Oracle’s E-Business Suite is a collection of enterprise resource planning (ERP), customer relationship management (CRM), and supply-chain management (SCM) computer applications. Reports indicate that over 21,000 global organizations use Oracle EBS. Two critical vulnerabilities (CVE-2019-2638, CVE-2019-2633) in Oracle EBS have turned around the face of security for businesses. These Oracle EBS vulnerabilities (also known as ORACLE EBS PAYDAY vulnerabilities) could allow an attacker to completely compromise the Oracle EBS system. Additionally, an attacker can maliciously transfer electronic funds, print a bank check in the attacker’s name, read sensitive information or modify business data. Using the right vulnerability management tool can stop this.
Oracle EBS vulnerabilities critical security bugs though were patched by Oracle in April 2019 by using a patch management solution, thousands of business systems are still found to be unpatched and exposed to attack. Additionally, an IDC survey of 430 IT decision makers indicates that 64% of the organizations have reported an ERP breach.
Onapsis points out in there survey,
survey, coupled with critical alerts from the U.S. Department of Homeland Security continues to show that ERP systems are under fire more than ever.
These flaws are still a matter of concern as several attacks have been reported in the last 12 months.
As explained by Onapsis, the vulnerability lies in Thin Client Framework (TCF) which is an API provided to developers to build server-based applications by reducing the amount of processing at the client-side. TCF is known to be enabled by default on all EBS and cannot be disabled. TCF accessed through simple HTTP(S) requests thus making all EBS systems connected to the internet a potential target for attackers. Onapsis estimates that at least 1,500 EBS systems connected directly to the internet.
The two critical vulnerabilities:
- CVE-2019-2638 is a vulnerability in the ‘Consolidation Hierarchy Viewer‘ component of Oracle General Ledger.
- CVE-2019-2633 is a vulnerability in the ‘Messages‘ component of Oracle Work in Process.
These vulnerabilities are easily exploitable and attacks could affect additional products too. An attacker who successfully exploits the vulnerabilities could gain complete access to critical data. It allows unauthorized creation, deletion or modification of the critical data. It also allows an attacker to cause denial of service condition.
Attack Scenarios in Oracle EBS vulnerabilities
Onapsis published a report detailing two possible scenarios of financial fraud using Oracle EBS. The normal process for fund transfer involves a payment module for transactions. The information for this transaction is provided by financial and accounting modules and previously generated invoices for suppliers. EBS communicates with a bank for fund transfer using a preconfigured transmission protocol provided by Oracle or a custom protocol created by a company. However, it is carried out manually using the documents by EBS.
Malicious Electronics Fund Transfer
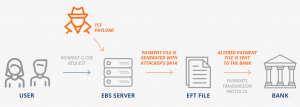 Image Credit: Onapsis_ThreatReport_Oracle_PAYDAY_Vulnerabilities
Image Credit: Onapsis_ThreatReport_Oracle_PAYDAY_Vulnerabilities
All companies have a specific day when the payments processes. Instructions about the Electronic Funds Transfer (EFT) for the bank by EBS as a text document with a previously configured format. The EFT file contains information about each pre-approved electronic transfer in the payment order, which includes amount to br transfered, the destination and source bank name, branch number and destination account number etc. The created EFT file is sent to the bank using transmission protocols provided by EBS or a communication protocol configured by the user. The EFT file is to instruct the bank to complete the transaction without the need for any further approval.
An attacker who abuses these vulnerabilities in EBS can modify the EFT details leading to compromise of the entire transaction process happening for several hundreds of accounts.
Malicious Check Printing in Oracle EBS vulnerabilities
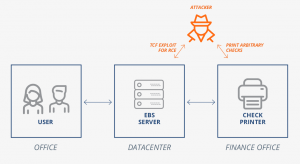 Image Credit: Onapsis_ThreatReport_Oracle_PAYDAY_Vulnerabilities
Image Credit: Onapsis_ThreatReport_Oracle_PAYDAY_Vulnerabilities
Printed Cashable Checks is important payment method make secure transactions. Companies use printers configured to work with EBS for printing checks. Any instruction about money movements coming from EBS considers legitimate. When EBS has to print a check, the application server configured to reach the printer. The OS treats the check printer as a regular one which uses to print any other files too.
An attacker can gain control over the OS of the EBS application server to print checks with desired details. But, the attacker needs to put in extra effort in ensuring the validity of the check number. An attacker can take over the EBS application server by exploiting a flaw in EBS and gain access to the check printer by modifying OS commands in different module configurations or by manipulating procedures and concurrent processes. After retrieving a valid check number and template, an attacker can create a file with an arbitrary cashable check and print it.
Another very threatening fact is that the application also allows an attacker to cover his tracks. SQL protocol used to erase audit logs and restore it to the state before the attack, leaving no trace behind.
Affected Products by Oracle EBS vulnerabilities
Oracle E-Business Suite (EBS)
Impact
These vulnerabilities affect Confidentiality, Integrity and Availability of the EBS system. An attacker who successfully exploits the vulnerabilities could gain complete access to critical data and allow unauthorized creation, deletion or modification of the critical data or allow an attacker to cause denial of service condition, which could disrupt businesses and lead to huge financial losses.
Solution
Oracle has released patches in April 2019 to mitigate these vulnerabilities. The attacks are more widespread now than ever and therefore recommend that these updates (if not installed) install on the highest priority.

