Managing cloud environments can become overwhelming with 1000+ resource types and around 200+ AWS services. To control costs, mitigate risks, and reduce operational complexity, it becomes essential to organize resources into meaningful categories. Cloud Security Asset Exposure categories provide a systematic view of deployed assets across various domains, including IoT, Machine Learning, Security, Quantum Technologies, and more. However, valuable insights often come not only from the resources present in these categories but also from those that are missing. Absences may indicate unused services, misconfigured discovery logic, or gaps in visibility, all of which can significantly impact governance and security posture.
Understanding AWS Resource Categorization for Security and Governance
AWS uses a standardized service categorization framework to organize its extensive portfolio of cloud services into logical groupings, which aids in resource management and governance. When organizations implement cloud security and compliance monitoring systems, they utilize AWS’s official service categories, such as, Compute, Storage, Database, Networking & Content Delivery, Analytics, Machine Learning, and Security, Identity & Compliance to systematically classify and assess their resources.
AmazonAwsforengineers describes the dual naming convention found in security configuration files and reflects this organizational structure. The identifier, formatted in normalized lowercase (like “compute”), is known as “resource_category_name”, while “resource_category_display_name” provides the corresponding human-readable label (such as “Compute”) for user interfaces and reporting dashboards. For example, EC2 instances fall under the Compute category since they represent Amazon’s core web service that delivers secure and scalable compute capacity in the cloud. Other services such as Lambda, Elastic Beanstalk, and Lightsail also contribute to providing scalable computing capacity and serverless execution options.
AmazonGeeksforGeeks describes the methodology that helps security teams and compliance tools to implement consistent governance policies, conduct targeted risk assessments, and maintain organized oversight across various functional domains within their cloud infrastructure. This ensures that resources are appropriately classified according to their operational purpose and technical characteristics within the broader AWS ecosystem.
Cloud Resource Categories and What Do They Tell Us?
A real-world dashboard snapshot and what it tells us…
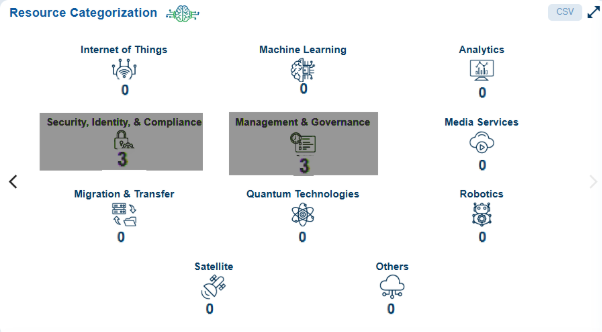
Cloud dashboard shows 15+ resource categories, but only two (Security and Governance) were captured and displayed.
All other 9 categories report “0” resources, including critical domains like:
- Internet of Things
- Machine Learning
- Analytics
- Migration & Transfer
- Media Services
- Quantum, Robotics, Satellite, and Others
This could be due to:
- Actual absence of these resources
- Resources that exist but neither categorized nor tagged
- Existing tools or policies not configured to detect or label resources properly
Security Implications of having unreliable resource categorization:
- Risk of uncategorized or unmanaged resources
- Hidden cost centers
- Compliance exposure due to audit blind spots
How Resource Categorization Works?
Continuous Monitoring
Real-time or scheduled scans ensure new resources are categorized promptly.
Automated Classification with Rule Engines
Rule engines typically map resources to categories based on service type, tags, or metadata.
Tagging and Metadata
Tagging is essential for categorization enforced according to the tagging standards across accounts and subscriptions. This provides sufficient flexibility for any organization that wants to implement additional filtering on a specific category. For instance, tags can help answer questions such as: Among the resources in the Compute category, which ones are production EC2 instances and which are testing Lambda functions?
Visualization and Reporting
- Dashboards: Effective dashboards allow filtering by category, region, account, and compliance status.
- Drill-Down Capabilities: Allows users to investigate individual resources, their metadata, and associated risks.
What is Getting Categorized?
Each Resource Category (e.g., Machine Learning, Security, IoT) consists of multiple resource types across various AWS or Azure services. These are logical aggregations of underlying constructs, not just single-resource groups.
A robust cloud visibility solution examines and organizes these service-specific resources into meaningful categories for governance and operations.
