Secure Hash Algorithm 1, or SHA-1, is a cryptographic hash function designed by the National Security Agency to be part of the Digital Signature Algorithm. A hash function is a method to map an arbitrary set of data to data of fixed size called hashes or digests. And hashing is used for digital signatures, one of the pillars of PKI’S. It ensures authenticity in/browsers, documents, downloadable content, and financial transactions. SHA-1 produces a 20-byte hash value known as a message digest. Every message digest is expected to be unique. We should get a completely different hash if the original data is changed in any way. SHA-1 can also have a few vulnerabilities that might cause problems. Therefore, a good vulnerability management software is the key solution to this problem.
In cryptography, collision is one kind of attack specific to the hash. A collision occurs when an identical hash is in production for two different inputs. It can lead to signature forgery. Secure Hash Algorithm 1 is now broke because of this collision attack. A successful collision attack is in development and demonstrated by Google researchers. SHA-1 is no longer secure, and we should not rely on it for practical security. Until now, collision attacks have been more theoretical and expensive. But the SHA-1 attack is no longer theoretical. A method has been in development by Google researchers that allow us to create two PDF files having different content but producing identical hash value. Any anomalies in them can resolve by a good vulnerability management tool.
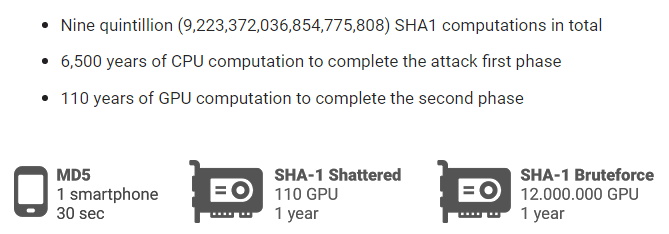
Below are some numbers that give a sense of how large-scale this computation was,
(Source: Google Security Blog)
“SHA-1 shattered attack is still more than 100,000 times faster than a brute force attack which remains impractical.”
From a security perspective, digital signatures and cryptographic keys are important. SHA-1 collision can be in exploitation by attackers to falsify the digital signatures and break the communication, which uses the SHA-1 hash algorithm. Duplicate certificates can originate with the help of a collision attack, which allows an attacker to conduct impersonation attacks, man the middle attacks, and steal sensitive data.
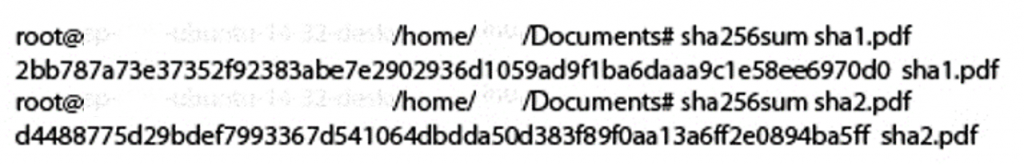
As proof of the concept, two PDF files are present by Google researchers, which have different content but the same SHA-1 hash value.
Calculating sha1sum of the pdfs –
Calculating sha256sum of the pdfs –
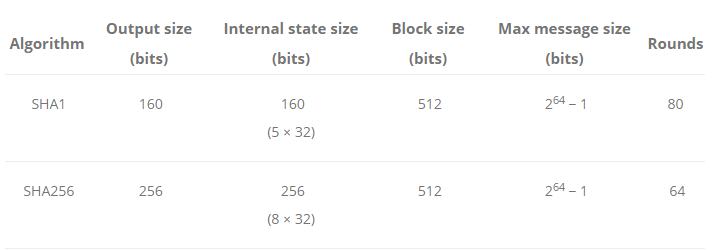
Due to the small size of the SHA-1 hash, as mentioned in the above table (source: KeyCDN), it is more prone to attack.
SHA-1 collision detection:
An online tool is developing based on counter-cryptanalysis, which can be of use to submit files and checks for SHA-1 collision attacks. Counter-cryptanalysis is a paradigm to strengthen weak cryptographic primitives and detect cryptanalytic attacks at the cryptographic level.
- It detects whether the message is constructing itself using a collision attack.
- A single message of collision pair is sufficient.
- Based on the crucial properties of the known cryptanalysis on MD5 and SHA1:
- The attack exploits trivial differential steps with probability (close to) 1 to be able to obtain ‘low’ complexity.
- Very few message block differences result in attacks with ‘low’ complexity.
Basic algorithm: detects last near collision block
– Guess ‘message block difference’ and ‘difference’ at trivial step (i).
– Reconstruct computation.
– Check whether collision in the chaining value is present.
If the guess is correct, then the collision is present with certainty.
If the guess is incorrect, then a false positive occurs.
Defense:

As shown in the above diagram, consider migrating to safer alternatives such as SHA-256 or SHA-3 and also make use of online tool availability for collision detection for the PDF.
Google will release the technical details of the proof-of-concept soon, which can be of use for the collision attack, i.e. everyone can create two PDFs that hash to the same message digest.