Audit logs capture and record administrative activities within your organization’s cloud infrastructure. They offer a detailed record of user activities, system events, and resource changes across an organization’s cloud infrastructure.
This article helps understand the structure of the log, the type of events recorded in the log, sample use case, UI operations that include search, filter, and export options, and lastly security and compliance benefits of cloud audit logging.
Structure of the Cloud Audit Log
Each entry in the log typically contains:
Job Code
A unique identifier or range representing a specific logged action or event.
Date & Time
A timestamp (with timezone) indicating exactly when the event occurred.
Organization
The business or security domain under which the activity was executed.
Account
The specific cloud account involved in the action.
User
The identity (human or service account) that initiated the activity.
Message
A descriptive statement outlining what happened, including affected resources, scan statuses, or configuration changes.
Categories of Events Captured in Audit Log
Audit log codes for cloud security are categorized into functional groups, each assigned a specific range of codes and corresponding events that capture particular actions or outcomes in cloud security operations.
Here’s a real-time assignment of Job Code and Event Categorization Across Different Tools.
| Code | Category | Coverage |
| 51000 | Profile Management | Covers activities related to creating, updating, and deleting cloud profiles |
| 52000 | Scan Management | Focuses on cloud scan scheduling and resource discovery |
| 53000 | CSPM (Cloud Security Posture Management) | Logs posture management scan events and benchmark configurations |
| 54000 | CSAE (Cloud Security Asset Exposure) | Includes scan execution, cloud resource group management, watchlist configuration, and cloud resource tags |
| 55000 | CIEM (Cloud Infrastructure Entitlement Management) | Captures entitlement scan activities |
| 56000 | CSPA (Cloud Security Posture Anomaly) | Covers scan and whitelist operations |
| 57000 | CSRM (Cloud Security Remediation Management) | Tracks remediation job creation, updates, rollbacks, and execution |
Click here for more information.
Types of Events Recorded
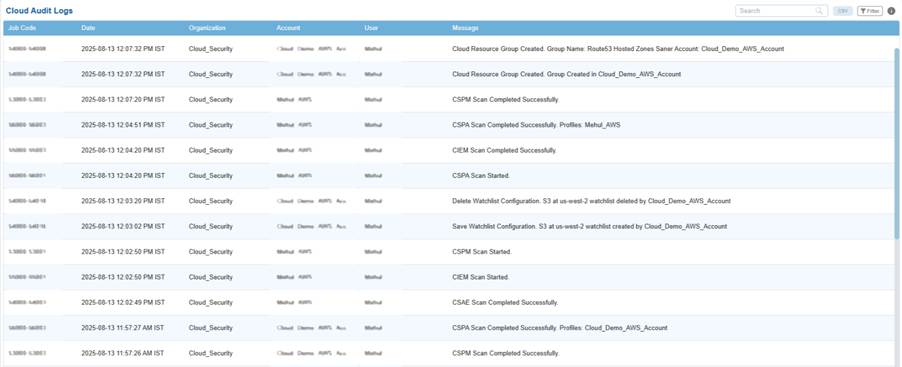
The sample log showcases a range of event types, including:
Cloud Resource Creation
The creation of Route53 Hosted Zones or resource groups are shown as an example.
Security Scans
Completion and initiation of CSPM (Cloud Security Posture Management), CSPA (Cloud Security Posture Assessment), CIEM (Cloud Infrastructure Entitlement Management), and CSAE (Cloud Security Assessment Engine) scans.
Configuration Changes
Watchlist modifications such as adding or deleting monitored resources.
These logs capture both start and completion events, ensuring traceability of processes from initiation to closure.
Sample Use Case
As per the given log:
- At 2025-08-13 12:07:32 PM IST, a Route53 Hosted Zone resource group was created by the user xxx under the Cloud_Demo_AWS_Account.
- Within the same minute, a CSPM scan completed successfully for xxx_AWS.
- A little after, watchlist configurations were both added and deleted, followed by a series of security scans across CSPM, CSPA, CIEM, and CSAE modules.
Such sequential visibility ensures that if an unauthorized configuration change occurred, investigators can trace it to a precise user action and time.
Search, Filter, and Export Operations in Saner Cloud Audit Logs
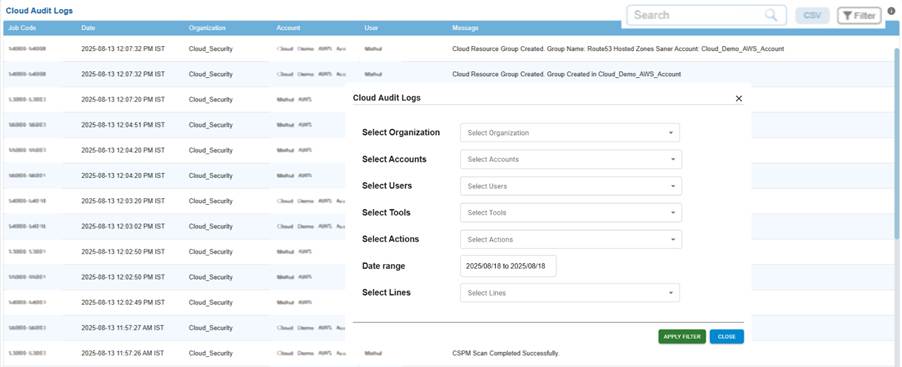
The audit log interface offers several options for efficiently locating and analyzing data. Users can perform searches by entering keywords such as names, job codes, or other identifiers. The filtering feature allows for refining results based on criteria like organization, account, users, tools, actions, date range, or activity lines. Furthermore, logs can be exported in CSV format for comprehensive offline analysis.
Security & Compliance Benefits
Maintaining detailed audit logs supports:
Incident Investigation
When a security alert is raised, these logs help pinpoint the exact action, user, and resource involved.
Compliance Audits
Many frameworks (e.g., ISO 27001, SOC 2) require demonstrable activity records.
Operational Transparency
Stakeholders gain visibility into cloud security posture checks and configuration changes.
Privilege Monitoring
Detects high-privilege operations, such as watchlist deletions or resource provisioning.
Go Further
Saner Cloud is a comprehensive solution designed to help organizations effectively manage their cloud operations. Key features of the product include asset exposure, posture management, posture anomaly detection, identity and entitlement management, and remediation management.
Documentation is organized to help you quickly and efficiently find the information you need, whether you’re troubleshooting, learning how to use specific tools, or seeking in-depth knowledge about the product suite.
Discover how to troubleshoot issues with Saner Cloud Audit Logs. Schedule your trial today for a more comprehensive experience!

