Do you believe you’re dealing with vulnerabilities correctly? When you run a scan and report a few new vulnerabilities that are unaddressed for longer than 90 days, you’ll try to prioritize them rather than new ones. What if those old vulnerabilities don’t pose more risk than the new vulnerabilities? That’s where choosing the right metrics comes in handy. This process is simplified with a vulnerability management tool.
Metrics play a vital role in measuring your organization’s success. Knowing what percentage of devices your organization regularly scans with a vulnerability management software is always beneficial. Before proceeding further, we must first understand what Vulnerability Management Metrics mean.
What are Vulnerability Management Metrics?
As we know, vulnerability refers to a weakness or flaw attackers can exploit on devices to launch an attack. It can be any software bug or inadequately secured firewall rule. Managing vulnerability becomes overwhelming and tedious for security admins. So it becomes essential to measure parameters that could help detect vulnerabilities and assess their impact on overall risk to organizational security. Security admins can monitor many vulnerability management metrics to understand their vulnerabilities better and make their job less complex by utilizing a vulnerability management software.
Why do We Need to Manage Vulnerabilities?
Cybercriminals are lurking all over the internet, waiting for the opportunity to sneak around and get your organization’s information. When you consider why vulnerability management is essential, the first thing that should come to mind is keeping your network safe from known exploits. Attackers will look for new vulnerabilities in your system that could potentially lead to the theft of sensitive data and old vulnerabilities that have not been patched yet.
As a result, having an effective vulnerability management platform that can detect, evaluate, remediate, and report vulnerabilities is critical. We’ll now look at the metrics you can use to manage vulnerabilities more accurately.
The top 12 Vulnerability Management Metrics are:
1. Device Coverage:
The most crucial vulnerability management metric is scan coverage. To measure which devices are getting scanned, the organization scans them. We usually ignore scanning when we add only a few new devices to the organization. It usually happens because you don’t want to scan them for long, as vulnerability scans take forever. But, it’s essential to make sure that the scanner covers all devices for vulnerabilities.
2. Time For Detection:
It specifies the amount of time required to discover a known vulnerability. When we find a new vulnerability, we need to determine how long it will take for our application to detect it, whether it’s months, weeks, days, or hours. The smaller the time difference, the better. Reduce the time difference by using a vulnerability management software.
3. Time For Remediation:
After finding the vulnerability, we must address it. The longer it takes to resolve, the more prone to attacks it becomes. Hence This is one of the reasons to have vulnerability management metrics.
4. Number Of High Critical Vulnerability:
Critical vulnerabilities are always dangerous, so it is advised to treat them first even though you have other less-critical vulnerabilities pending to be treated.
