In the first week of April 2017, an unknown hacking group called Shadow Brokers leaks an exploitation framework named FuzzBunch. From the Equation Group (one of the world’s most sophisticated attack groups and widely suspected of having ties to the United States National Security Agency (NSA)). Resolving this issue would be simpler with a Vulnerability Management Tool.
This framework consisted of several unauthenticated remote exploits for Windows (such as the exploits codenamed EternalBlue, EternalRomance, and EternalSynergy), Windows implants, and other hacking tools. One of these hacking tools is a backdoor implant codenamed DOUBLEPULSAR. It is a backdoor use to inject and run malicious code on an infection system. It gets installed and used by ETERNALBLUE. EternalBlue is an SMBv1 (Server Message Block 1.0) exploit that could trigger an RCE and attack SMB file-sharing services. It is believed to have originated with the NSA. Also, to be noted, it is a RAM-resident implant. That is, the attack lives in memory.
DoublePulsar features:
DoublePulsar is a sophisticated, multi-architecture memory-based kernel payload that hooks onto x86 and 64-bit systems and allows an attacker to execute any raw shellcode payload. It is a full kernel payload giving full control over the system. It does not open new ports but make use of the same port as the one the SMB service runs on. This malware infects computers running Windows and it opens a backdoor through which other malware can be loaded onto infected computers. As per Dan Tentler (CEO and founder of Phobos Croup) once the DoublePulsar is present, it can do any of the four following things:
1) either it responds to a specific ping request (such as a heartbeat),
2) it can uninstall itself,
3) load shellcode, or
4) run a DLL on the host.
These are the only purpose of this malware.
DOUBLEPULSAR is a loading dock for extra malware whose purpose is to provide a covert channel by which to load other malware or executables. All the SMB and RDP exploits in the FuzzBunch exploitation framework use DoublePulsar as the primary payload.
