What were the biggest culprits and causes of cyberattacks in the past few years? CVE or software vulnerabilities are the usual suspects, but other security risks being exploited are on the rise and vulnerability management tools are struggling to keep up. It is a trend you must be observing too. The key type of security risk seeing a significant rise is misconfigurations in your security controls, giving away easy backdoor access to hackers and threat actors.
Reducing potential threat vectors from these misconfigurations can be simpler than you think. So, are your security controls functioning correctly?
If not, let’s fix it!
Security Controls: A Brief Dive
What are Security Controls?
Let’s understand the basics. Security controls are critical functions and mechanisms in your IT network’s devices that are used to protect and prevent cyberattacks. They typically include both physical and technical controls, but in this blog, we will be talking about technical controls alone.
Security controls include access controls, firewalls, multi-factor authentication, password policies, vulnerability detection, patch management, etc., that can play a critical role in securing the organization from potential cyberattacks.
Why are they important?
Security controls can play a significant role in a wide variety of protection functions. Be it data security, endpoint security, confidentiality, or continuity of process, security controls have a significant impact on their functioning.
Another critical use case of security controls is in enforcing compliance. Most compliance policies provide strict regulations on how security controls must be, making it vital for IT and Security teams.
Further, security controls are critical in creating a resilient and secure IT infrastructure and preventing potential loopholes that could lead to cyberattacks.
The Consequences of Improper Security Controls
The most obvious consequence of improper security controls is a cyberattack. Since security controls take a significant percentage of your organization’s IT security posture and could leave a gaping hole for cyber-attackers to intrude.
Further, improper security controls directly lead to failure in the enforcement of compliance policies. This, in turn, can affect the reputation, business, and the overall organization’s security.
Adding to the list is the impact on the operational continuity of the organization from improper security controls. As a result, operational disruption becomes a direct consequence that affects the business and can lead to a rise in costs for the organization.
Check if your Security Controls are Functioning Properly: The SanerNow Way
If security controls are so critical, how do you check if they are functioning properly? How do you make them function correctly? Let’s find out!
SanerNow Advanced Vulnerability Management is a premier cyberattack prevention solution that can help you enforce proper security controls and help prevent cyberattacks effectively.
With a combination of its 7 modules, SanerNow provides complete vulnerability management capability for modern IT and Security teams. With integrated vulnerability detection, assessment, prioritization, and remediation, SanerNow takes your vulnerability management to the next level.
Talking about security controls, the following SanerNow modules provide you with complete control over the functioning of security controls:
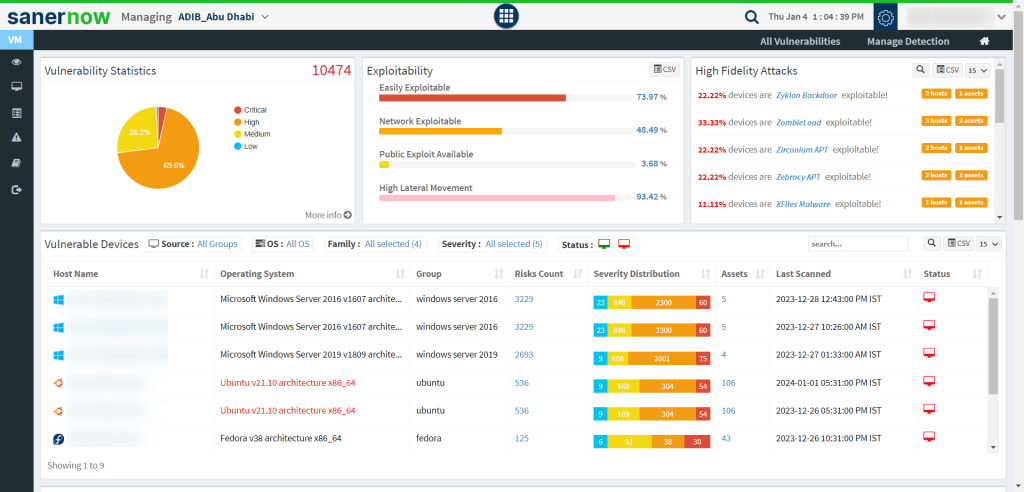
- Vulnerability Management: Vulnerability detection is a critical security control that every IT security team needs, and SanerNow VM can detect security risks like CVES, misconfigurations, posture anomalies, and other security risks. It also provides you with a complete overview of the risks present in the network.
