Over 79 percent of cloud buyers reported using multicloud providers in the third quarter of 2024. As cloud adoption scales, organizations are spreading infrastructure across AWS, Azure, GCP, and others to meet uptime, performance, and vendor diversification goals. But what begins as a strategic advantage often introduces security inconsistencies and operational blind spots.
Security teams face overlapping identities, varying configuration models, and a flood of platform-specific controls that rarely align. A misconfigured S3 bucket in one environment or an overprivileged IAM role in another may go unnoticed without unified visibility. Meanwhile, audit requirements demand consistent policy enforcement, even as each cloud provider has a different definition of compliance and telemetry.
The next sections outline the primary difficulties of keeping multicloud environments secure and provide clear strategies to tackle these issues, including managing access, preventing configuration changes, detecting threats, and handling security tasks across different providers.
Key Security Challenges in Managing Multicloud Environments
Operating across multiple cloud providers introduces security management complexity that often exceeds what traditional security tooling and processes can handle. The fundamental challenges stem from inconsistent control planes, fragmented identity structures, and siloed logging mechanisms across platforms.
1. Inconsistent Identity and Access Management (IAM)
Each cloud provider implements IAM differently. AWS uses IAM roles and policies, Azure defines role-based access control (RBAC), and GCP follows a resource hierarchy with identity binding. Without a normalized view, it becomes difficult to assess who has access to what resources and whether those permissions align with least-privilege principles. Overprivileged accounts, stale service identities, and excessive cross-account access are common and often go unnoticed in siloed environments.
2. Configuration Drift and Misalignment
Teams often apply baseline configurations during provisioning, but over time, infrastructure as code (IaC), manual changes, or service updates cause drift. In multicloud settings, configuration baselines are not only difficult to enforce, they vary significantly by provider. For instance, default encryption or firewall rules differ between AWS S3 buckets, Azure Blob storage, and GCP Cloud Storage. Inconsistent baselines across environments introduce gaps that attackers can exploit easily.
3. Fragmented Visibility and Monitoring
Logging, telemetry, and security signals are scattered across providers. While AWS CloudTrail, Azure Monitor, and GCP Cloud Logging all provide telemetry, none of them offer a comprehensive view from the outset. Security operations teams must stitch together logs, normalize data formats, and correlate events across sources. Without consolidated visibility, incident detection and forensic investigations become delayed and error-prone.
4. Policy Management at Scale
Enforcing consistent policies for access control, data protection, and workload hardening is complicated in multicloud. Security frameworks such as CIS Benchmarks or NIST 800-53 may be partially supported on each platform, but not uniformly. Attempting to enforce global policies using provider-specific tooling leads to coverage gaps. Scaling policy as infrastructure expands becomes unmanageable without centralized orchestration.
5. Increased Attack Surface and Shared Responsibility Complexity
As environments grow, the attack surface expands. APIs, workloads, serverless functions, and third-party integrations multiply across platforms. Cloud-native vulnerabilities differ from traditional on-prem risks. Meanwhile, each provider defines its shared responsibility boundaries differently, leading teams to often misinterpret the provider’s security versus their own security needs. Misunderstanding these divisions leads to gaps in threat modeling and control ownership.
Strategic Controls for Multicloud Risk Mitigation
Multicloud environments introduce structural complexity that security teams must address with scalable, platform-agnostic strategies. The approaches below focus on creating control consistency, minimizing misconfigurations, and enabling rapid incident response across AWS, Azure, GCP, and other platforms.
a. Establish Unified Visibility
Asset sprawl is a common byproduct of multicloud adoption. Without full awareness of workloads, services, configurations, and identities across providers, security risks often go unaddressed.
Inventorying cloud assets requires more than static asset management databases. Agentless scanners, API-based discovery, and CSPM platforms can continuously gather information from control systems and organize the results across different accounts and providers. Granular inventory should include network exposure, encryption status, patch levels, and identity bindings.
Best Practices:
- Use native APIs (e.g., AWS Config, Azure Resource Graph, GCP Asset Inventory) to ingest real-time state data.
