 Fig 1: Image credit: zdnet.com
Fig 1: Image credit: zdnet.com
Armis Security Inc., a cybersecurity firm based in the United States, has discovered five critical Cisco router vulnerability in a networking protocol developed by Cisco. These flaws could enable hackers to target virtually all devices, from data center switches to cameras and IP phones worldwide. These vulnerabilities were disclosed when Cisco released fixes for affected devices. A good vulnerability management tool can solve these problems.
The term CDPwn was coined by Armis to collectively identify the flaws in Cisco Discovery Protocol(CDP). Cisco router vulnerability administrators use CDP across enterprises to identify devices on their networks. These flaws affect those Cisco products which are using the CDP protocol. Vulnerability Management Software can resolve these issues.
The attackers can exploit these newly disclosed vulnerabilities to invade vulnerable Cisco devices. Out of the five vulnerabilities disclosed by Cisco Systems, four are classified as Remote Code Execution (RCE) vulnerabilities, while one is a Denial of Service (DoS) vulnerability that can impact an entire enterprise.
What is Cisco Discovery Protocol?
CDP is a proprietary Layer 2 protocol developed by Cisco Systems. It shares information about connected Cisco devices such as IP Phones or Switches, across an enterprise network. The information which is contained in CDP announcements can vary by the device type and the OS version running on it. It can have the OS version, hostname and IP address from all protocols configured on the port where CDP frame is sent, the port identifier from which the announcement was sent, device type and model, duplex setting, VTP domain, native VLAN, power draw (for Power over Ethernet devices), and other device-specific information.
CDPwn Vulnerabilities:
The following four vulnerabilities are critical RCE bugs, each CVE affecting a different mechanism that parses CDP. An attacker can send a maliciously crafted CDP packet to a target device located inside the Cisco router vulnerability network to exploit the vulnerability.
1. CVE-2020-3119: Cisco NX-OS Software CDP RCE Vulnerability:
Out of the various details shared by the CDP protocol, this vulnerability exploits the power draw (for Power over Ethernet devices) request field in CDP packets. However, to exploit this stack overflow vulnerability, an attacker can send a specially crafted CDP Packet with an increased power level than the one the switch wants. Therefore, a packet containing too many PoE request fields will trigger this vulnerability on affected devices. By exploiting this vulnerability, an attacker could gain full control over the switch and the network composed of different subnetworks or VLANs. This flaw exists because the Cisco Discovery Protocol parser does not check the input for the PoE field in a CDP packet properly.
If an attacker successfully exploits this vulnerability, it could allow the attacker to execute arbitrary code with administrative privileges on an affected device.
2. CVE-2020-3118: Cisco IOS-XR – CDP Format String Vulnerability:
In a CDP packet, many fields are used by the parsing mechanism, and the parser fails to validate string input in those fields. To exploit this vulnerability, an attacker can craft a malicious CDP packet and send it to a vulnerable device. An attacker can edit the format string parameter passed to the sprintf function of the CDP parser. An attacker can edit stack variables using certain format string characters, leading to a stack overflow.
If an attacker successfully exploits, he can cause a stack overflow to execute arbitrary code with the highest privileges on an affected device and can gain full access over a network and its subnetworks.
3. CVE-2020-3111: Cisco Voice over IP Phone – CDP RCE and DoS Vulnerability:
Cisco IP phones also rely on CDP for management purposes such as configuring to the VLAN, a phone should be connected to. The IP Phone can also request specific PoE parameters, and the switch to which it is connected can enable or disable those parameters using CDP.
Port ID field of CDP packet is not validated by CDP parsing mechanism. A stack overflow vulnerability exists in that field’s parsing function, and an attacker can exploit the Port ID field to execute malicious code. While each CDP-capable switch in the network terminates CDP packets, an additional bug exists in the IP phones, i.e., broadcast CDP packets are a usual part of CDP packets.
This flaw allows an attacker to send Ethernet broadcast packets over a network which can cause DoS on vulnerable devices.
4. CVE-2020-3110: Cisco Video Surveillance 8000 Series IP Cameras CDP RCE and DoS Vulnerability:
A heap overflow vulnerability exists in the parsing of CDP packets in the implementation of the Cisco 8000 Series IP cameras. Since the Port ID field of the CDP packet is not validated by the CDP parsing mechanism, an attacker can exploit this by enclosing a very large value to the PORT ID field. On top of it, this heap overflow contains attacker-controlling bytes and can trigger multiple times by an attacker.
