A simple message on a secure(*cough) internal channel saying YOU HAVE BEEN HACKED is a terrifying nightmare for all employees, especially security teams, in an organization. But that’s what happened to Uber, the ride-share giant. Again! called the Uber attack. An attack like this should be detected by a vulnerability management solution.
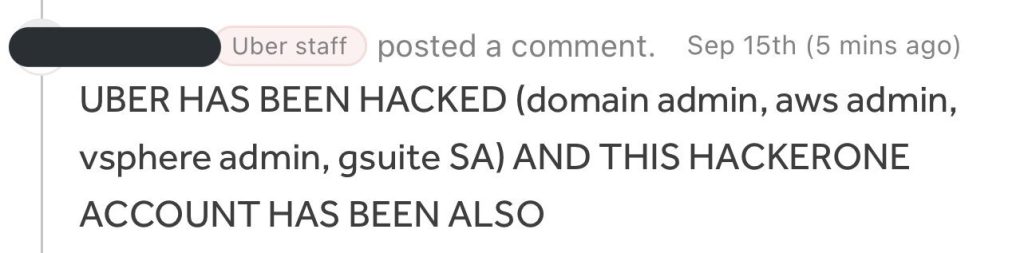
On September 15th, messages on Uber’s internal Slack and HackerOne channels from a staff account announced the entire network infrastructure of the company compromised. The employees clearly thought it was a joke, but this soon snowballed into widespread chaos, as messages from the IT team asking not to use the channels basically confirmed it. This is why a patch management solution is required.
Backgrounds of Uber attack:
This isn’t the first time, however. In 2016, Uber’s network, with sensitive user data stolen and a ransom of 100,000$ paid to cover it up. After investigations, the ex-CISO of Uber is under trial for the alleged cover-up.
But more importantly, this alleged breach was a social engineering operation by an 18-year-old (not confirmed) who also seems to have some connection with another recent leak of Rockstar Games. And funnily enough, they also used Uber’s own HackerOne accounts to send out emails that contained their telegram handle. Soon, they also explained their modus operandi, on how they breached the ride-share giant.
More importantly, how weak was the organization’s cyber-defense if a simple social engineering attack could breach the entire network? Or was it Uber’s blunder that caused its downfall?
The Anatomy of Uber Attack
How and when did it happen?
-
- The point of attack: The 1st step of every cyber-attack is gaining access to an organization’s network with user credentials. In the case of Uber, two possibilities talked about.
-
-
- A social engineering attempt on one of Uber’s employees led to the threat actor accessing the organization’s VPN and entering its network.
- But another theory floating on the internet suggests the threat actor bought a set of user credentials from an underground marketplace. This was confirmed by an investigation conducted by Group_IB, a renowned group of cybersecurity researchers.But even with MFA enabled, how did the hacker get access to the network?
- The double door breach:
Multi-factor Authentication ensures that leaked credentials don’t lead to breaches. So, even with the user’s credentials, only if the user approved a push notification would the threat actor get in.But even with MFA, all the hacker had to do was repeatedly harass the user by bombarding them with WhatsApp messages to authenticate the login request. This process of repeatedly spamming users to authenticate MFA is called MFA Fatigue. And the threat actor impersonated an IT team member requesting the user to authenticate it. It was a textbook social engineering-initiated breach.