- Apply CSPM tools to continuously map posture against frameworks such as CIS Benchmarks or NIST 800-53.
- Track ephemeral assets such as containers and serverless functions with time-bound visibility.
b. Standardize Configuration and Compliance Controls
Provider-specific defaults vary significantly, which makes baseline hardening and compliance enforcement inconsistent. Security teams need to codify standards and apply them uniformly through automation.
Using configuration baselines that match CIS Benchmarks and linking them to the Cloud Security Alliance’s Cloud Controls Matrix (CCM) helps create a consistent compliance approach across different environments. Infrastructure as Code (IaC) can codify these controls for automated validation at provisioning time.
Best Practices:
- Validate cloud templates with policy-as-code engines (e.g., OPA, Checkov, Regula).
- Integrate IaC scanning into CI pipelines to block deployments with misconfigured resources.
- Use remediation-as-code to enforce consistency post-deployment.
c. Centralize IAM Oversight
Disjointed identity and access systems across clouds create blind spots. Multiple identity sources, unlinked accounts, and varied RBAC implementations make it difficult to maintain consistent access control.
Federated identity models using SAML or OIDC can centralize authentication. CIEM (Cloud Infrastructure Entitlement Management) platforms help map permissions, detect privilege escalation paths, and revoke unused entitlements.
Best Practices:
- Aggregate IAM data across clouds to identify toxic combinations of permissions.
- Detect overprivileged roles, stale service accounts, and shadow admins.
- Apply JIT and time-bound access to reduce standing privileges.
d. Automate Detection and Remediation Workflows
Manual response is unsustainable across multicloud environments with high asset volume. Automation reduces the window from threat detection to validated mitigation.
CNAPP platforms allow teams to combine misconfiguration detection with auto- remediation and trigger workflows for containment, alerting, or ticketing.
Best Practices:
- Integrate CNAPP or SOAR platforms with posture management and IAM telemetry.
- Define rule-based automation to isolate misconfigured resources or revoke high-risk permissions.
- Audit all remediation actions for traceability and compliance reporting.
e. Build for Zero Trust Across Clouds
Flat networks and implicit trust models increase blast radius in case of compromise. Applying Zero Trust principles across cloud environments enforces strict boundaries around identity, data, and workload access.
Network segmentation, service identity verification, and granular access policies limit lateral movement and reduce exposure.
Best Practices:
- Enforce mutual TLS and certificate-based identity for service-to-service traffic.
- Apply microsegmentation to restrict east-west communication in virtual networks.
- Use context-aware access controls that factor in identity, device posture, and workload risk.
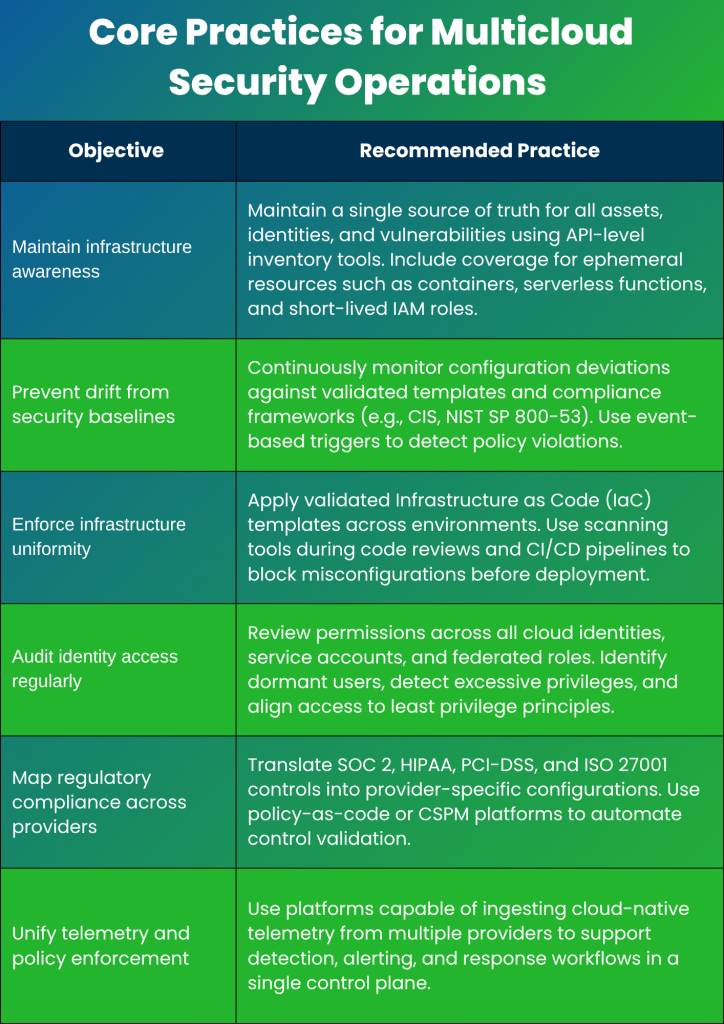
Operational Consistency Starts with Foundational Hygiene
Security maturity across multicloud environments depends on disciplined operational practices. Variability in provider defaults, identity models, and telemetry formats can expose gaps if foundational hygiene is not maintained. The following practices serve as guardrails to prevent misconfiguration drift, policy fragmentation, and oversight lapses across AWS, Azure, GCP, and other cloud platforms.
