Accessing IT infrastructure is fundamental to building and maintaining a security posture. IT security admins have superficial visibility of their IT infrastructure with insufficient actionable insights, which is not enough. In addition, IT security admins are unaware of the most obvious outliers, deviations, and aberrations that can lead to sophisticated cyberattacks. Continuous Posture Anomaly Management process can finally help you with these issues. Some of the obvious risk exposures are:
- Anonymous logins
- Poorly configured Wi-Fi settings
- Unwanted network open ports
- Usage of unapproved VPN software and more.
To build a robust security posture, IT security admins must know in and out of the IT infrastructure to detect and analyze the outliers and mitigate them. To achieve this, SecPod recently introduced its latest innovation SanerNow Continuous Posture Anomaly Management which facilitates IT security admins to get a deeper and holistic view of their IT infrastructure to discover the anomalous posture and eliminate outliers.
This article will help you understand the different outliers, deviations, and aberrations you can uncover with SanerNow Continuous Posture Anomaly Management.
The SanerNow Continuous Posture Anomaly Management: Uncovering the Most Obvious Risks!
Daily automated anomaly scans to discover various posture anomalies
SanerNow Continuous Posture Anomaly Management process provides continuous and automated scans to detect a plethora of anomalies.
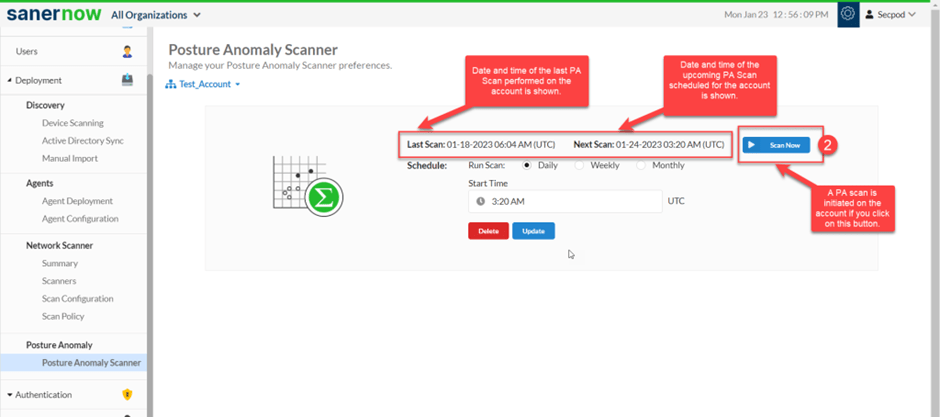
The anomaly scans detect various anomaly types:
- Rule-based anomalies like collective mapping ARP entries and DNS cache entries.
- Data trend anomalies include changes in hostnames, MAC addresses, and IP addresses.
- Outlier-based anomalies include deviations in Run Command History, Firewall settings, Scheduled Tasks, Services, Autorun applications, IP Forwarding Status, UID GID mapping, Kernel parameters, RPC, Software licenses, or High CPU or RAM usage.
- Any deviations from standard configuration are considered anomalies. Moreover, SanerNow Continuous Posture Anomaly Management has 40+ checks to test whether the devices are set with different configurations.
Statistical anomaly computation to identify anomalous posture within an organization’s devices
Continuous Posture Anomaly Management process uses statistical computations and Machine learning algorithms to identify anomalies in your organization. Some of the anomalies include:
- Vulnerable process making an outbound network connection
- Irregular Host IP to MAC address maps found across devices in the ARP table
- Applications are found to make outbound connections to unusual ports
- Unusual command execution found in Windows Run Command history
- Unusual tasks are scheduled in Task Scheduler, and more
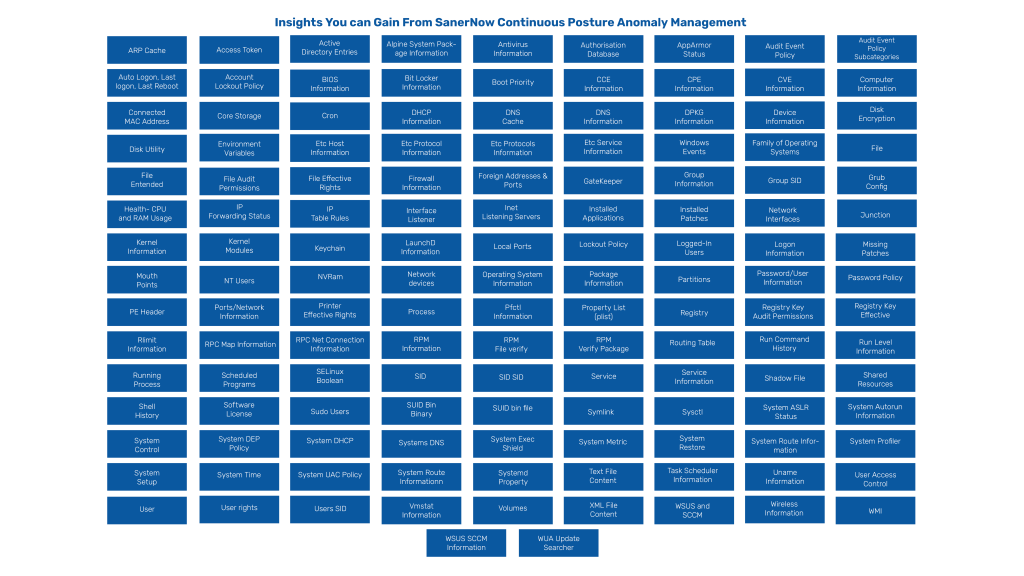
Likewise, data points are collectively computed to derive anomalies so IT security admins can get a holistic view of their IT infrastructure.