The threat actor was in. - Uber’s ‘uber’ mistake:
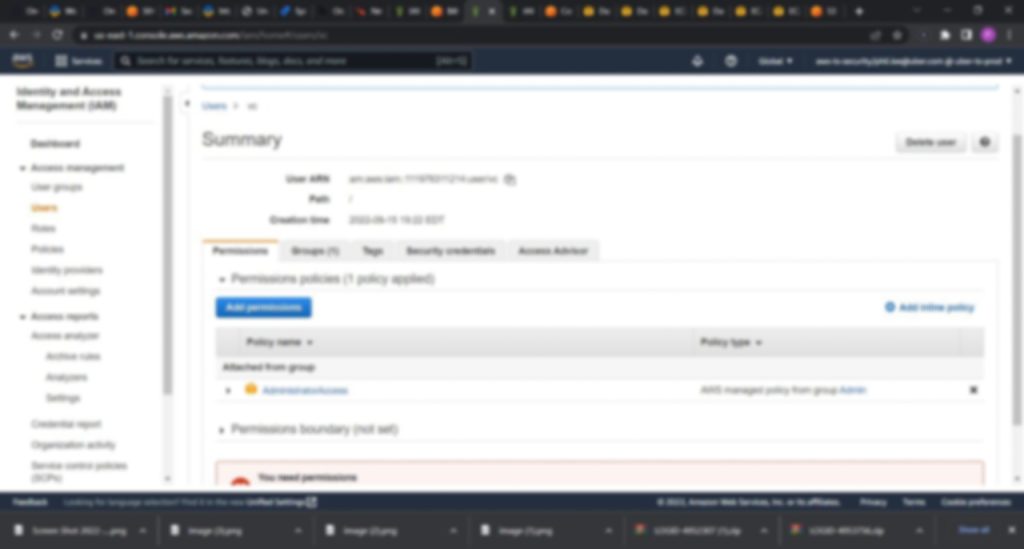
Once the network compromised, the hacker was inside the VPN and had access to everything a typical employee with basic access would have, but Uber had committed a blunder.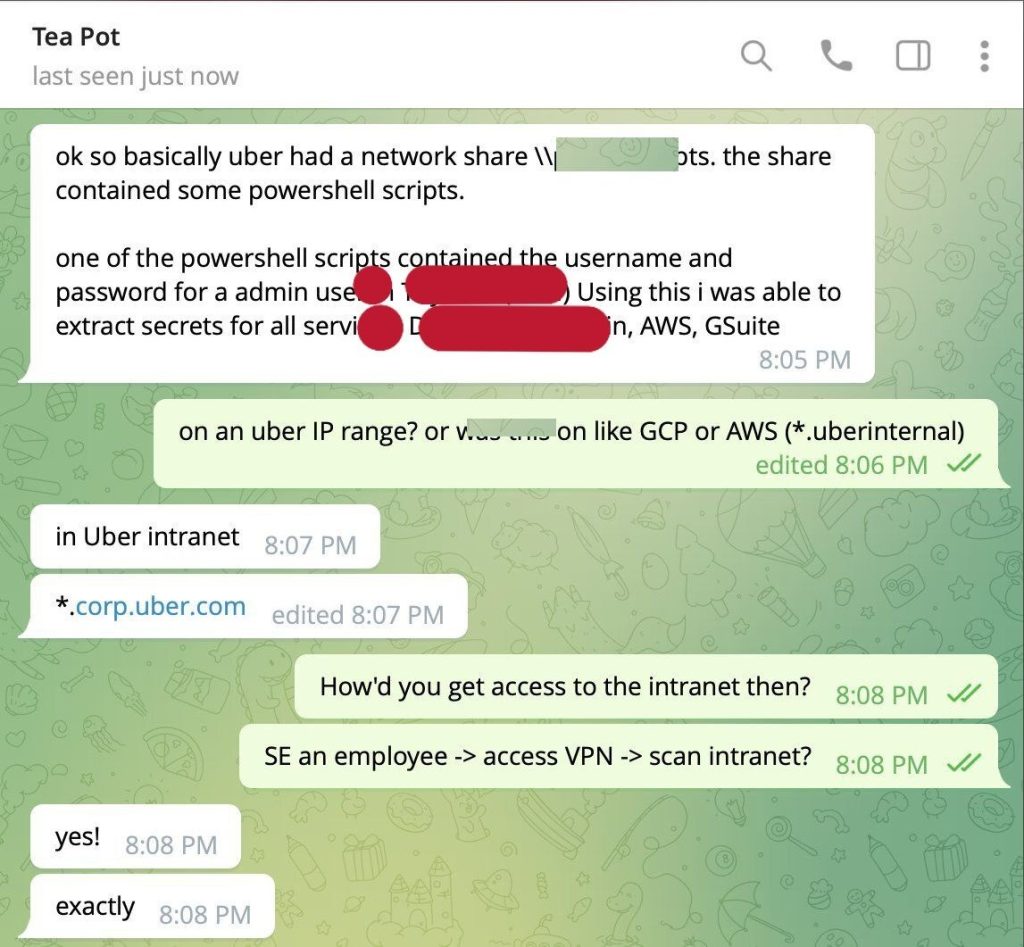
Uber, in its internal network-shared drive space, had stored a few PowerShell scripts that contained a hard-coded username and password for an admin user in Privilege Access Manager (PAM).