Core Practices for Multicloud Security Operations
How Saner Cloud Supports Multicloud Security Operations
Managing multicloud security requires consistent visibility, continuous posture evaluation, and policy-aligned remediation across cloud environments. Teams need a solution that connects the dots between misconfiguration detection, entitlement oversight, and compliance automation, without toggling across disparate tools.
Saner Cloud is purpose-built for this requirement. It supports multicloud security operations by bringing unified visibility, prioritization, and response together across AWS and Azure accounts.
Integrated Capabilities That Matter:
- Continuous Exposure Analysis: Saner Cloud continuously monitors configurations, entitlements, and anomalies by collecting telemetry across providers. It identifies resources exposed to external networks and maps findings to frameworks such as CIS, HIPAA, and NIST using its built-in compliance engine.
- Multicloud Misconfiguration Management: Using its CSPM module, Saner Cloud conducts posture evaluations and flags deviations from security baselines. Issues such as disabled MFA, overly permissive roles, or exposed storage instances are detected and prioritized with confidence scoring.
- Context-Aware Remediation: Security teams can configure remediation workflows directly within the Saner dashboard. Actions such as isolating misconfigured resources, revoking excessive permissions, or applying remediation-as-code are fully traceable for audit purposes.
- CIEM and IAM Oversight: Saner Cloud’s CIEM dashboard maps user and service entitlements across clouds and highlights risk-prone privilege paths. Teams can monitor inactive accounts, over-permissioned roles, and unused identities in one place.
- Unified View with AI Insights: Dashboards provide centralized insight into posture, exposure, and anomalies. Teams can prioritize actions using visual risk distribution, anomaly heatmaps, and integrated AI assistance for reporting and triage.
Saner Cloud simplifies security across complex cloud environments through a prevention-first model. Rather than reactively chasing misconfigurations or identity sprawl, teams gain a single control plane to manage, assess, and respond to cloud security risk at scale.
Securing What Spans Across Cloud Boundaries
Managing multicloud security presents a growing operational challenge. As environments expand across providers, inconsistencies in identity management, configuration enforcement, and policy control often surface only after incidents occur.
Solving for these gaps requires more than reactive detection. Teams need proactive methods for managing posture, access, and exposure across all accounts and services, from build to runtime. Programs that prioritize control standardization, centralized visibility, and policy-driven response are better equipped to address both current risks and emerging cross-cloud attack paths.
Saner Cloud supports this shift by helping teams monitor, assess, and act across AWS and Azure through a single interface. To see how it fits into your multicloud security strategy, request a tailored walkthrough of Saner Cloud’s unified security operations platform.

