This April another big update from Microsoft, which includes 11 security bulletins addressing a total of 26 vulnerabilities. The high priority fix is for Microsoft Office addressing 5 vulnerabilities, Windows HTTP protocol stack (HTTP.sys) and Internet Explorer addressing 10 vulnerabilities.
This month four bulletins are rated as Critical, addressing 17 vulnerabilities and seven are rated as Important.
Critical security updates addresses security issues in Internet Explorer 6 to Internet Explorer 11, Microsoft Office, Windows HTTP protocol stack (HTTP.sys) and Microsoft Graphics Component. All of them potentially allow Remote Code Execution.
The other seven important security updates address issues in Microsoft SharePoint Server, Windows Task Scheduler, Microsoft Windows, XML Core Services, Active Directory Federation Services, .NET Framework and Windows Hyper-V.
Microsoft addresses Zer0-Day vulnerability in Microsoft Office CVE-2015-1641 and according to Microsoft, Exploitation Detected. Windows HTTP protocol stack (HTTP.sys) CVE-2015-1635 is also critical as the attack is simple and leads to remote code execution. Hence we highly recommend to apply these patches as soon as possible.
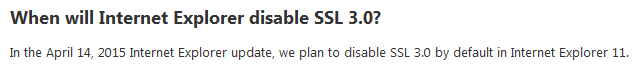
As mentioned earlier in Microsoft blog in February 2015 to disable SSL 3.0 by default in Internet Explorer 11.
Today Microsoft released an update MS15-032 that disables SSL 3.0 by default in Internet Explorer 11 and also Microsoft recommend to use latest security protocols such as TLS 1.2 in web servers and web applications.
Microsoft security bulletin summary for April 2015 in order of severity.
MS15-032: Cumulative Security Update for Internet Explorer (3038314)
Severity Rating: Critical
Affected Software: Internet Explorer
Impact: Remote Code Execution
MS15-033: Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (3048019)
Severity Rating: Critical
Affected Software: Microsoft Office
Impact: Remote Code Execution
MS15-034: Vulnerability in HTTP.sys Could Allow Remote Code Execution (3042553)
Severity Rating: Critical
Affected Software: Windows HTTP protocol stack (HTTP.sys)
Impact: Remote Code Execution
MS15-035: Vulnerability in Microsoft Graphics Component Could Allow Remote Code Execution (3046306)
Severity Rating: Critical
Affected Software: Microsoft Graphics Component
Impact: Remote Code Execution
MS15-036: Vulnerabilities in Microsoft SharePoint Server Could Allow Elevation of Privilege (3052044)
Severity Rating: Important
Affected Software: Microsoft SharePoint Server
Impact: Elevation of Privilege
MS15-037: Vulnerability in Windows Task Scheduler Could Allow Elevation of Privilege (3046269)
Severity Rating: Important
Affected Software: Windows Task Scheduler
Impact: Elevation of Privilege
MS15-038: Vulnerabilities in Microsoft Windows Could Allow Elevation of Privilege (3049576)
Severity Rating: Important
Affected Software: Microsoft Windows
Impact: Elevation of Privilege
MS15-039: Vulnerability in XML Core Services Could Allow Security Feature Bypass (3046482)
Severity Rating: Important
Affected Software: Microsoft XML Core Services
Impact: Security Feature Bypass
MS15-040: Vulnerability in Active Directory Federation Services Could Allow Information Disclosure (3045711)
Severity Rating: Important
Affected Software: Active Directory Federation Services
Impact: Information Disclosure
MS15-041: Vulnerability in .NET Framework Could Allow Information Disclosure (3048010)
Severity Rating: Important
Affected Software: .NET Framework
Impact: Information Disclosure
MS15-042: Vulnerability in Windows Hyper-V Could Allow Denial of Service (3047234)
Severity Rating: Important
Affected Software: Windows Hyper-V
Impact: Denial of Service
SecPod Saner detects these vulnerabilities and automatically fixes by applying security updates. Download Saner now and keep your systems updated and secure.
- Veerendra GG