For more information, follow the link: https://docs.aws.amazon.com/whitepapers/latest/aws-overview/amazon-web-services-cloud-platform.html
How is Resource Categorization Used Across Different Industries for AWS and Azure?
| Resource Categories | Used in Industries | Use Case | AWS Services | Azure Services |
| Compute | Finance | High-frequency trading, risk modeling | EC2, AWS Batch | Azure Virtual Machines, Azure Batch |
| Application Integration | Retail | Order processing, CRM integration | Amazon SQS, SNS, Step Functions | Azure Logic Apps, Azure Service Bus |
| Blockchain | Supply Chain | Product tracking, provenance | Amazon Managed Blockchain | Azure Blockchain Workbench (deprecated), Quorum |
| Business Applications | HR | Workforce management, payroll systems | Amazon WorkDocs, Amazon Honeycode | Dynamics 365, Power Apps |
| Networking & Content Delivery | Media & Entertainment | Global content streaming, load balancing | Amazon CloudFront, ELB | Azure Front Door, Azure CDN |
| Cloud Financial Management | Enterprise IT | Budgeting, cost tracking | AWS Cost Explorer, AWS Budgets | Azure Cost Management and Billing |
| Databases | Healthcare | EHR systems, secure patient data storage | Amazon RDS, Amazon Aurora, DynamoDB | Azure SQL Database, Cosmos DB |
| Storage | Education | Lecture videos, scalable backups | Amazon S3, Glacier | Azure Blob Storage, Azure Files |
| Developer Tools | Software Development | CI/CD, version control | AWS CodePipeline, CodeCommit | Azure DevOps, GitHub Actions |
| End User Computing | Remote Work | Virtual desktops, secure access | Amazon WorkSpaces, AppStream 2.0 | Azure Virtual Desktop, Windows 365 |
| Front-end Web & Mobile | E-commerce | Mobile and web app hosting | AWS Amplify, Amazon API Gateway | Azure App Service, Azure API Management |
| Internet of Things | Manufacturing | Factory monitoring, predictive maintenance | AWS IoT Core, AWS Greengrass | Azure IoT Hub, Azure IoT Edge |
| Machine Learning | Healthcare | Diagnosis support, drug discovery | Amazon SageMaker, Comprehend Medical | Azure Machine Learning, Azure Cognitive Services |
| Analytics | Marketing | Customer insights, campaign analytics | Amazon Redshift, Athena, QuickSight | Azure Synapse Analytics, Power BI |
| Security, Identity, & Compliance | Government | Secure access, compliance monitoring | AWS IAM, AWS Shield, Macie | Azure Active Directory, Azure Defender |
| Management and Governance | Large Enterprises | Audit, configuration management | AWS Config, Control Tower | Azure Policy, Azure Blueprints |
| Media Services | Broadcasting | Video processing, live streaming | AWS Elemental MediaLive, MediaConvert | Azure Media Services |
| Migration & Transfer | Legacy IT Systems | Cloud migration, hybrid connectivity | AWS Migration Hub, DMS | Azure Migrate, Azure Database Migration |
| Quantum Technologies | Research | Quantum simulation, cryptography | Amazon Braket | Azure Quantum |
| Robotics | Logistics | Automated warehousing, delivery drones | AWS RoboMaker | ROS on Azure VMs, Custom ML |
| Satellite | Agriculture | Earth observation, crop monitoring | AWS Ground Station | Azure Orbital |
| Others | Non-profits | Donation systems, global collaboration | AWS Nonprofit Credit Program | Microsoft Tech for Social Impact |
How are Resources Grouped into Categories?
Resource categorization is achieved by cross-mapping AWS service metadata with a defined taxonomy. Here’s how it’s typically done:
- TAG-BASED CLASSIFICATION
Using standardized tagging to organize resources under high-level categories
json
{
“name”: “describe_instances”
“resource_category_display_name”: “Compute“,
}
Explanation:
In AWS, the “describe_instances” call is frequently used through the SDK or CLI to list EC2 virtual machines. By categorizing this under “Compute,” cloud security, cost, or operations, platforms can effectively organize this API alongside other compute-related operations, such as ECS and Lambda.
- SERVICE-TYPE MAPPING
Using the in-built services for category mapping that helps with assigning a resource type to a Category quickly.
With this mechanism cloud services (like EC2, S3, RDS, etc.) are mapped to predefined categories (like Compute, Storage, Database, etc.) to organize them meaningfully.
- RULE ENGINES
Auto-categorize based on defined criteria and trigger alerts when resources are uncategorized or miscategorized.
Explanation:
The rule engine uses defined criteria, such as resource name, tags, service type, and metadata, to automatically classify resources.
For example:
– If a resource is an EC2 instance, it is categorized as Compute
– If it is a DynamoDB table, it is categorized as Database
If a resource is either Uncategorized (not assigned to any category) or Miscategorized (wrongly assigned, for example, an S3 bucket labeled as Compute), then the rule engine raises an alert, flagging it for review or correction.
Bring it Together in Dashboards!
Your view is only as clear as your categorization. With the diagnostics in Saner Cloud’s visual dashboard, you can quickly gather visibility and coverage gaps in cloud resource discovery and categorization processes.
Go Further
Saner Cloud is a comprehensive solution designed to help organizations effectively manage their cloud operations. Key features of the product include asset exposure, posture management, posture anomaly detection, identity and entitlement management, and remediation management.
Documentation is organized to help you quickly and efficiently find the information you need, whether you’re troubleshooting, learning how to use specific tools, or seeking in-depth knowledge about the product suite.
Discover how Saner CSAE is designed to visualize the resource sprawl across your cloud accounts. Schedule your trial today for a more comprehensive experience!

