SanerNow CVEM
Continuous Vulnerability and Exposure Management
Secure your modern IT infrastructure with a bleeding-edge attack surface platform
Why is your Vulnerability or Exposure Management Solution Not Effectively Reducing your Attack Surface?

Lack of Deeper Insights into the IT Infrastructure
IT security teams do not have deeper visibility over the IT infrastructure. Traditional tools typically provide limited view to hardware and software details with insufficient actionable insights. As a result, IT security teams overlook the most obvious attack vectors that can lead to massive security breaches.

Vulnerabilities Beyond CVEs are Left Out
Traditional vulnerability and exposure management solutions focus only on managing CVEs or software vulnerabilities and leave out the other crucial security risks like IT asset exposures, misconfigurations, deviation in security controls, and security posture anomalies.

Lack of Integrated Remediation Capabilities
Most traditional tools do not provide integrated patching to remediate the vulnerabilities. This leaves the vulnerabilities to prevail in the network, opening gateways for attackers to exploit.

Siloed Interfaces and Multiple-Point Solutions
Tradition tools still rely on siloed interfaces and multiple tools to execute each step of vulnerability and exposure management. The process of traversing across swivel chair interfaces is hard, time-consuming, and consumes a lot of manual effort.
With all these challenges, the larger goal of preventing cyberattacks and building a robust security risk and compliance posture is flawed and slowed down. IT security teams need an attack surface management tool that looks from the weakness perspective and can manage vulnerabilities, exposures, and beyond, provides integrated remediation, and enables you to achieve continuous and automated prevention of cyberattacks under one roof.
Spot the Difference with Continuous Vulnerability and Exposure Management
See for yourself why your team should switch away from traditional vulnerability management and take a whole new approach to cyberattack prevention and attack surface management.
Traditional Vulnerability Management
Continuous Vulnerability and Exposure Management
Visibility to limited IT asset details with insufficient actionable insights
Holistic and deeper visibility into IT infrastructure with clarity on actionable insights
Siloed interfaces & multiple-point solutions approach
Unified, single-solution approach to visibility, detection, assessment, prioritization, and remediation
Rely on a separate tool for remediation
Integrated and seamless patch management capability for timely remediation
Discover only CVEs or software vulnerabilities
Detect vulnerability, misconfigurations, asset exposures, missing critical security patches, and security posture anomalies within a single console
Lack of remediation controls to fix security risk exposures
Remediation controls beyond patching to fix the vulnerability and other security exposures
Manual methods and irregular processes
Built for automation, achieving continuous compliance
Irregular scans and no clarity on real-time risk posture
Continuous scan and up-to-date risk posture assessment
Prolonged Patch Management Lifecycle taking months to complete
Rapid, continuous, and automated patch management lifecycle
Lack of capabilities to build queries to detect and respond to security risks
Build custom queries to detect security risks and deploy instant response
OS and device-specific support
Heterogeneous and device-agnostic support
Multiple agents
Single, light-weight, multifunctional agent
Lack of API support & eco-system integration
Native API support and eco-system integration
Ineffective attack surface management
Rapid and effective attack surface management
Lack of weakness perspective for cyberattack prevention
Weakness perspective incorporated into managing security risks.
Segregated security & IT goals
Unified security and IT goals
SanerNow CVEM Framework Supercharges Enterprise Attack Prevention Strategy
SecPod SanerNow’s philosophy is offering simplicity and automation to make the job of IT security administrators significantly better, everyday.
SanerNow’s Continuous, Automated, & Advanced Vulnerability and Exposure Management Solution to Build an Unbreachable Defense
SanerNow reinvents vulnerability and exposure management with a broader approach to vulnerabilities, integrated remediation, rapid detection techniques, vast security intelligence, and end-to-end automation, all under one roof.

Manage Vulnerabilities, Exposures and Other Security Risks in a Single Unified Platform
Go beyond managing CVEs and focus on other security risks as well. SanerNow manages software vulnerabilities, misconfigurations, deviation in security controls, IT asset exposures, security posture anomalies, and various security risks from a single centralized console.

Mitigate Vulnerabilities On-Time with Integrated Remediation
Remediate vulnerabilities and other security risks quickly with integrated patching. Perform vulnerability assessment and remediation from the same console and reduce risk exposure to a large extent. Along with patching, leverage other security controls and mitigate numerous security risks.

