Steganography
Steganography is an art of hiding a message, image, or file within another message, image, or file.
Most images are used to hide the data. The flexibility of using images means that information can be hidden in a variety of ways. It can be scattered all over the image or inserted straight inside.
If data is inserted straight inside. we can find it easily using the below technique,
Hex Editor
like HexEdit, HxD on windows
using :%!xxd command on Linux
FF D8
FF D9
EOI (End Of Image) marker

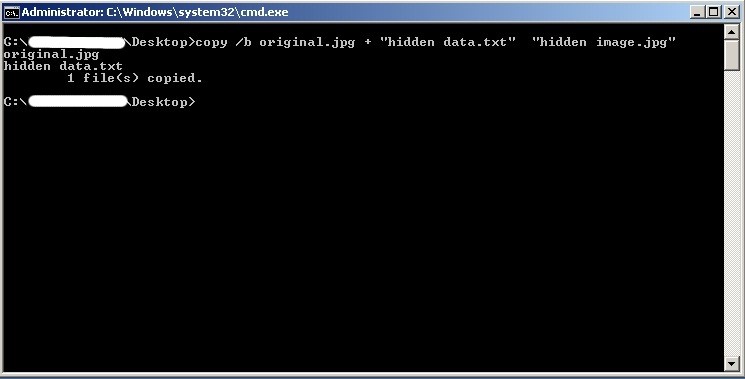
Here is an example to insert data straight inside the image without any tool on windows:
- Create a test file with some data to hide. ( Here i used “hidden data.txt” )
- Take an image to which you need to hide. ( Here i used “original.jpg” )
- In Command prompt use the below command to hide the content.
copy /b original.jpg + "hidden data.txt" "hidden image.jpg"
A new image will be created with your data hidden. You can open and view that image normally.
But, to view the hidden content open that image in any Hex editor as mentioned above and see the hidden data at the end after the EOI marker.
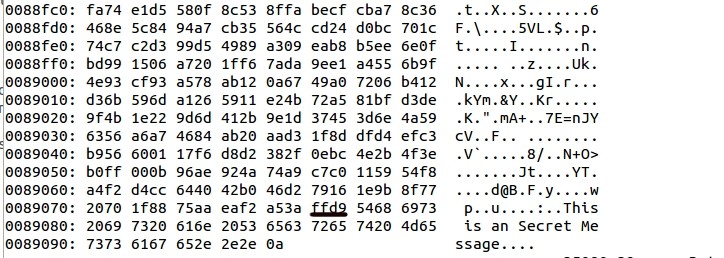
Later, a quick obfuscation layer is added (Password or key) to hide the visibility of the data in the HEX format. To view the original message we need that key or password.
Here is an example to insert data inside the image using Outguess tool:
outguess is one of the tool that allows the insertion of hidden information into
the redundant bits of data sources.
Data Hiding :
outguess -k "secretkey" -d hidden.txt image.jpg out.jpg
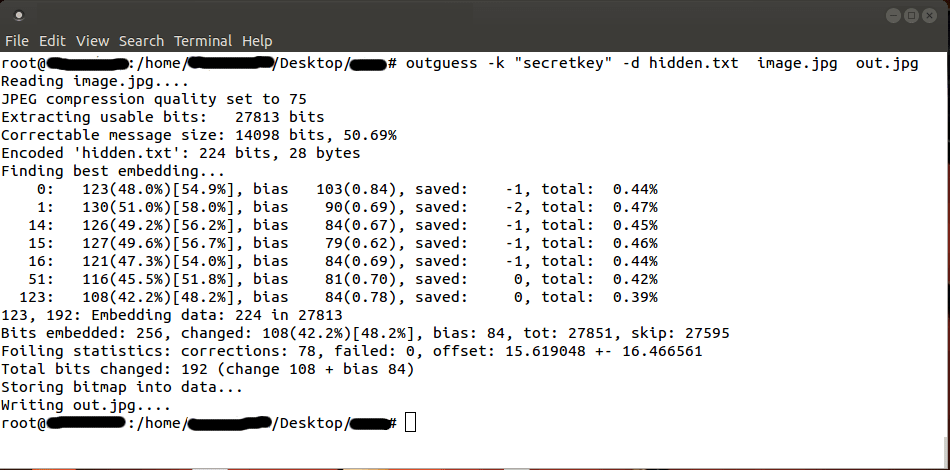
(more…)Data Retrieval :
outguess -k "secretkey" -r out.jpg hidden.txt
