In a messy age of cyber-attacks and growing number of vulnerabilities, IT and security teams are as busy as the stakes are high. As attacker dynamics shift, security strategies often adjust reactively. The resulting turmoil gives experienced professionals trouble keeping up with these weaknesses and attackers. Artificial Intelligence may be able to lend a hand.
How can AI help?
It stops the reversion to past norms by detecting early indicators of regression, such as unpatched vulnerabilities with known exploits, inaccurate asset criticality mapping, deprioritized vulnerabilities, and static CVSS scores of vulnerabilities. It identifies gaps where exploitability data, asset exposure, and organizational context are ignored, leading to delayed remediation of high-risk exposures.
If we are seeking short-term normalcy, the most significant concern about not using AI is a missed window for change in tackling and managing burgeoning vulnerability backlogs with reduced momentum.
Let’s go a bit further.
When a vulnerability exposes itself, it introduces the potential for exploitation. It becomes a serious threat. Here is the relationship: Threat = Vulnerability × Exposure, so Risk = Probability of Threat (vulnerability × exposure).
This relationship offers a basic understanding of how risk occurs. Understanding its practical application depends on how well we quantify and prioritize vulnerability risk.
CVSS Drawbacks
CVSS scores fall short here. Here are some of the technical limitations of CVSS. It keeps the entire vulnerability management process in disarray, and outcomes are unfavorable.
- CVSS base scores are static. They do not dynamically reflect the presence of public exploits, proof-of-concept exploit code, or active exploitation in the wild
- As the scores are static, they are suitable for modern day attack surfaces, and this can increase the chances of exploitability over time
- CVSS treats every asset equally. It ignores the severity of the vulnerability to the organization, risk exploitability, or device risk. They treat a high-risk vulnerability the same across all devices.
- Organizations rely on CVSS base scores but rarely implement them in a continuous vulnerability management workflow.
- A CVSS score of 9.8 might represent a technically severe vulnerability with zero known exploits. Whereas a 7.2 score might have weaponized exploits
- CVSS uses CIA (confidentiality, availability, integrity), and this is not reflective of operational risks such as exploit potential
This is where AI becomes indispensable.
It analyzes the interplay between vulnerabilities, asset exposures, and real-world exploitability. AI enables organizations to move beyond simple risk models (like CVSS) by contextualizing and prioritizing vulnerabilities based on actual risk, not theoretical severity.
This helps to focus remediation efforts on what truly matters, reducing the probability of an attack. We must aspire for a better path led by AI.
AI Impact
AI-driven, risk-based prioritization is critical for predictive vulnerability management. Predicting vulnerabilities before they are exploited is a strategic imperative. The shift is crucial because it has specific technical justifications.
- Huge vulnerability backlogs: Millions of vulnerabilities are disclosed every year and remediating them with limited resources is not feasible. AI models can recognize which vulnerabilities pose real-world challenges based on their exploitability, impact, and business context.
- Risk contextualization: Traditional risk prioritization models rely on the CVSS score alone. A risk-based model can incorporate asset criticality, business impact, and context, continuously updating security intelligence to dynamically correlate them to prioritize vulnerabilities with actual risk.
- Security intelligence integration: Static models cannot continuously ingest and react to dynamic vulnerability data. AI-driven models can continuously take in the latest and updated security intelligence feeds and adjust prioritization more dynamically.
- Automate prioritization: Manual risk prioritization is time-consuming and error-prone. Automated risk categorization and enrichment of vulnerability data using AI can accelerate remediation flow.
Towards Smarter Prioritization
Smarter prioritization is not about operating in abstraction. It does not ignore the nuances. Because, if you look at the earlier equation, Risk = Probability of Threat (Vulnerability × Exposure), risk is not just about having a vulnerability.
It depends on how likely a threat is to exploit it (Probability of Threat), how exposed that vulnerability is to attackers (Exposure), and where it resides (which influences both exposure and impact). This means the same vulnerability can pose different levels of risk.
To solve this, we must combine raw vulnerability data with business context, dynamic security intelligence, MITRE ATT&CK mappings, ML-powered Exploit Prediction Scoring Systems (EPSS), and AI-driven risk categorization algorithms to prioritize vulnerabilities and support targeted remediation actions.
This combination is non-negotiable. The following are the reasons:
- Though raw vulnerability data provides the foundation, it lacks situational awareness, without which we won’t be able to manage large vulnerability backlogs, might miss high-risk ones, or end up remediating low-risk vulnerabilities
- You must add business context to understand asset criticality and its operational importance.