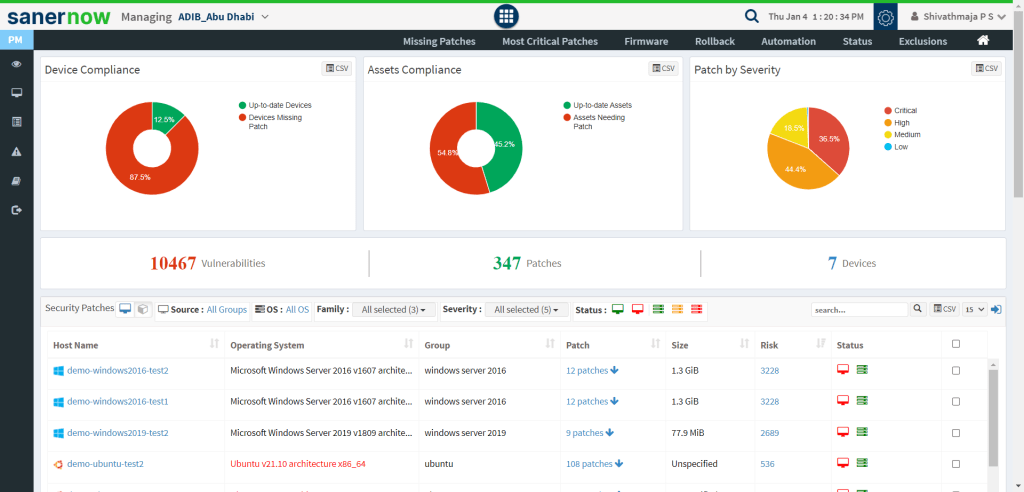
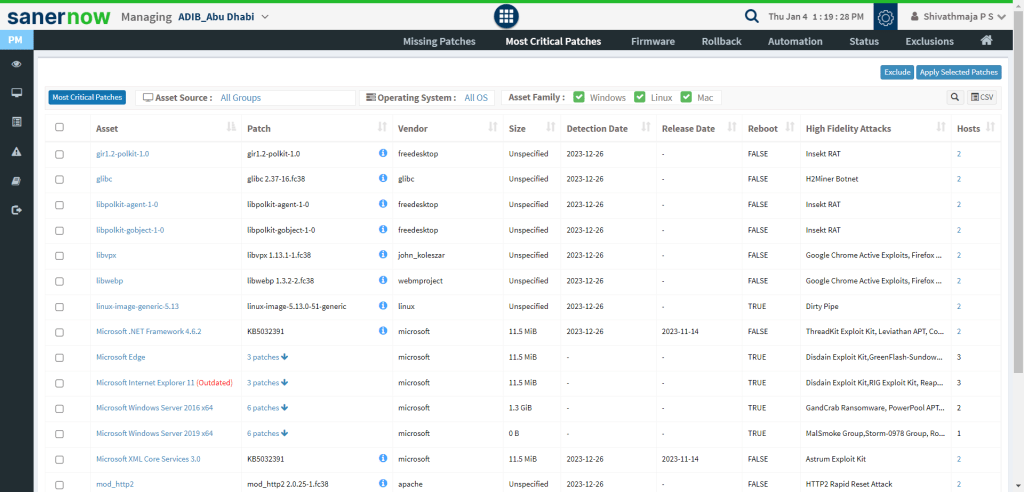
- Patch Management: Vulnerability mitigation is another critical security control that needs to be effectively performed. SanerNow PM gives complete details of missing patches, critical patches, and other info based on every asset and allows you to have granular control over the application of the patches.
- Compliance Management: SanerNow’s compliance management module covers a large portion of security controls that are typically included in common security policies. Additionally, controls like access control, network management, password policy and more can be found and can be managed and modified here.
