In 2025, ransomware escalated from a disruptive nuisance to a global economic crisis. Cybersecurity Ventures projects that ransomware damages will reach $57 billion this year, translating to $156 million per day or $109,000 per minute. Reactive cybersecurity tools fail to contain this scale of damage. Detection typically occurs after systems have been encrypted, data exfiltrated, and operations disrupted. At that point, the impact has already spread across business functions, leaving limited options for recovery.
The evolving sophistication of ransomware tactics, including double extortion, fileless attacks, and lateral movement, has rendered signature-based detection increasingly ineffective. According to recent analyses, 60% of ransomware attacks bypass traditional detection tools, leaving organizations vulnerable.?
In response, the cybersecurity industry is moving toward a prevention-first approach —one that focuses on stopping threats before they escalate, instead of relying on delayed detection and reactive response. Gartner predicts that by 2030, preemptive cybersecurity solutions will account for 50% of IT security spending, up from less than 5% in 2024.?
The Evolution of Ransomware and the Failure of Reactive Security
Ransomware has shifted from blunt-force disruption to calculated, multi-stage operations. Attackers increasingly use double and triple extortion — encrypting data, exfiltrating sensitive files, and threatening disclosure to intensify leverage. Techniques such as fileless intrusion, lateral movement, and credential abuse allow ransomware to spread quietly across systems while avoiding traditional detection.
Ransomware-as-a-Service (RaaS) continues to reduce the technical barrier for attackers. Affiliates license ready-made payloads and infrastructure from operators, accelerating the volume and scale of attacks. Target selection has become more calculated, often aimed at organizations where even brief disruptions carry immediate financial or regulatory consequences.
Traditional detection tools are increasingly ineffective against these techniques. Signature-based systems rely on predefined threat patterns, an approach that falters against zero-day exploits and polymorphic code. Cybersecurity Ventures estimates that ransomware damage will reach $57 billion globally in 2025, or roughly $156 million per day — an economic signal of how reactive tools continue to fall short.
Timing remains a fundamental issue. Detection typically occurs after encryption has begun, leaving security teams to respond during or after active compromise. At that stage, organizations are negotiating under pressure, managing outages, and attempting recovery with limited room for containment.
Prevention-first models approach the problem differently. Instead of waiting for malicious behavior to manifest, they eliminate common entry points — through attack surface reduction, privilege restriction, and blocking unauthorized execution paths. The defensive posture shifts from reactive containment to preemptive disruption, addressing threats before they reach operational depth. Delays in visibility compound the problem. In 2024, more than half of ransomware incidents resulted in full data encryption, even among organizations with modern detection tools in place. Once encryption begins, operations grind to a halt and the focus shifts to containment, negotiation, and damage control — none of which address the underlying vulnerability.
Reactive tools address symptoms. Prevention-first strategies — those that reduce the attack surface, remove exploitable conditions, and block execution paths — intervene before ransomware begins to operate. The security model changes from watching for attacks to stopping the conditions that allow them to occur. As ransomware matures, so must the defense strategy and that shift cannot wait.
What Is Prevention-First Security?
Modern ransomware campaigns often execute faster than security teams can respond. Attackers exploit unpatched systems, abuse identity privileges, and traverse internal networks with minimal detection. By the time alerts are raised, encryption has usually begun, and recovery becomes reactive by design.
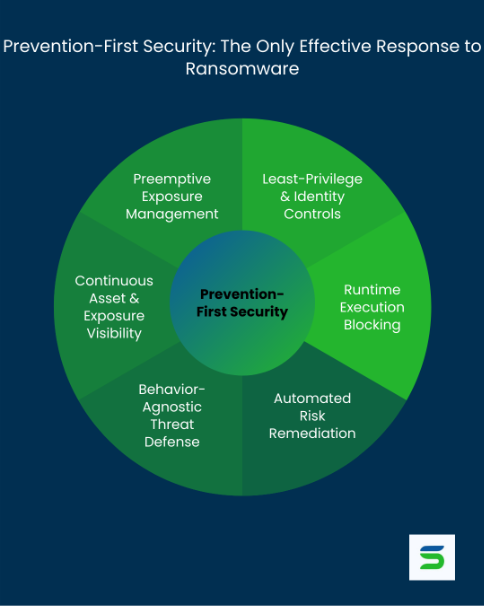
Prevention-first security changes the point of engagement. Rather than relying on behavioral analytics or signature matching after an intrusion starts, it interrupts the attack path before execution. The focus shifts to eliminating exploitable misconfigurations, enforcing access boundaries, and blocking malicious activity at runtime—before it can gain process-level control or lateral access.
Gartner refers to this model as Preemptive Cyber Defense, forecasting that by 2030, half of all enterprise security platforms will be based on preemptive principles — up from less than 5% in 2024. The shift reflects growing pressure to defend against ransomware variants designed to bypass traditional detection entirely.
Why Prevention Is the Only Effective Solution
Reactive security models rely on identifying malicious behavior once it’s in motion. This creates an inherent delay — between intrusion, detection, and response — that ransomware exploits by design. Pre-execution tactics like privilege escalation, process injection, and remote code execution typically unfold in seconds. Any lag in response allows attackers to complete their objectives before containment begins.
Prevention-first systems remove this dependency on speed. They block unauthorized scripts from executing, disable credential abuse pathways, restrict exposure from open ports or misconfigured services, and enforce least-privilege access across identities and assets. Since these controls operate independently of signature matching, they remain effective against polymorphic malware, zero-day exploits, and fileless attacks.
Rather than generating alerts to be triaged after the fact, prevention-first security eliminates the operational conditions ransomware depends on. This reduces dwell time to zero, limits false positives, and avoids the post-incident overhead associated with decryption, negotiation, or data restoration.
Where reactive models respond to damage, prevention-first architecture prevents execution altogether, cutting the attack off before it ever begins.
How SecPod’s Saner Platform Helps in Ransomware Prevention
Ransomware thrives in complexity, misconfiguration, and delay. Preventing it requires consistent control, not just over vulnerabilities, but over how assets are exposed, configured, and accessed across environments. The Saner Platform applies this principle at scale.
Built on an AI- powered prevention-first foundation, SecPod’s Saner Platform continuously reduces the attack surface across endpoints, servers, and cloud workloads. It identifies exploitable conditions — unpatched systems, excessive privileges, exposed services — before attackers can act. Automated remediation closes gaps at the source, while compliance enforcement and runtime controls suppress malicious behavior before execution.
Rather than reacting to indicators of compromise, the platform eliminates the footholds ransomware relies on, denying attackers the conditions they need to operate.
The Saner Platform delivers the prevention-first control your security program needs, at speed and at scale.