- Security intelligence gives insight into active exploits (& its POCs), likelihood of exploitation, trending vulnerabilities & attack campaigns
- MITRE ATTACK mapping helps to technically categorize vulnerabilities based on their exploitability, automatability, and technical impact
- AI-driven risk categorization to reference factors such as Malware Vulnerability Enumeration, CISA KEVs, Google Project Zero Findings, vendor advisories, exploit databases, etc.
What’s more?
This approach is needed to sustain posture resilience and reduce infrastructure (or environmental) stress, meaning how well enterprise IT security teams can maintain security posture when vulnerabilities emerge.
They can steer through or adjust their posture based on continuous scanning and security intelligence. E.g., a highly secure IT environment (strong security controls, integrated VM platform) allows precise adjustments with minimal deviations from secure baselines. In contrast, a lowly secured IT environment (unpatched/misconfigured systems, siloed tools) makes posture control slow and unmanageable.
You will be able to handle internal and external pressures acting on the organization to prioritize vulnerabilities, such as business priorities, compliance deadlines, emerging attacks, or audit needs.
How does it help?
The combination also helps in more scenarios.
To consider one such example, you might want to reprioritize remediation to tackle a zero-day exploit or shift focus to respond to a critical business event, such as an M&A (merger and acquisition), as it brings more IT assets to your environment. Such situations test your VM process and the prioritization capabilities to sustain your security posture.
The second example is managing legacy systems, shadow IT, and business-critical systems vulnerabilities. The combination helps to orient security posture and reduce the constraints of this operational load by avoiding any overcorrections in posture.
To emphasize the importance of this combination further, it reduces the attack surface area, reducing exposure. It not only addresses vulnerability but also how vulnerability and its exposure trend over time. It keeps the probability of an attack low, through dynamic posture adjustments such as rebalancing patch schedules. You will also be able to stand strongly under the pressure of rising attack probabilities, without destabilizing core operations.
The Role of EPSS
One of the most prominent factors in this combination, which we have been discussing so far, is the role of EPSS (Exploit Prediction Scoring System). EPSS uses ML models to include real-world exploitation indications and vulnerability attributes to predict the probability/likelihood of exploitation.
Here is a quick look at its efficiency and coverage in the real world:
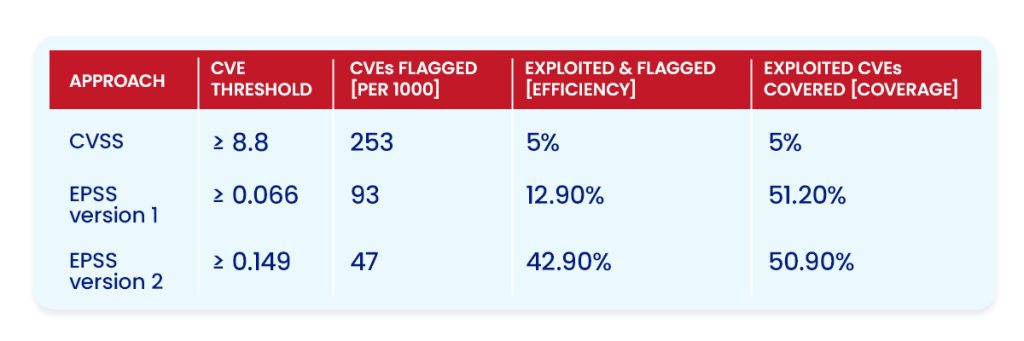
In this table, out of the 253 picked by CVSS, only 5% are being exploited, so you are fixing vulnerabilities that aren’t so dangerous. But you do catch half of the threats (50.70%).
Version 1 of EPSS picks 93 instead and targets around 12% that are exploited, which is good targeting. However, version 2 of EPSS picks only 47 and targets 42.9% of those actively exploited, which is brilliant. And still, you end up catching half the threats like other methods. So, with EPSS version 2, you fix only the dangerous ones, spend half the time and effort (just 47 instead of 253), optimizing efforts more efficiently.
Enter SSVC Risk Prioritization
The data from the MITRE ATTACK mapping, Security Intelligence, ML-driven EPSS, and AI-driven Risk Categorization Algorithm must be effectively correlated. This is needed to technically categorize vulnerabilities based on their exploitability, automatability, and technical impact (which CVSS cannot do).
The system uses the SSVC model to correlate for prioritization, which far surpasses CVSS effectiveness.
