BitPaymer/IEncrypt campaign has been targeting various public and private sector industries spread across the U.S. This campaign uses spearphishing emails as its initial infection vector and delivers Dridex malware. BitPaymer/iEncrypt ransomware is known to encrypt data, apps and program files on the target machine. Therefore, Vulnerability management system can resolve these issues.
The campaign utilized an unquoted service path vulnerability in Apple iTunes. The vulnerability resides in Apple Software Update utility. Apple iTunes is obsolete on the new MacOS Catalina and is therefore not vulnerable. However, all the Windows machines running Apple iTunes and iCloud were open to attack.
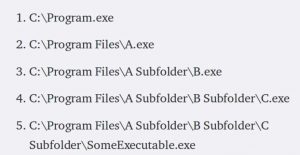
An unquoted path vulnerability is a simple flaw where a path to an executable contains spaces and is not enclosed in quotations.
C:\Program Files\A Subfolder\B Subfolder\C Subfolder\Executable.exe
In such a case, the system interprets the path as shown below:
This allows an attacker to place a malicious executable in any folder or sub folder and execute it with SYSTEM privileges.
The major matter of concern here is that even when iTunes is uninstalling. Apple continues to run on the installed machine and requires a separate procedure to remove it. This vulnerability readily assists attackers in evading detection by security solutions. Most of the products are based on behavioral monitoring of the parent-child process on systems. And when a legitimate process signed by a trusted vendor such as Apple executes a malicious child process, the risk rating given by AV products is low.
security updates(detailed in our blog). For iCloud and iTunes for Windows last week. We hereby issue a gentle reminder to system administrators for applying these security updates on priority to prevent any instances of active exploitation.