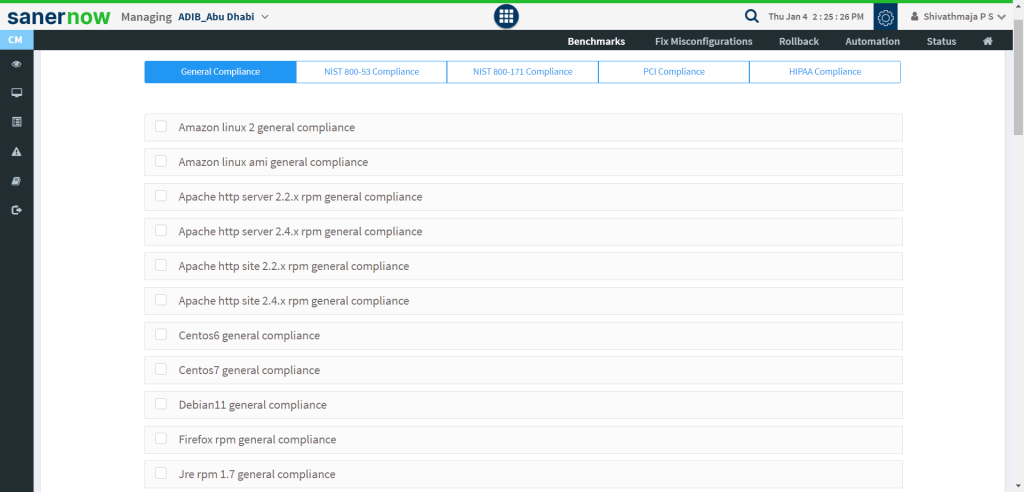
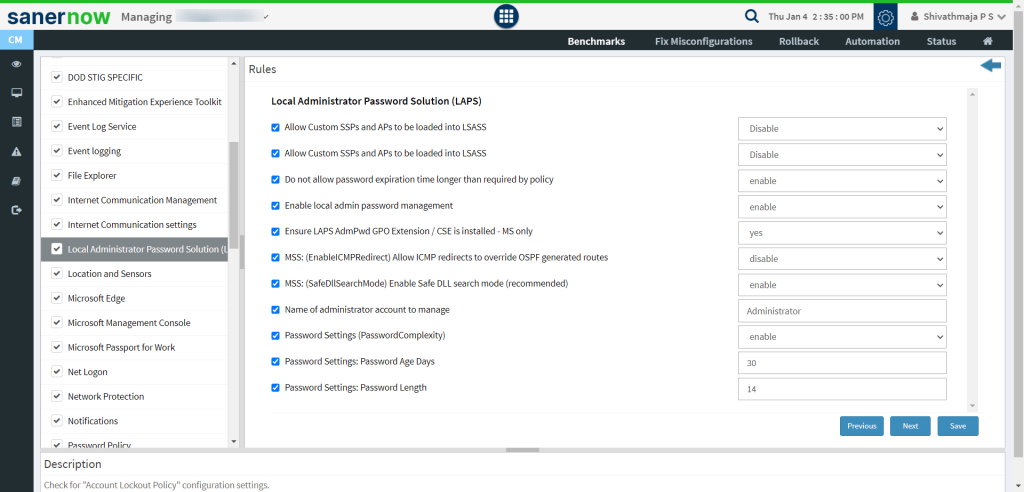
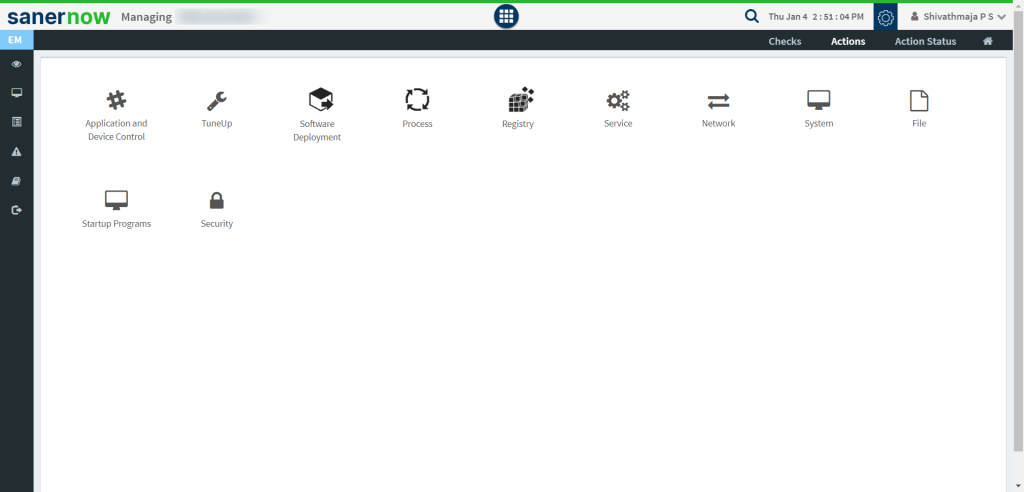
- Endpoint Management: SanerNow’s Endpoint Management module gives complete management of more than 100+ security controls that go beyond patching or vulnerability management. From application and device control to managing services and more , the endpoint management module completes the security control coverage of SanerNow.
Conclusion
Prevention of cyberattacks is an organizational imperative and should take the forefront, not be an afterthought. This change in how we approach IT security can completely transform your organization’s security posture for the better.
Further, security controls are a must for every IT and Security team looking to minimize the attack surface and effectively combat cyberattacks. However, a good vulnerability management tool that can help you properly enforce and configure your security controls can give you a much-needed security boost.