5. Frequency Of Scan Coverage:
This measure indicates how frequently scans occur. Regularly performing scans is necessary for the organization to ensure they don’t miss any high-risk vulnerabilities.
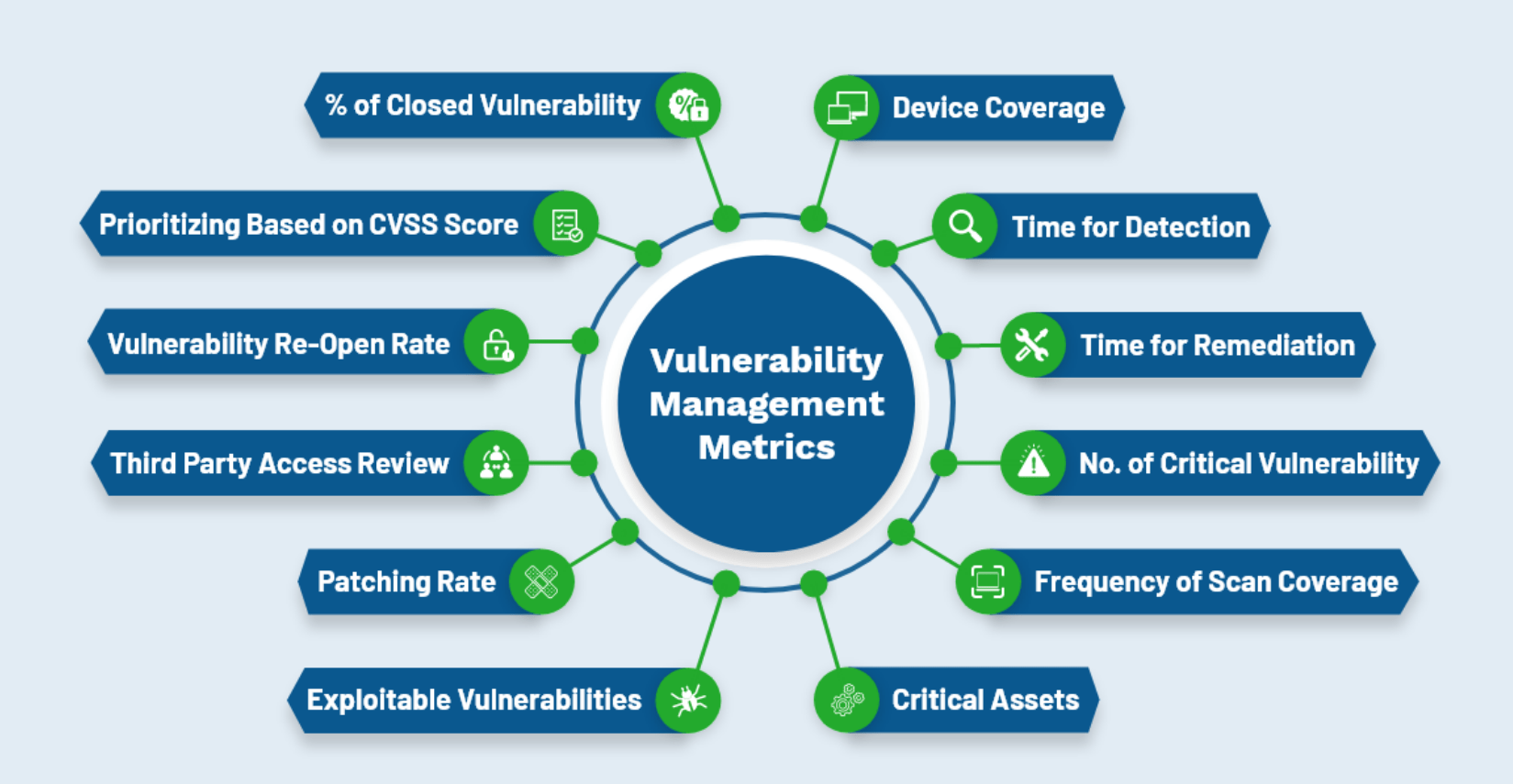
6. Patching Rate:
Patching has always been an essential aspect of cyber security; it is a procedure that involves adding patches (updates) or upgrading to newer versions to address security flaws. The admin applies patches, and this metric shows the number of patches applied and the time taken to apply each patch.
7. Third-party access review:
Certain accesses would’ve been given to third parties to complete an activity; we must ensure that access is stopped after they meet their service.
8. Vulnerability re-open rate:
There are occasions when vulnerabilities reappear after being discovered and treated. It simply indicates how ineffective the remediation was; consequently, it is critical to track the re-open rate and identify ineffective remediation with a vulnerability management tool.
9. Prioritizing based on CVSS score:
CVSS (common vulnerability scoring system) is an open framework that measures the characteristics and severity of the vulnerability. It additionally helps in prioritizing the high-critical to low-critical exposure.
10. Percentage of closed vulnerability:
We must determine if the remediation was successful after we find and remediate vulnerabilities. Keeping a database of closed vulnerabilities allows us to identify devices that are free of vulnerabilities and ensures that our remediation is effective.
11. Exploitable vulnerability:
Vulnerability management metrics measures the ease with which a vulnerability can be exploited in a target device. This exploitation can be resolved by using a vulnerability management tool.
12. Critical assets:
Any resource, product, or gadget that is valuable to an organization is classified as a key asset; it can be a confidential database or financial report. The assets team would identify and place these assets in the assets inventory, then determine the most critical assets and apply appropriate security controls.
Why Vulnerability Managmeent Metrics Critical?
- Visibility: Have clear picture of enterprises IT network that helps ITsec teams to have comphrensive understanding of all risks allowing for more informed decision making capabilities.
- Prioritization: With metrics, enterprises prioritize remediation efforts based on risk levels, ensuring that the most critical vulnerabilities are addressed first.
- Tracking Progress: Metrics enable teams to measure the effectiveness of their vulnerability management efforts over time.
- Continuous Improvement: Regularly analyzing vulnerability metrics can highlight trends and areas needing improvement.
Use SanerNow to Automate Your Vulnerability Management Metrics
With its well-known SCAP feed of over 175,000+ vulnerability checks, it is the industry’s fastest, fully integrated tool. Therefore You no longer need to be concerned about the never-ending scans. Isn’t it amazing that SanerNow can do it in just 5 minutes?
It’s easy to know the percentage of critical vulnerabilities, high-fidelity attacks, top remediation, vulnerable devices, and much more in one dashboard. Explore SanerNow vulnerability management by scheduling a Demo, or you can also start your free trial.


