Cloud misconfigurations are one of the typical and yet often overlooked threats in cloud environments. They can result in data breaches, compliance violations, and operational disruptions. This article examines the signs of misconfigurations, including unexpected public access, unusual traffic patterns, and few cloud service-related misconfigurations. It also illustrates their potential impact through real-world examples.
The article also provides a structured implementation blueprint that outlines the workflow from detection to remediation, utilizing Cloud Security Posture Management (CSPM), Cloud Infrastructure Entitlement Management (CIEM), and Cloud Security Risk Management (CSRM) modules. Moreover, it emphasizes the importance of continuous monitoring, security automation, and cloud-native best practices in maintaining a strong security posture.
Signs You Might Have a Misconfiguration
- Unexpected Public Access to Resources:
Storage buckets, databases, or compute instances accessible without authentication.
- Unusual Network Traffic or Access Patterns:
Sudden spikes in outbound traffic, geographic anomalies, or access at odd hours.
- Frequent or Unauthorized Changes to Security Groups or Firewall Rules:
Ports opened/closed frequently, or new CIDR blocks, allowing broad access (e.g., 0.0.0.0/0).
- Alerts or Findings from Cloud Security Tools (e.g., CSPM, SIEM, IDS/IPS):
Warnings from AWS Lambda, Azure Defender, GCP SCC, etc., indicating misconfigurations or anomalies.
Scenario
In a hypothetical scenario, an organization decided to move a significant portion of its infrastructure to the cloud, primarily using AWS or Azure. In a rush to meet a tight product launch deadline, an internal team deployed a set of microservices without conducting a proper security review.
Among the oversights were:
- An S3 bucket containing sensitive client data was set to public-read
- IAM roles were over-provisioned, permitting lateral movement across cloud environments
- Logging was partially disabled in staging environments to reduce cost and noise, and this practice was inadvertently carried over to production
- No alerts were configured for changes to access control policies
This misconfiguration went unnoticed for weeks until a security staff member contacted them, informing them that sensitive files were publicly accessible. By that time, data exfiltration had already occurred.
Outcome of the Scenario
The data breach forced the organization into an unplanned disclosure after it was confirmed that sensitive client information had been publicly exposed. This not only damaged the company’s reputation but also attracted regulatory scrutiny under data protection laws, like GDPR, HIPAA, and CCPA. Authorities demanded detailed incident reports, evidence of controls, and corrective actions. The breach also incurred significant legal and compliance costs, including forensic investigations, legal fees, customer compensation, and regulatory fines, along with long-term expenses to strengthen compliance and security.
Root Cause Analysis Revealed
Root cause analysis revealed several underlying issues that contributed to the incident. Firstly, the organization lacked security automation; there were no automated checks or cloud security posture management (CSPM) tools in place to detect misconfigurations. Secondly, there was no centralized visibility into cloud spending or configurations, leading to siloed decision-making without proper oversight. Lastly, the staff had inadequate training and were unfamiliar with cloud-native security best practices, which led to critical mistakes during deployment.
What’s the Security Impact of Different AWS Misconfigurations?
Misconfigurations in AWS services lead to significant security breaches, data loss, unauthorized access, and operational disruptions. Issues often go unnoticed due to overly permissive IAM policies, public-facing storage buckets, or unavailable encryption. The following breakdown highlights common misconfigurations across key AWS services, RDS, S3, IAM, EC2, Lambda, and CloudTrail, along with the behavior they trigger and the resulting security consequences.
- RDS
| Misconfiguration | Resulting Behavior | Security Impact |
| RDS Protection Not Enabled | Database leak | Loss of all data if deletion protection is disabled or automated snapshots are misconfigured |
| Public Snapshot sharing | Database leak | Anyone can restore your DB instance and view data |
| Unencrypted Connections | Credential or Data Leakage | If an RDS DB does not require SSL connections, apps may connect in plaintext. Passwords and queries can be sniffed if the network layer is compromised. |
- S3 Buckets
| Misconfiguration | Resulting Behavior | Security Impact |
