslv2 not present in ssl_protocols.
OpenSSL:
However, easiest and recommended solution is to upgrade 1.0.2 and 1.0.1 to 1.0.2g and 1.0.1s respectively. Users of older OpenSSL versions should upgrade to either one of these versions.
SecPod Saner detects these vulnerabilities and automatically fixes it by applying security updates. Download Saner now and keep your systems updated and secure.