In simpler terms, Uber had basically stored the user credentials of an administrator that had access to everything and controlled the access for anyone as well. This meant the threat actor gained access to literally everything in the organization’s network. All in one single swoop.
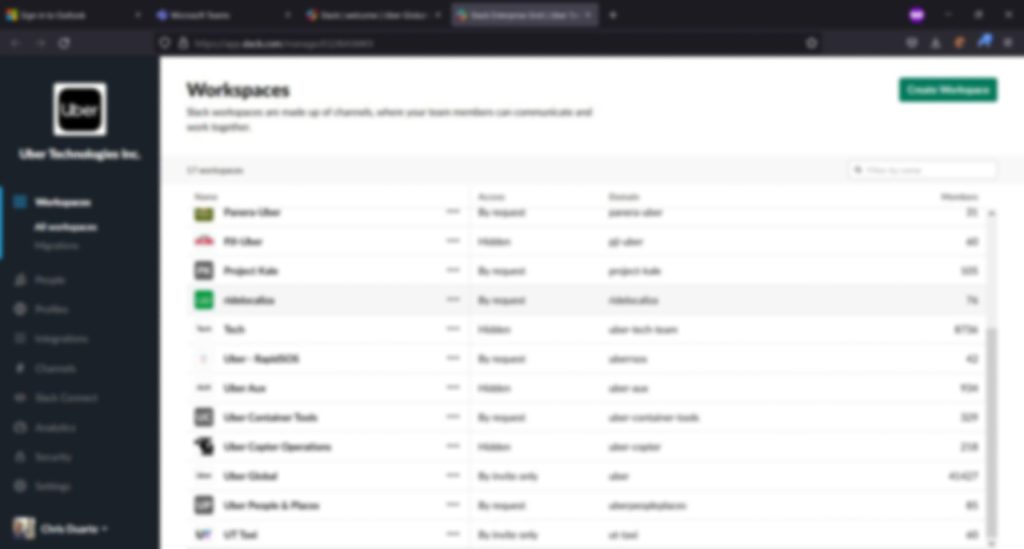
This included
– Slack Workspaces
– Google Workspace Admin
– AWS Accounts
– HackerOne Program
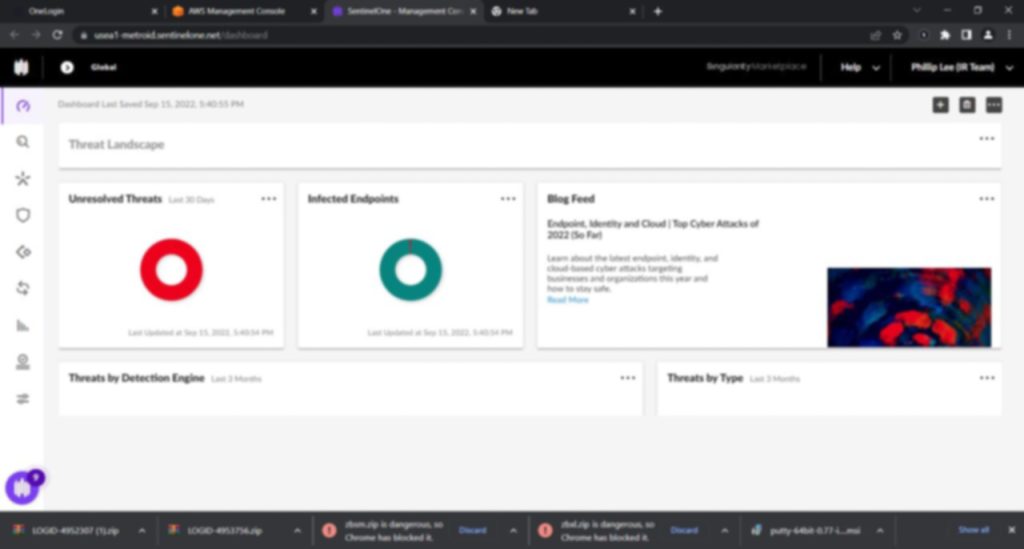
– SentinelOne EDR
– vSphere Dashboard
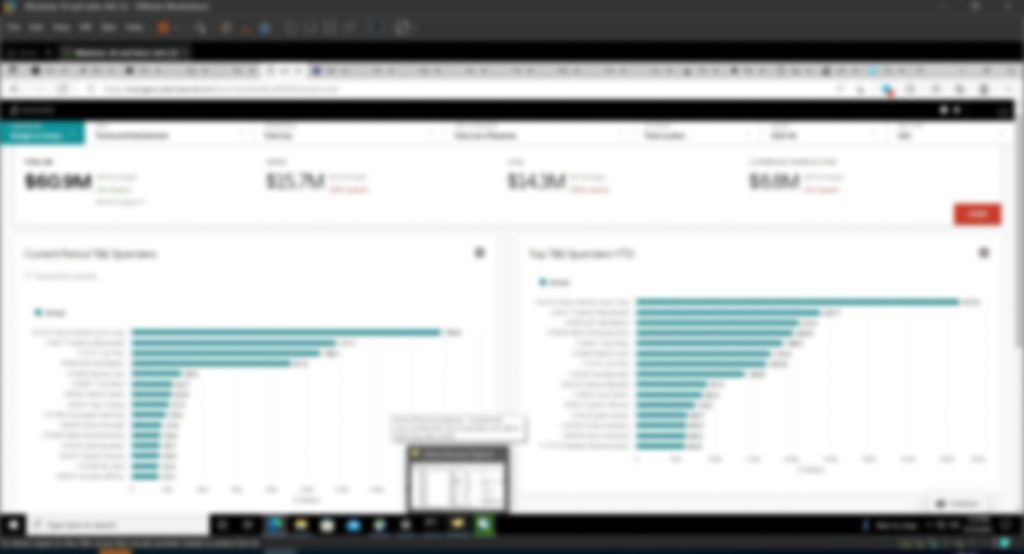
– Financial Dashboards - The Fallout:
And soon enough, the news spread like wildfire when the screenshots of Uber’s internal financial records and more were out in public. The hacker had also made their telegram user-handle public, and conversations about how they performed the attack were also out in public.
-
With the recent tweet and announcement from Uber’s official channels, the worst confirmed.
Questions asked, explanations made, fingers pointed, and lessons learned.
Are People the Ultimate Cyber-risk?
Are people of an organization the biggest cyber risk? Social engineering (SE) is the simplest and, unfortunately, the most effective way through which threat actors get into an organization. SE is fairly common, and combating it, especially in huge organizations, is increasingly difficult.
So, to combat the aftermath (or to respond to the incident) and minimize its effects is why we have user access control and privilege management.
But storing user credentials, especially of high-access admins, is incredibly dangerous and, frankly, a rookie mistake on Uber’s part. With sensitive info stored carelessly, it becomes ridiculously easy for threat actors to exploit networks. And that’s exactly what has happened.
