“The perfect kind of architecture decision is
the one which never has to be made” – Robert C. Martin.
While building the SecPod architecture, our prime intent was to support the transfer and storage of enormous data points.
An account in SanerNow contains a collection of devices – segregated into groups based on device characteristics. This trait of the SanerNow Server helps administrators to take collective actions. SanerNow starts with discovering devices in the organization’s network and installing agents on these devices using one of the many deployment options available.
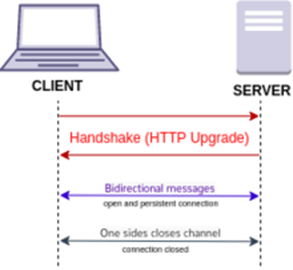
The agents are connected to the server and communicate in real-time using a web socket over HTTPS. An alternative communication between agents and the SanerNow server using a polling mechanism is also available. This configuration ensures that no outbound port other than 443 is utilized for communicating with the server. In an organization, 443 is often an allowed outbound port; hence security administrators can be assured that no extra port is open or needs approval.
The communication from the SanerNow server is digitally signed and verified by the agent on the endpoints to prevent man-in-the-middle attacks. Similarly, the agent authenticates with the server using a SAML key unique to every agent; this helps the SanerNow server uniquely identify agents and send detection and response scripts applicable to the devices. The SanerNow Agent authentication sequence is depicted below,

100+ pre-built detection scripts help discover interesting facts about the device. Some of the examples are the presence of potentially unwanted programs, sensitive data stored as plain text, a system up-time of more than seven days, diminishing disk space, security and non-security patches to be installed, installed applications with an unknown publisher, numerous open ports, BitLocker status, gatekeeper settings, etc.
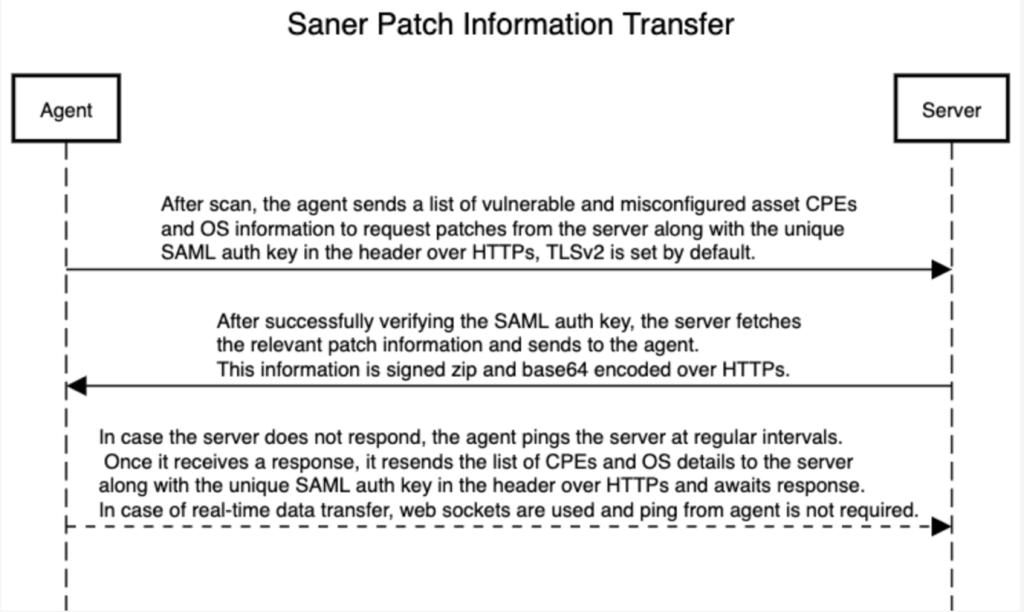
On discovering such security concerns, you can take timely actions such as block/uninstall unwanted applications, delete a file, encrypt the disk, reboot devices, system clean-up, install patches to prevent attacks, deploy trusted software, stop a process, set BitLocker and gatekeeper settings, and ensure proper DEP and Firewall configuration on a device. A security patch information transfer is depicted below,
Along with SanerNow’s robust CVE (Common Vulnerability Enumeration), SVE (SecPod Vulnerability Enumeration), and MVE (Malware Vulnerability Enumeration) based vulnerability prioritization, mitigation, and compliance with Patching capabilities, the ability to talk to a device and respond to security concerns in real-time provides advanced vulnerability management capabilities to your organization. With the upcoming addition of new products in the roadmap, SanerNow architecture does not undergo major changes, thus offering a stable platform for many value-added features for the customers.