The Great Perils of FPhishing
Every year, many organizations fall victim to phishing attacks. Tens of millions of phishing emails make it to your inbox and are clicked and opened. A recent study by the Anti-Phishing Working Group (APWG) has revealed just how much we have been victim to phishing over the years. The study reveals that in the first quarter of 2016, phishing has surged by 250 percent. With keyloggers possessing advanced tracking components to aim specific information, attackers using phishing methods globally, have become hostile in 2016.
Phishing is a fraudulent attempt in which the attacker tries to steal personal information such as login credentials, social security number, credit card number or password. They masquerade as a trustworthy entity or person in an email or other communication medium.
What to look for in a phishing email
We receive many e-mails every day. In a hurry to check it all, we often don’t check the legitimacy of the e-mail, its sender or its content. We end up clicking on one of these e-mails or download an attachment in the mail and become a victim of the phishing attack.
A phishing e-mail has many characteristics such as generic greeting, personal information requests, fake links, attachments, the tone of urgency, usage of common phishing language, brand spoof, and suspicious email address. These are the characteristics which we should pay attention to but we end up ignoring.
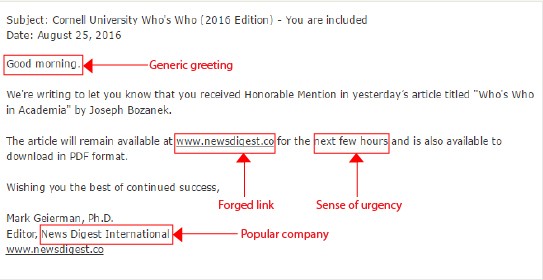
Given below is an example of a phishing email:
(image source: http://www.it.cornell.edu/)
Generic greeting: Phishing emails are typically sent in bulk. To save time, cyber criminals use a generic tone of introduction/ greeting such as “Hello Winner” or “Good Morning”. This way they don’t have to enter the names of each recipient.
Fake links and attachments: The aim of a phishing attack is usually to get you to click a link, pop-up message or to download an attachment. Links embedded with phishing messages direct you to fraudulent websites. Websites that include spelling errors such as www.myshap.com instead of www.myshop.com, incorrect URL, URLS with unnecessary symbols such as @,! etc., are signs of a bogus link. Even if a link has a name that you recognize doesn’t mean that it is real.
Popups can release malware into your PC and infect it.
Be extremely cautious of such links and attachments. If you are not sure about the legitimacy of the links and attachments in the mail, don’t click on it.
Attempts to obtain your personal information: No company will ask you for your personal information without a reason. Phishing emails are sent with a purpose to trick you into providing personal information. Spammers and fraudsters mail you asking your personal details such as social security number, PIN number, bank account number, debit or credit card number or birthday. They may send the mail disguising as an employee of a bank, financial information or a reputed firm. If you receive an email requesting such information, it is most likely a phishing attempt. Don’t reply but simply ignore such e-mails.
The sense of urgency: To make you believe that an email is true, attackers send an email with a message that seems to be urgent such as “your account is suspended” or “unauthorized login attempt.” Thinking that it is a mail that requires a quick action, you click on the link. You provide your information and the attackers thus succeed in their attempt. The phisher is taking advantage of your worry to trick you into providing confidential information. Beware of such subject lines.
Hoaxing popular companies: Phishers use graphics or names of well-known companies that appear to be genuine but may actually take you to malicious sites. Don’t fall for the brand hoax.
Phishing language in e-mails: Some of the common phishing language in emails are “Verify your account” or “Update your Password”. A genuine business will never send just an email requesting you to update your account or share information regarding your login credentials. Read your emails carefully and report anything that appears suspicious.
The sender’s e-mail address: The sender’s email address if the first giveaway of a phishing attempt. Even if the e-mail looks legitimate, the address often seems to look odd. For example, an email from Nissan with an e-mail address such as [email protected] is evidently not an email from Nissan. Don’t trust the display name and don’t open if you don’t trust the address.
Bogus phone calls: Bogus phone calls are also a part of phishing. In case you are not sure about the caller, the caller’s number, or phone number, then ignore the call or hang up before they try to get you to sharing personal information. Don’t share any personal information via phone calls.
Ensure that you have the right endpoint security solution installed on your endpoints for protection against phishing attacks.
– Rini Thomas