DELMIA Apriso is utilized in production processes for digitalization and monitoring, with widespread deployment in automotive, aerospace, electronics, high-tech, and industrial machinery divisions. It supports various functions, including production scheduling, quality management, resource allocation, and warehouse management.
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning regarding a critical vulnerability, identified as CVE-2025-5086, a deserialization of untrusted data vulnerability that can lead to remote code execution. It has a CVSS score of 9.0 and an EPSS score of 68.66%, which indicate its critical severity. The remote code execution (RCE) vulnerability is in Dassault Systèmes’ DELMIA Apriso software. This manufacturing operations management (MOM) and execution (MES) solution is used by organizations worldwide.
Technical Analysis
The exploitation of CVE-2025-5086 involves sending malicious SOAP/HTTP requests to vulnerable endpoints. These requests load and execute a Base64-encoded, GZIP-compressed .NET executable embedded within the XML. Security researcher Johannes Ullrich observed these attacks originating from IP address 156.244.33[.]162.
The malicious payload has been identified as a Windows executable. Researchers have classified a similar DLL as “Trojan.MSIL.Zapchast.gen“, a program designed for cyber espionage activities such as keylogging, screenshot capture, and gathering active application lists.
Affected Products
The vulnerability affects DELMIA Apriso versions from Release 2020 through Release 2025.
Tactics, Techniques & Procedures (TTPs)
The observed attacks leverage the following MITRE ATT&CK TTPs:
- TA0002 – Execution: Attackers achieve code execution by exploiting the deserialization vulnerability.
- T1203 – Exploitation for Client Execution: This involves exploiting a vulnerability in DELMIA Apriso to execute malicious code on the server.
Indicators of Compromise
An indicator of compromise (IOC) associated with this vulnerability is the IP address 156.244.33[.]162, which has been linked to exploitation attempts.
Use SanerNow to Detect this Vulnerability
- Login to the SanerNow Portal.
- Switch to the account specific view and go to the Devices tab to manage devices for your account.
- If any device under this account has the application installed, by switching to the Assets tab you will see:
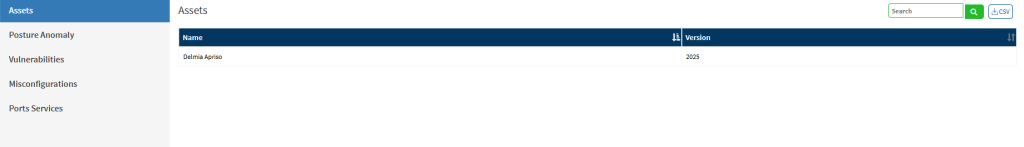
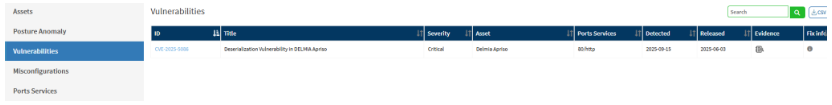
- If the Vulnerable version is installed, on switching to the Vulnerabilities section you can see the CVE listed:
To check if the CVE is associated with any threat actor or malware:
- In the options tab select VM
- In the High-Fidelity Attacks sections search for the CVE, if it is found, you will see:
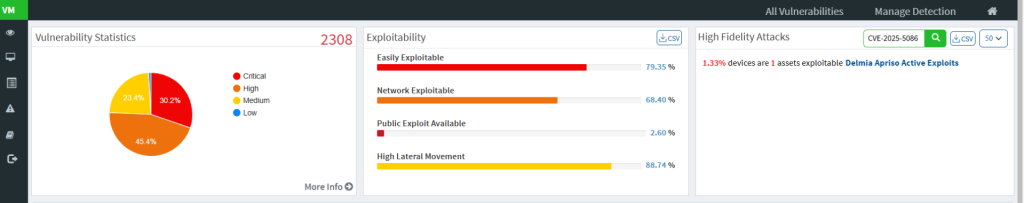
Mitigation & Remediation
CISA has added CVE-2025-5086 to its Known Exploited Vulnerabilities (KEV) catalog, and advises Federal Civilian Executive Branch (FCEB) agencies to apply necessary updates or mitigations by October 2, 2025. It is highly recommended that all organizations using DELMIA Apriso apply available security updates or consider discontinuing use of the software until a patch can be implemented.
Instantly Fix Risks with Saner Patch Management
Saner patch management is a continuous, automated, and integrated software that instantly fixes risks exploited in the wild. The software supports major operating systems like Windows, Linux, and macOS, as well as 550+ third-party applications.
It also allows you to set up a safe testing area to test patches before deploying them in a primary production environment. Saner patch management additionally supports a patch rollback feature in case of patch failure or a system malfunction.
Experience the fastest and most accurate patching software here.

