This month’s Patch Tuesday marks a significant start to the year, with Microsoft delivering a heavy volume of updates to address 114 vulnerabilities. This includes 3 zero-day flaws, one of which is actively exploited.
The sheer volume, doubling the count from last month, highlights the importance of a rapid deployment cycle for IT teams this January.
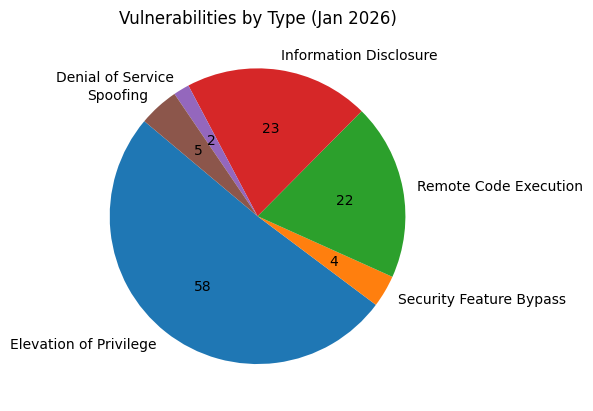
Vulnerability Breakdown
Here is a breakdown of the 114 vulnerabilities addressed in the January 2026 update:
Vulnerability Highlights: Three Zero-Days
This month is particularly high-risk due to three zero-day vulnerabilities, meaning they were either publicly disclosed or actively exploited before a patch was available.
CVE-2026-20805: Desktop Window Manager (Info Disclosure)
- Overview: A vulnerability in the Windows DWM component that organizes how application windows appear on screen.
- Risk: Although rated as Info Disclosure, it is actively exploited to leak memory addresses, which enables attackers to bypass security protections such as ASLR for multi-stage attacks.
CVE-2026-21265: Windows Secure Boot (Security Feature Bypass)
- Overview: A vulnerability related to expiring Secure Boot certificates from 2011.
- Risk: This flaw could allow an attacker to bypass Secure Boot integrity checks. This patch rotates the expiring certificates to ensure boot security is maintained.
CVE-2023-31096: Agere Soft Modem Driver (Elevation of Privilege)
- Overview: A legacy driver vulnerability that was publicly disclosed.
- Risk: To mitigate risk, Microsoft has officially removed these legacy drivers (agrsm64.sys) from the Windows operating system in this update.
Critical Vulnerabilities: Deep Dive
| CVE ID | Impacted Component | Description |
| CVE-2026-20854 | Windows LSASS | A critical network-based flaw that allows an unauthenticated attacker to execute code remotely by sending malicious packets to the LSASS service. |
| CVE-2026-20944 | Microsoft Word | This vulnerability permits arbitrary code execution if a user opens a specially crafted Word document, typically delivered via phishing. |
| CVE-2026-20952 | Microsoft Office | A high-risk “Use-After-Free” bug that can be triggered through the Office Preview Pane, allowing code execution without direct user interaction in some cases. |
| CVE-2026-20955 | Microsoft Excel | A pointer handling error that enables attackers to execute commands on a victim’s machine when a malicious Excel file is opened. |
Affected Products & Scope of Update
The January 2026 update is comprehensive, impacting a wide array of Microsoft’s ecosystem:
- Core Operating System: Windows 10, Windows 11, and Windows Server (2019, 2022, 2025).
- Development Tools: .NET, Visual Studio, and Azure DevOps Server.
- Database & Productivity: Microsoft SQL Server and Microsoft Office.
- System Components: Windows Kernel, Windows Installer, and the Cloud Files Mini Filter Driver.
- Browsers: Microsoft Edge (Chromium-based).
The diversity of these fixes, ranging from kernel-level drivers to user-facing applications like Office, means that almost every Windows-based environment (on-premise or cloud) is affected.
What You Should Do
- Prioritize the Active Zero-Day: Immediately deploy patches for CVE-2026-20805. Because it is already being used in attacks, this should be the top priority for all systems.
- Apply OS-Level Patches First: Given the two publicly disclosed elevation of privilege flaws in the Kernel and Installer, focus on updating Windows client and server operating systems.
- Validate Critical RCE Fixes: With 31 RCE vulnerabilities addressed, ensure that systems exposed to the internet or untrusted networks are updated to prevent remote code execution attacks.
- Audit Server Environments: Don’t forget infrastructure-specific updates, particularly for SQL Server and Azure DevOps Server, which often require specialized maintenance windows.
- Review Defense-in-Depth: Beyond patching, monitor for unusual local privilege escalation attempts and ensure that the Principle of Least Privilege (PoLP) is strictly enforced to mitigate the impact of any potential breach.
Instantly Fix Risks with Saner Patch Management
Saner patch management is a continuous, automated, and integrated software that instantly fixes risks exploited in the wild. The software supports major operating systems like Windows, Linux, and macOS, as well as 550+ third-party applications.
It also allows you to set up a safe testing area to test patches before deploying them in a primary production environment. Saner patch management additionally supports a patch rollback feature in case of patch failure or a system malfunction.
Experience the fastest and most accurate patching software here.

