RobbinHood is a relatively new ransomware that was first spotted in April 2018. A distinct feature of this ransomware is that it targets every computer individually and does not encrypt other computers via connected shares. RobbinHood claims to delete all the information related to an infected computer including the IP address, Encryption keys, etc. once the payment is complete. RobbinHood was developed using Golang (aka Go) and is known to be under active development.
SophosLabs published a detailed analysis of the infection process followed by RobbinHood ransomware. This ransomware in addition to encrypting files on the systems is known to disable security products by loading malicious drivers after bypassing the driver signature enforcement on Windows Systems which ensures loading of drivers signed by both the manufacturer and Microsoft. This method can be used to successfully subvert a setting in kernel memory on Windows 7, Windows 8 and Windows 10.
Disabling Security Products on Endpoints
Researchers have recently discovered RobbinHood Ransomware exploiting a known privilege escalation vulnerability (CVE-2018-19320) in Gigabyte drivers. The process involves loading a trusted, signed and vulnerable third party driver (Gigabyte) to patch the Windows kernel in-memory, to load a second unsigned malicious driver into Windows. This second driver is responsible for ending processes and files related to endpoint security products, bypassing tamper protection and enabling the ransomware on the target device. Since the driver runs in the kernel memory, it bypasses all the security controls which are applicable in the user space and successfully encrypts the files.
Ransomware Capabilities
- Deletes a list of pre-defined security related applications and its associated processes. This ensures that the processes cannot be restarted, as related files are no longer available on that system.
- Disables driver signature enforcement in Windows kernel.
- Disconnects all network shares from the targeted computer.
- Disables Windows automatic repair and other services related to antivirus, database, and mail server.
- Deletes Shadow Volume Copies and event logs.
Ransomware Infection Methods
Unlike other ransomware, RobbinHood’s methods of infection do not include spam campaigns. RobbinHood targets publicly accessible Remote Desktop Services and leverages Trojans which provide remote access to the ransomware attackers. A few researchers have also predicted that the EternalBlue exploit could have been used in the previous attacks, but there is concrete evidence supporting this.
SanerNow lists the potential targets for malware in an enterprise network (shown in the figures below).
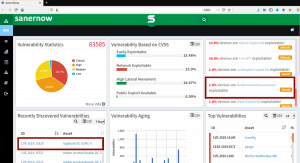
Fig2. SanerNow listing of potential targets in an organization for RobbinHood Ransomware
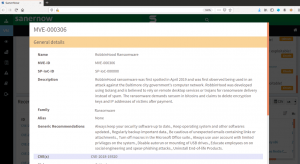
Fig3. Details about RobbinHood Ransomware
General recommendations to prevent ransomware infections
1. Keep your systems up-to-date with the latest patches available from vendors.
2. Allocate only necessary rights to user accounts.
3. Enable security at multiple stages so the attack chain can be disrupted at some stage.
4. Use multi-factor authentication (MFA) mechanisms.
5. Set complex passwords
6. Maintain an active backup of the files on your machines.
7. Allow Remote Desktop connections through a Windows Firewall and make it only accessible through a VPN.
8. Enable tamper protection on machines
9. Set complex passwords
SanerNow detects the vulnerabilities which could be used as infection vectors for spreading RobbinHood ransomware. Download SanerNow and keep your systems updated and secure.

