Attackers are continuously looking for new vulnerabilities to take advantage of. They easily exploit the ones that are not remediated and the ones that are still prevalent among the endpoints. At the same time, we come across various tools and strategies to execute Vulnerability Management. Therefore, it is essential to understand about Vulnerability Management database in extensive detail. Having a vulnerability management framework with a comprehensive and is crucial. Regularly check for new vulnerabilities to prevent cybersecurity breaches and reduce attack surfaces. While choosing a vulnerability management tool, understand the importance of a SCAP feed.
What is a vulnerability database?
A vulnerability database results from an effort to collect information about all the known security flaws in software. The database aims to maintain, collect, and disseminate information about discovered computer security vulnerabilities. The database conventionally describes the identified vulnerabilities. It also assesses the potential impact of affected systems and provides any updates or workarounds to mitigate the issue. The database assigns a unique identifier to each vulnerability found. It is either numeric or alphanumeric. The database information is accessible through web pages, API, or exports. However, having a vulnerability management software is important.
Opensource vulnerability databases: Are they effective?
There are various open-source vulnerability databases available in the market. However, a few well-known open-source databases include NVD, Issue trackers, OSVDB, and Security Advisories. Even though these databases produce collective information of vulnerabilities, they still come with a set of challenges. If an open-source database detects a vulnerability, and the same is patched, the vulnerability might still be accessible to the attackers who may use it to their advantage.
Continuously monitoring the open-source vulnerability databases and merging them with your vulnerability management program is not easy. It delays the whole vulnerability management process. These databases also produce a scattered view of vulnerabilities that are not in one place. Open source is chaos. It has no rules or support to dictate one strict line of vulnerabilities publication.
Hence we recommend you have a well-built vulnerability database integrated with your vulnerability management tool. With this, you can get better visibility over your vulnerability exposure. You can also plan on quick remediation measures.
Things to look out for in your vulnerability management database
The vulnerability management program chosen by any organization has to do two things: First, find any critical vulnerabilities. Second, Fix them by patching them automatically. It is a boon if the program can prioritize the vulnerabilities, patch them based on risk levels, and provide visibility into the organization’s security posture. For a Vulnerability management program to be able to do all these, the database has to be extensive. It must also be capable of identifying even the most minor vulnerability exposure. Here are few things you have to look out for in your vulnerability database:
The number of vulnerabilities supported: More the number of vulnerabilities, the better the chances of detecting anything vulnerable in the network. As the Vulnerability management database grows in size, it is almost effortless for the IT teams to discover all types of vulnerabilities.
Immediate availability of latest updates: It should be up-to-date with information on the latest vulnerabilities. Detects Numerous vulnerabilities every day. Hence it is critical to discover a vulnerability immediately to prevent any exploits and reduce the risk exposure.
SecPod SCAP Feed, the world’s largest vulnerability database in action
Having understood the importance of a comprehensive vulnerability database thoroughly, SecPod has invested a lot of resources over many years in security research intelligence. SecPod has been a predominant SCAP feed vendor for more than a decade and has built the world’s largest vulnerability database with over 130,000+ checks. In addition, the SecPod SCAP repository offers a natural language-based search interface to extract security information.
SecPod keeps multiple sources of security content into one repository providing CPE, CVE, CCE, OVAL, CWE, CESS, and XCCDF information. This repository is easily integrated into the SCAP solution through a set of web service interfaces. This repository also provides a natural language-based search for security content.
Vulnerability Database work with the scanner?
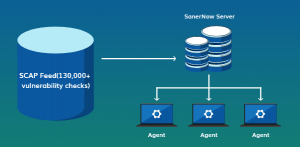
SanerNow’s vulnerability management application works on the Agent-Server model. The SanerNow Server hosted on the cloud is in continuous syncs with the SCAP feed to get information on the latest vulnerabilities. These vulnerability details are passed on to the agent present in the endpoints for further scanning and detection.
The agents installed in the endpoints receive all vulnerability management tasks from Server. Tasks from running vulnerability scans to remediating vulnerabilities with relevant patches. These tasks are executed silently on the endpoints without disturbing the users. This agent is set in a live connection with the Server to help execute any on-demand or real-time vulnerability management tasks.
Key Highlights of SecPod’s vulnerability database:
-
-
- Extensive Coverage – Provides CVEs and CCEs for various penetrating systems, servers, applications, networks, and mobile devices.
- Professional Quality – The content has been developed professionally and is tested for security.
- Vast Target – Has broad content coverage for operating systems, enterprise servers, applications, networks, and mobile devices.
- Daily Update – Offers daily release and is in sync with product’s repository.
-
SecPod Vulnerability Management distinctive features –
-
-
- Precise detections Continuous Scans – Lightweight agents installed at endpoints continuously monitor systems to detect risks and vulnerabilities with limited bandwidth consumption accurately.
- Rapid Scans – Detect the vulnerabilities in less than 5 minutes with a comprehensive and rapid scanner.
- Integrated Patch Management – Taking an integrated patch management approach to identify, prioritize and remediate vulnerabilities instantly from the SanerNow dashboard.
- Largest Vulnerability Database – SanerNow leverages this vulnerability database and detects vulnerabilities in the endpoints accurately.
-
To watch SanerNow’s vulnerability management capabilities in action, sign up for a demo today.
To get information on the Top Vulnerabilities of 2020, download this report.
Link – https://marketing.secpod.com/top-vulnerability-report-2020