SMBLoris is a remote, unauthenticated application-level denial of service (DoS) attack against Microsoft Windows operating systems. A vulnerability of this kind can be tracked using an appropriate vulnerability management tool. The Server Message Block (SMB) network protocol implementation causes it due to a very old memory-handling bug. The vulnerability is in how the system processes SMB packets and allocates memory. Two RiskSense security researchers — Sean Dillon and Jenna Magius — discovered it in 2009 and named it after the Slowloris attack on web servers. SMBLoris is the same thing as Slowloris but instead of HTTP, its done via SMB.
SMBLoris affects all modern versions of Windows from Windows 2000 through Windows 10 and three SMBs – SMBv1, SMBv2, and SMBv3. Samba which is an alternative to SMB for other operating systems is also vulnerable in a default install.
Technical Details of SMBLoris:
SMB runs on port 445. The NetBIOS service on port 139 is probably also exploitable. The NetBIOS Session Service (NBSS) header initially transmits the data for any SMB session and undergoes processing before establishing any SMB authentication mechanism. NBSS header occupies 4 bytes of memory.
The structure of NetBIOS Session Service (NBSS) header can be understood from figure below:
First 8 bits of NetBIOS Session Service (NBSS) header represent message type, next 7 bits represent flags and last 17 bits represent the length of SMB message. When a computer running an SMB service receives an NBSS header, it immediately allocates in memory the number of bytes determined by the Length field of the NBSS header. By sending a 17-bit NBSS length field set to the max value of 2 raise to power 17, allocates the SMB service allocates a max of 131072 bits (128 KiB). The kernel keeps the connection open for 30 seconds and then gives up. For every connection attempted, it ties up 128KiB of memory in the “non-paged pool” (physical RAM) for 30 seconds, and this allocated memory cannot be swapped out to disk. The SMBLoris flaw is dangerous and slows down Microsoft Windows operating systems. To avoid these flaws we should use a good vulnerability management software.

Memory Consumption:
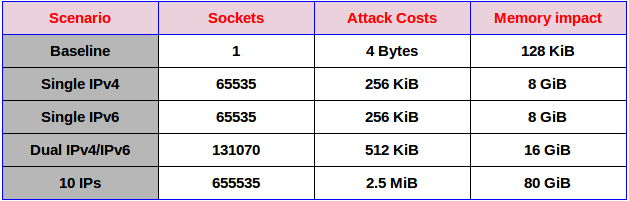
If attacker fires off a connection request for every TCP port possible – up to 65535, potentially it can chew through up to 8GiB of non-paged RAM for half a minute. This will hamper the performance of the machine. Additionally, if an attacker launches this attack on IPv4 and IPv6, that memory consumption increases to 16GiB. If an attack comes from ten IPs, an attacker can fill 80GiB, and so on. Eventually, the target can’t allocate memory and needs a manual reboot if it becomes unresponsive.
Memory Impact
In short, computationally, it is very inexpensive for anyone to cause large memory allocations and waste enormous amounts of CPU cycles making vulnerable machines completely unusable and even causing the entire operating system to crash.
The SMBLoris flaw is dangerous as it allows an attacker to open tens of thousands of connections to the same machine, exhausting its RAM and potentially crashing the target’s computer. This vulnerability does not cause remote code execution but an attacker can get critical services to crash and can completely freeze the system. A PoC is also available here.
Solution to SMBLoris:
No patch exists for SMBloris vulnerability at this time. According to Microsoft, SMBloris vulnerability is a moderate issue as firewall rules block the SMB port at the network edge. Inside of a network, its usage would only announce and pinpoint the attacker as it requires sending a large number of unauthenticated SMB connections. Microsoft has announced that they will not fix SMBloris vulnerability immediately but will likely address it later to prevent it from affecting unmanaged consumer users with no firewalls configured.
Mitigation:
Disabling the SMB protocol on Windows will not help according to the two RiskSense researchers, Dillon and Zach. The only way to prevent an SMBloris attack is to place a computer running an SMB service behind a firewall that blocks incoming SMB connections or limits their incoming SMB connections to a smaller value. In case of samba on Linux, admins can set “max smbd processes = 1000” in the Samba smb.conf config file to prevent attackers from opening a large number of SMB connections to the Samba server that eventually prevents SMBloris.