People aren’t the biggest cyber risk, but they are the gateway for every other risk to become dangerous.
The Blame Game
So, who’s to be blamed here? The user who was socially engineered or the person or people responsible for the blunder of storing admin credentials?
It’s a question that’s very difficult to answer without knowing the entire picture. While both are responsible for the end result, the damage would greatly minimized if the right measures for storing sensitive information taken.
A lot of cybersecurity frameworks and policies explicitly suggest not storing admin credentials, and they do so for a reason.
So, what does it mean to you & us?
The Uber attack will have ramifications, and the impact will be long-lasting. However, lessons learned, and better measures to prevent such attacks. Or someone else will learn it the hardway.
Had the organization followed a strict cybersecurity framework, proper vulnerability management, and attack surface reduction, this article would not be written.
If the organization trained its employees against social engineering attacks, the chance of a cyberattack occurring would have been significantly lower.
Had enough care taken in storing sensitive user credentials, the damage would much lesser.
But these are the lessons for us to learn from the attack and its aftermath.
Conclusions:
The Uber attack will be an eye-opener for organizations, CISOs, and their teams throughout the world. Even with great cyber-defense and MFA, simple mistakes can simply breach their organization by simplifying the work for the threat actor.
Cybersecurity best practices can go a long way in ensuring such attacks do not occur.
But for Uber, only time will tell how everything else plays out.
Screenshots Credits: vx-underground