| S3 bucket storing logs or user data is accidentally set to public | Data breach | Sensitive data can be downloaded |
| Anyone on the internet, with or without AWS credentials, can access your S3 bucket | S3BucketPublicAccess Unauthorized data access | Anyone on the internet can read and write |
| ACL grants Everyone READ/WRITE | Spike in download traffic. Access from non-org IPs | Bypass policy protections |
| Versioning or Encryption disabled | Unusual overwrite/deletion of sensitive files. No audit trail | No rollback or data protection |
- IAM Roles and Policies
| Misconfiguration | Resulting Behavior | Security Impact |
| Over-permissive policies (Action: “*”, Resource: “*”) | Privilege escalation attempts. Execution of unusual or unauthorized actions. Abnormal spikes in API usage | Grants excessive privileges across all services and resources |
| Cross-account trust without conditions | API calls from unfamiliar or untrusted AWS accounts. Role assumptions from unexpected account IDs | Allows external principals to assume roles without restrictions |
| Lack of MFA enforcement | Role assumption without MFACloudTrail shows high-privilege actions from users without MFAIncreased access from unrecognized IPs or devices | Enables access with only a password or an API key, lowering identity assurance |
- EC2 Instances and Snapshots
| Misconfiguration | Resulting Behavior | Security Impact |
| Publicly shared snapshots | Unauthorized snapshot copy or sharing activity. Detection via snapshot usage in unrelated accounts. Audit trail anomalies in CloudTrail | Exposes sensitive data to any AWS user globally |
| Open SSH/RDP ports to the internet (0.0.0.0/0 on port 22 or 3389) | Brute-force attempts seen in VPC Flow Logs | Exposes EC2 instances to global brute-force attacks |
| Unencrypted AMIs and EBS snapshots | Data exposure in case of snapshot leak. No alerts, but security posture weakened (visible in security score or audits) | Data at rest is not protected, increasing risk of compromise |
- Lambda Functions
| Misconfiguration | Resulting Behavior | Security Impact |
| Execution roles with excessive permissions | Unauthorized changes to S3, DynamoDB, IAM, etc.CloudTrail logs show Lambda-initiated resource modifications | Lambda function can access or modify unintended AWS resources |
| Environment variables leak | Misconfigured Lambda functions may log environment variables (containing secrets or keys) to CloudWatchSecrets leaked through logs or runtime errors. Potential lateral movement if credentials are exploited | Anyone with read access to logs can extract secrets. Sensitive credentials or tokens may be exposed in logs or to unauthorized users |
| Triggered by public or unauthenticated sources | Unusual spike in invocations. High-frequency or abnormal invocation patterns from unknown sources | Enables attackers to invoke functions without authentication |
- CloudTrail
| Misconfiguration | Resulting Behavior | Security Impact |
| Logging disabled or not enabled in all regions | Gaps in audit trail during incident response. Anomalous actions (e.g., role creation, policy updates) go undetected | Critical events in certain regions go unmonitored |
| Logs not encrypted or stored in insecure locations | Compromised audit integrityPotential leak of sensitive operational data | Log data is exposed to tampering or unauthorized access |
| No multi-account trail consolidation | Incomplete visibility across environments. Missed detection of cross-account privilege escalation or abuse | Disconnected logs across accounts make it difficult to trace events |
Best Practice
Misconfigurations often arise from weak configurations that compromise visibility, control, or access. To prevent these misconfigurations from leading to security incidents, it is crucial to implement continuous monitoring, automate remediation, and strictly adhere to the principle of least privilege, along with established security best practices.
Implementation to Address Cloud Misconfigurations
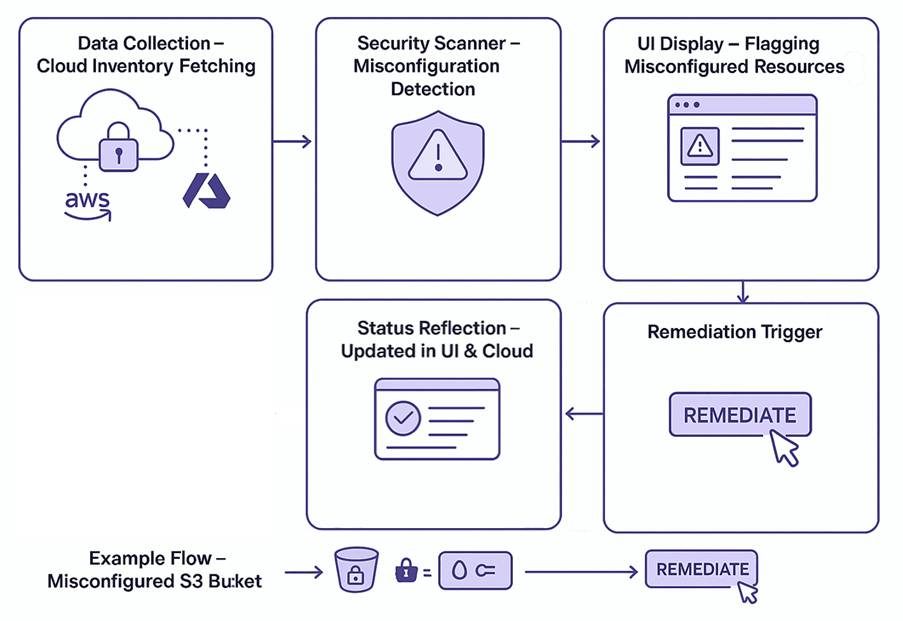
1. Data Collection with Cloud Inventory Fetching
Modules involved: Core ingestion pipeline
Cloud Connectors authenticate with an organization’s cloud accounts to securely access and retrieve metadata from various cloud services. This metadata includes information on Logging and monitoring settings (example: CloudTrail status, log destinations, CloudWatch metrics, and alarms) Identity and Access Events (example: Recently assumed roles, failed login attempts, MFA status, and last activity timestamps), Tagging and Resource Group Metadata (example: User-defined tags, cost allocation tags, environment markers etc.), and more. The collected data is then normalized into a consistent format and stored in an internal asset store for further analysis and processing.