When deciding which vulnerabilities to fix first, the SSVC model doesn’t just look at technical risk (like CVSS or EPSS scores). It also considers the business context and what security protection is in place. It gets this information from enterprise asset inventory, which helps it understand which device or software is exposed or important for business, and through the OCIL questionnaire, which learns about the security controls in place (is the firewall active, or is MFA used, etc.).
Know more about SSVC risk prioritization.
The Integration – enabling the predictive model
This is not a trapped or siloed IT system, because it is not about scoring vulnerabilities. The system and the SSVC model are learning and aligning with business realities. Here is why it is a unified system with a strong AI-ML backbone.
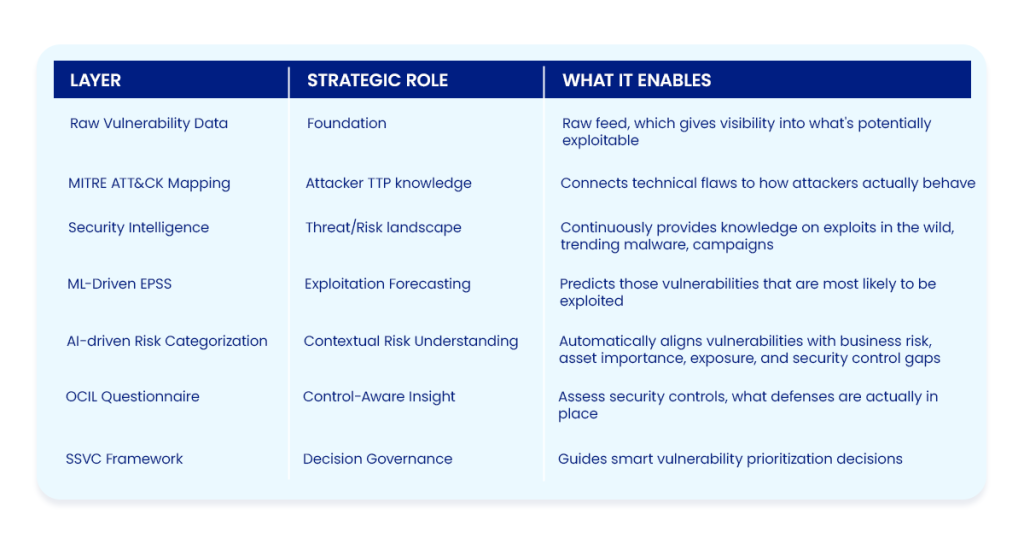
Each layer complements the other. The system shifts and adapts to business priorities and risk patterns. It aligns with your risk language and clarifies what the real exposure is today. Risk prioritization is done with accountability, you can clarify to the audit why you prioritized a vulnerability over the other, backed by intelligence.
The Big Shift in Managing Risk
More than just a technical enhancement, it’s a significant shift. It redefines the way you look at vulnerability risk, aligning to the business context and backed by intelligence from asset criticality, business impact, and continuous feeds of security intelligence. This alignment ensures that risk decisions are defensible.
E.g., when a critical business application faces a known exploit, the AI system can justify prioritization based on financial impact and customer-facing exposure. Not just CVSS scores. The C-level and auditors need this level of transparency.
It’s not just defensive, where you scan, patch, and expect it to be done. AI-driven risk prioritization provides predictive assurance by anticipating the attack before it happens.
E.g., with Exploit Prediction Scoring System (EPSS) and continuous security intelligence, you can detect high-probability exploits even before proof-of-concept (PoC) code is published. This makes it possible to act before attackers can capitalize.
This minimizes exposure windows, reducing MTTR.
By synthesizing variables such as asset exposure, business criticality, active exploits in the wild, security controls already in place, MITRE ATTACK mappings, and exploitability scores, it enriches risk with context and ensures targeted remediation.
E.g., imagine managing 1,000,000 (1 million) vulnerabilities across your enterprise. Instead of manually triaging or patching based on outdated CVSS scores, the AI system can tell you to fix those 100, which pose real risk.
These examples are a full display of why this system is evangelistic. It upgrades risk prioritization to be more adaptive and AI-native. It’s “what’s next” in vulnerability management.
This is critical to overcome three compounding challenges. The surge in vulnerabilities, declining confidence in CVSS, and lack of control over remediation. To overcome these stressors, AI-ML-driven risk prioritization is the only way out. It is accountable and sustainable.