Outlier analysis of the gathered data to uncover interesting and insightful posture facts.
In mid-size or large organizations, IT security admins always look at security from an individual system point of view. Hence, they lack visibility to deviations. Besides, there will be commonalities across systems, like standard security policies, common security controls, application policies, device control policies, common security products and protocols, and common behavioral traits. Deriving deviations against these commonalities is a tedious task.
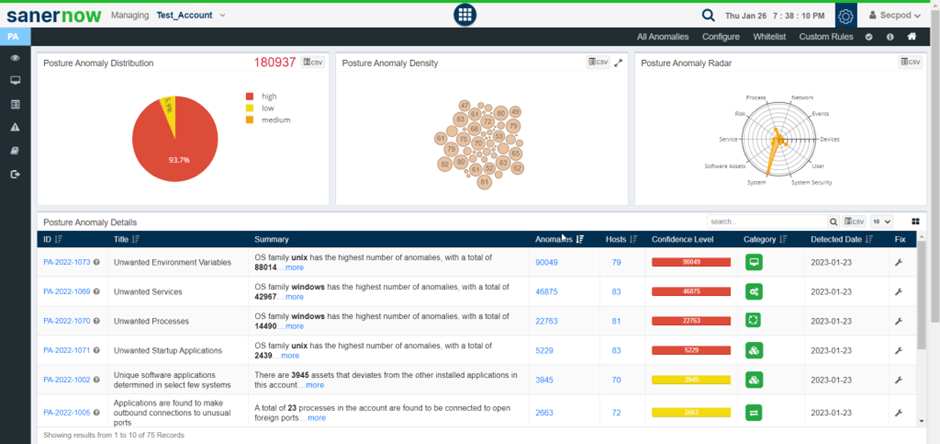
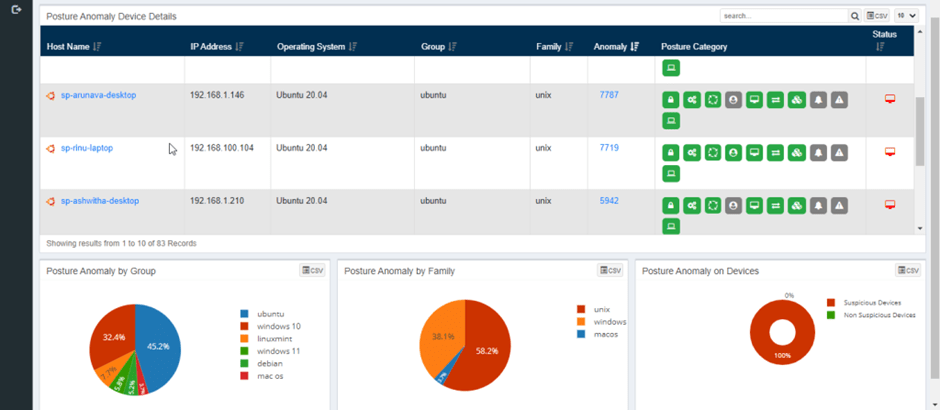
SanerNow CPAM holistically looks at the IT infrastructure and analyzes the deviations. The outlier analysis of the collected data uncovers insightful facts about security posture. The insightful dashboard facilitates IT security admins to get clear visibility over their IT infrastructure.
Whitelist your IT environment and identify anomalies to make your IT known-good
Once you get holistic visibility over your IT infrastructure, With SanerNow CPAM, you can verify and whitelist the systems and configurations by assessing them with various parameters. Therefore, Whitelisting your IT environment helps you identify anomalies and makes your IT known well. Also, Whitelisting anomalous findings in the devices bring a standard to be followed while computing anomalies.