2. Security Scanner and Misconfiguration Detection
Modules involved: Cloud Security Posture Management (CSPM), Cloud Infrastructure Entitlement Management (CIEM), Cloud Security Posture Anomaly (CSPA).
Static security rules, like the requirement that “S3 buckets must not be public,” are managed within a centralized rule engine. This engine continuously assesses cloud resource configurations by comparing them with predefined security baselines, such as CIS benchmarks, to identify any policy violations or misconfigurations.
3. Flagging Misconfigured Resources
Modules involved: CSPM/CIEM/CSPA UI layer
The UI layer across CSPM, CIEM, and CSPA modules visually flag misconfigured resources. It queries misconfiguration data in real-time and displays affected resources using clear, context-driven visuals, such as warning indicators, severity tags, and categorized listings, making it easier to identify and prioritize issues directly from the interface.
4. Remediation Trigger for Launching CSRM Module
Modules involved: Cloud Security Remediation Management (CSRM)
Clicking “Remediate” triggers a routing mechanism to the CSRM module. As a result, the system fetches misconfiguration metadata, pre-built remediation template, and necessary inputs from the user.
5. Status Reflection in UI & Cloud
Modules involved: Scanner and User Interface
After remediation, the issue is marked as “Resolved.” The resource appears healthy in the next scan, the updated configuration is confirmed with the cloud provider, and the UI refreshes the view to reflect the new status.
Example Flow: Misconfigured S3 Bucket
- S3 bucket with PublicAccess = True is found
- CSPM flags it and shows a “High” severity issue
- User clicks “Remediate”
6. Security Considerations
All remediation actions are authenticated and logged.
Secure Your Cloud Before It’s Too Late
With Saner CSPA and CSPM, you don’t have to guess. You get real-time visibility, automated checks, and actionable insights to fix misconfigurations before attackers find them.
What does Saner CIEM, CSPM, and CSPA Detect?
Saner Cloud’s security tools (CIEM, CSPM, and CSPA) work together to identify various misconfigurations, risky access permissions, and unusual activities in the cloud. CIEM specializes in detecting over-permissioned identities and abnormal user behavior. CSPM continuously monitors the cloud infrastructure for configuration errors and compliance violations. CSPA focuses on analyzing anomalies that may indicate emerging threats. Together, these modules provide comprehensive visibility and control over your cloud environment.
Cloud Infrastructure Entitlement Management (CIEM)
IAM (AWS) and Entra ID (Azure)
CIEM identifies risky Identity and Access Management issues such as:
- Permission Drift: Users, Policies, Roles, and Groups with excessive access levels
- Abandoned Entities: Inactive Users and Roles, Empty Groups, and Unused Policies
- Anomalous Behavior: Identities used at unusual times or with abnormal frequency by tracking Critical Activities
- MFA Tampering: Users disabling Multifactor Authentication or showing sudden changes in login behaviour
These detections help spot misconfigurations and potential threats before they escalate.
Cloud Security Posture Management (CSPM)
AWS and Azure
CSPM helps continuously monitor cloud misconfigurations such as:
Misconfigured Storage: Publicly accessible S3 buckets, Azure Blob Containers, or GCP Buckets
Unrestricted Ingress/Egress: Overly permissive Security Groups, NSGs, or Firewall rules
Unencrypted Services: Databases, Disks, and Communication channels without encryption at rest/in-transit
Compliance Violations: Deviations from industry standards like CIS, NIST, PCI DSS, SOC2, or HIPAA
These insights enhance visibility and ensure your cloud environment stays secure and compliant.
Cloud Security Posture Anomaly (CSPA)
Saner CSPA focuses on detecting any deviations in your cloud posture, such as:
- Sudden Misconfiguration Spikes: Rapid increase in misconfigured resources (e.g., multiple storage buckets becoming public simultaneously)
- Unexpected Policy Changes: Unusual modifications to IAM policies, firewall rules, or encryption settings
- Deviation from Baseline: Configuration states diverging from known-good baselines over time
- Time-Based or Behavior-Based Anomalies: Access or configuration changes happening outside normal operational hours or patterns
CSPA helps uncover stealthy threats and errors by flagging behavior that deviates from expected posture norms.
Go Further
Saner Cloud is a comprehensive solution designed to help organizations effectively manage their cloud operations. Key features of the product include asset exposure, posture management, posture anomaly detection, identity and entitlement management, and remediation management.
Documentation is organized to help you quickly and efficiently find the information you need, whether you’re troubleshooting, learning how to use specific tools, or seeking in-depth knowledge about the product suite.
Discover how Saner CSPM detects misconfigurations across your cloud accounts. Schedule your trial today for a more comprehensive experience!