DOUBLEPULSAR exists as a covert channel, which uses SMB features that have not been of use, particularly the “Trans2” feature. Trans2 is short for “Transaction 2 Subcommand Extension”. It’s a unique payload because it can infect a system, stay low for a bit, and return later when it wants to do something more intrusive. Note that the presence of DOUBLEPULSAR doesn’t mean they’re in danger by the NSA. It means there is a loading dock ready and waiting for whatever malware anyone wants to give it.

How to check system is in danger of DoublePulsar?
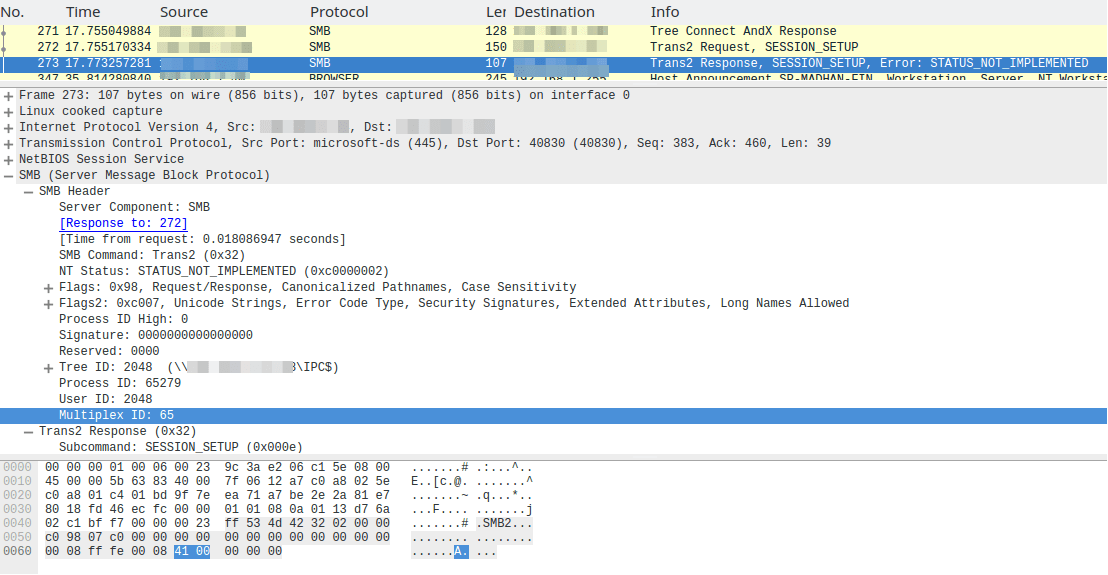
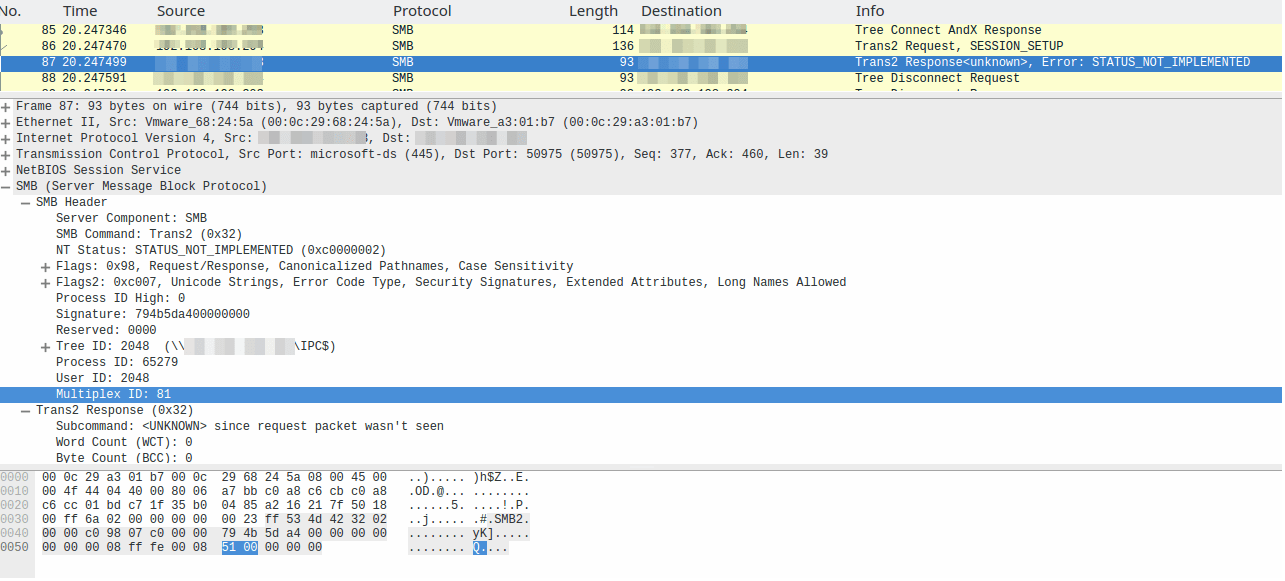
A free tool that can be of use to test whether the computer is in danger with the DoublePulsar backdoor is available here. The test results were obtain on the basis of the response of port 445 to a particular ping. The system running the exploit sends a “trans2 SESSION_SETUP” request to the computer to be test for backdoor presence. The intent of this request is to check if the system is compromising. Infected or not, the system will respond with a “Not Implemented” message. But a “Multiplex ID” is back as part of the message. That is 65 (0x41) for normal systems and 81 (0x51) for infected systems. If a system suffers from infection, then SMB can be a covert channel to exfiltrate data or launch remote commands.
Below image show response of DoublePulsar infected system:
Below image shows normal system response.
Microsoft patched the flaw way back in March 2017 that EternalBlue exploited. MS17-010 – patches a server message block (SMB) server vulnerability present in every Windows operating system. Even patch for the operating systems that had reached EOL like Windows XP and Windows 2003 was also provided by Microsoft. Also, patches for all the other exploits (EmeraldThread, EternalChampion, ErraticGopher, EsikmoRoll, EternalRomance, EducatedScholar, EternalSynergy, EclipsedWing) used by the NSA Hacking tools are also available from Microsoft.
Remediate Vulnerabilities with SanerNow
Try SanerNow free for 30 days – Free Trial