To understand what this vulnerability does, we need to understand what ASLR is.
ASLR is a security technique that randomly positions an executable’s base address and the position of libraries, heap, and stack in a process’s address space. Moreover, The random mixing of memory addresses performed by ASLR means that an attacker can no longer know at what address the required code is located.
An attacker can successfully exploit remote code execution since IP Cameras do not use ASLR.
5. CVE-2020-3120: Cisco FXOS, IOS XR, and NX-OS Software CDP DoS vulnerability:
An attacker can cause the CDP daemon in a router to allocate more memory than needed. Since there is no validation method to check memory allocation, it can cause the process to crash. If an attacker repeatedly tries to allocate huge memory than needed, the router in the targeted network will eventually reboot.
If an attacker successfully exploits this vulnerability, he can cause a complete DoS of the target router.
Scenarios depicting how an attacker can compromise and take over a network
Scenario 1 – Breaking of network segmentation
Network segmentation is the practice of dividing an enterprise network into multiple smaller subnetworks, where each division is a network segment. Such a division has many advantages, like improved security, reduced network traffic, controlled environments, and restriction of the risk of any failure to the subnetwork itself. The disclosed CDP vulnerabilities can break this segmented network. The prime devices in any enterprise are routers and switches that efficiently connect devices. And as it turns out, they can also be the most vulnerable assets. Since they contain access to all network segments, they can be is use for unauthorized data access.
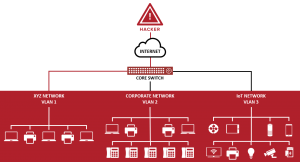 Fig 2: Image credit: armis.com
Fig 2: Image credit: armis.com
Switches handle many link layer protocols which are specific to them. Attack vectors and vulnerability can be severe as they can attack the whole enterprise. Also, most of the port switches, whether in use or not, enable itself by default and can only increase the risk of an attack. CDP is one of the protocols that enable itself by default.
An attacker can gain access to a device that is part of a network segment and can extend the attack to devices connected under the same subnetwork. However, to target devices on different network segments under the same network, an attack has to target the switch to which it connects. Once the attacker has gained access to a switch, he can have lateral access across all devices in a network. A switch can be more of a liability rather than an asset since it’s a relatively insecure device. An attacker can carry a man-in-the-middle attack via a switch. Therefore, Attackers can even hide specially crafted traffic across the switch to monitor or eavesdrop on the Cisco router vulnerability network.
Scenario 2 – Unauthorized data access from devices like IP phones and cameras
This scenario can be present once we have complete access to the network. In order to successfully exploit the Cisco router vulnerability and gain access to IP phones and cameras. Therefore, an attack has to send a specially craft broadcast packet across the entire network and subnetwork, though only Cisco IP Phones and cameras are affecting by this vulnerability.
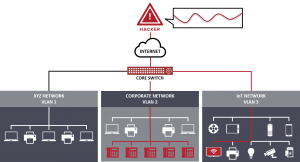 Fig 3: Image credit: armis.com
Fig 3: Image credit: armis.com
Affected Devices:
- Routers:
1. ASR 9000 Series Aggregation Services Routers
2. Carrier Routing System (CRS)
3. Firepower 1000, 2100, and 4100 Series
4. Firepower 9300 Security Appliances
5. IOS XRv 9000 Router
6. White box routers running Cisco IOS XR - Switches:
1. Nexus 1000 Virtual Edge and Nexus 1000V Switch
2. Nexus 3000, 5500, 5600, 6000 and 7000 Series Switches
3. Nexus 9000 Series Fabric Switches
4. MDS 9000 Series Multilayer Switches
5. Network Convergence System (NCS) 1000, 5000, 540, 5500, 560 and 6000 Series
6. UCS 6200, 6300 and 6400 Series Fabric Interconnects - IP Phones:
1. IP Conference Phone 7832 and 8832
2. IP Phone 6800, 7800, 8800 and 8851 Series
3. Wireless IP Phone 8821 and 8821-EX
4. Unified IP Conference Phone 8831 - IP Cameras:
1. Video Surveillance 8000 Series IP Cameras
Solution
Updates for all the above-disclosed CVEs are available on the Cisco Security Advisory page. Since CISCO already provides updates to fix the vulnerabilities, installing them and safeguarding the networks against emerging threats is highly advisable.