You can whitelist the following:
- Unwanted Network Ports that are configured
- Unwanted Services and Processes
- Unwanted Startup Applications
- Unwanted Environment Variables
- Unwanted Devices
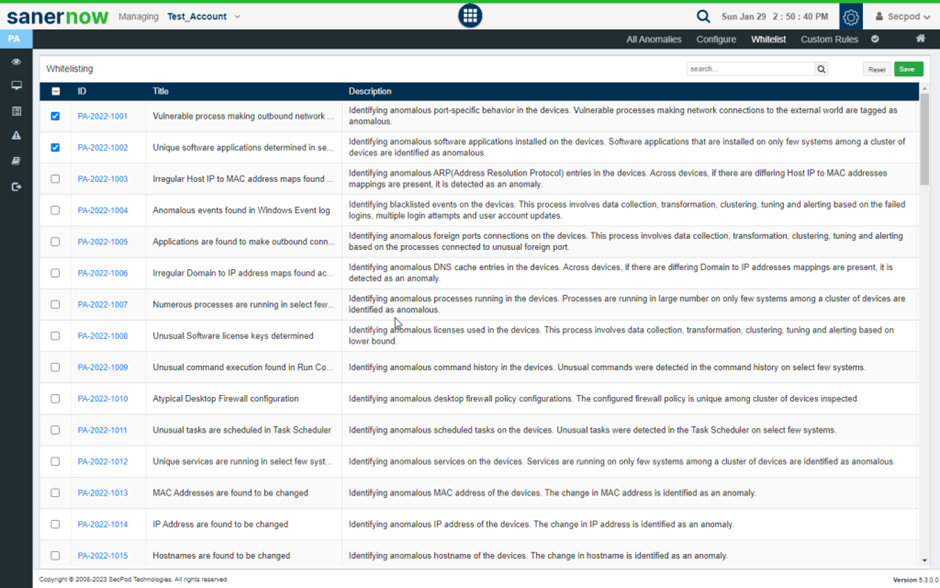
Analyze an array of security controls, and learn deviations
With SanerNow CPAM, identify the security controls & deviations and analyze them to take possible action to mitigate them finally. Some of the security controls that you can detect are:
- Wi-Fi Security is disabling
- Bit Locker is disabling
- Wi-Fi encryption is disabling
- Cloud applications are installing
- Time Synchronization is not enabling
- Outdated software applications are installing.
- Unknown disk type or Mass Storage devices connected
- Address Space Layout Randomization (ASLR) is disabling
- System Data Execution Prevention (DEP) Policy is disabling
- User Account Control (UAC) policies are not configuring properly …
In addition, SanerNow CPAM identifies security controls deviations with high certainty that are exploiting from an individual device perspective.
Create your own anomaly detection rules and respond to aberrations with integrated action.
In SanerNow CPAM, you can write custom detection and response scripts to respond to threats through its query module.
A query requests information from a database or live data from devices. Hence, SanerNow CPAM, with a metadata model, supports natural language-based queries related to the processes, services, users, registry, network, and device configurations. Also, it is fully compliant with well-established standards, such as SCAP and STIX/TAXII.
Query results are fetching in microseconds to help make quick decisions. Complex queries are creating, or multiple queries are cascading with ‘AND’ and ‘OR’ combinations.
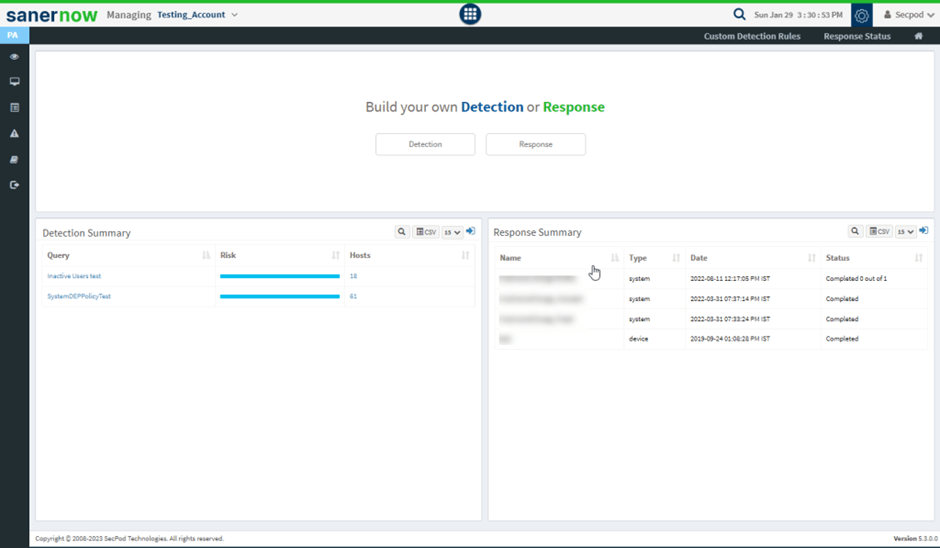
Queries are categorized into two types:
1. Default Queries – The CPAM provides default queries that can fetch information such as anti-virus information, hosts that have disabled the firewall, moreover, hosts that have disabled Bit locker protection, and more.
2. Custom Queries – Users can create custom queries.
In addition, the integrated actions will finally help remediate the same console’s anomalies.
Final Thoughts
Keeping your IT infrastructure in check is critical for staying ahead of the cyber curve. However, With Continuous Posture Anomaly Management (CPAM), you can declutter and normalize your IT infrastructure to enhance the overall security posture of your organization!
Therefore, if you Want to see CPAM in action? Schedule a demo today and learn how CPAM can help normalize your organization’s IT infrastructure!