Experience the Leading Edge of Security Innovation
Leverage the weakness perspective, machine learning, statistical analysis, and deviation computation methods to gain holistic visibility over your IT and detect outliers. Through Industry’s fastest scans, world’s largest security intelligence library, end-to-end automation, and truly integrated natively built solution, take vulnerability management to a whole new level

Automate End-to-end Tasks and Establish a Continuous Routine
Automate all the tasks from scanning, detection, assessment, and prioritization, to remediation and make vulnerability management a hands-free process. Establish a continuous routine to manage vulnerabilities and security risks and keep cyberattacks at bay.
Visualize & Normalize

SanerNow
AE
Continuously monitor IT assets

SanerNow
CPAM
Take control over attack vectors
Detect & Prioritize

SanerNow
VM
Detect CVEs and other risks

SanerNow
CM
Achieve audit-ready compliance
Remediate & Mitigate

SanerNow
PM
Patch OSs & 3rd party applications

SanerNow
EM
Harden devices beyond patching
Continuous Vulnerability and Exposure Management Software that is Sleek, Simple, yet is the Most Powerful
Run Real-Time Scans and Discover IT Asset Exposures
SanerNow runs regular monitoring scans on all your software and hardware assets. Discover malicious IT assets and Blacklist them from your network to improve security.
Gain Holistic Visibility into IT Infrastructure and Eliminate Outliers
Get collective and deeper visibility over you IT infrastructure. Spot the most obvious attack vectors including outliers in the network, unapproved software & devices, incorrectly configured security controls and much more, and eliminate them instantly.
Manage Vulnerabilities, Exposures and Beyond, All Under One Roof
Detect and remediate software vulnerabilities, IT asset exposures, misconfigurations, missing patches, deviation in security controls, and security posture anomalies from a single centralized console.
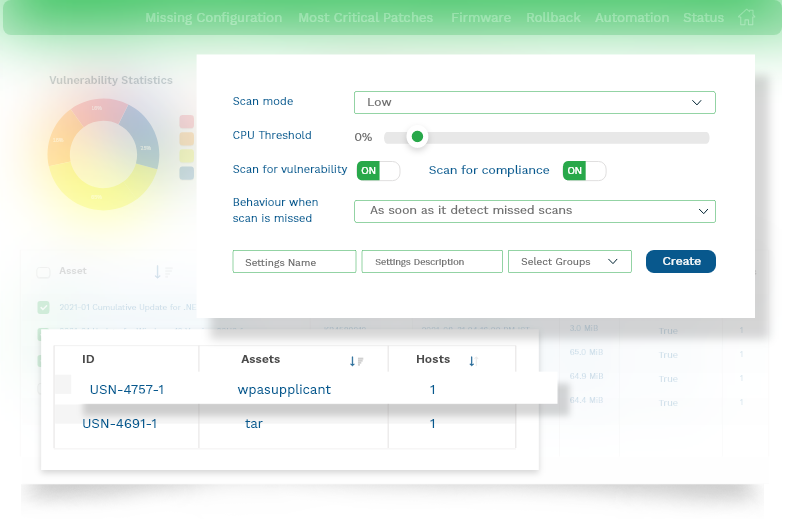
Blazing-Fast Scans to Detect Vulnerabilities, Exposures and Security Risks
SanerNow runs the continuous and the fastest scans in under 5 minutes. All this without consuming excessive network bandwidth or system resources.
Accurate Detection Powered by Vast Security Intelligence
SanerNow is powered by its home-grown world’s largest security intelligence library with 160,000+ vulnerability checks for accurate detection with near-zero false positives.
Remediate Vulns and Exposures On Time With Integrated Patch Management
Mitigate the vulns, exposures, and other security risks instantly with integrated patch management and reduce your attack surface. SanerNow supports patching for all major operating systems like Windows, Mac, Linux, and 450+ third-party apps.
Go Beyond Patching and Leverage Additional Remediation Controls
Mitigate numerous security risks with a plethora of security controls available in SanerNow. Eliminate attack surface to a larger extent with remediation controls available in the same console.
Harden System Configurations and Abide by International Compliance Standards
Detect deviation in compliance, fix misconfigurations and harden devices. Assure continuous compliance with major industry benchmarks, including HIPAA, PCI, NIST, and ISO.
Seamlessly Manage Millions of Risks
Prioritize millions of risks detected in your IT infrastructure based on business context, vulnerability intelligence, MIT&RE attack mapping, improved version of EPSS, and our inbuilt unique risk categorization algorithm
Global Enterprises trust SanerNow to Secure & Manage their Attack Surface
– Pradeep B
Consultant, NCIIPC, Govt. of India
– Ernest Darko Mensah
Managing Director, Spearhead Networks MSP
SanerNow has multiple modules like patch management, vulnerability management, compliance management, EDR, software deployment. Today, with rise of cyber risks it’s very important to have a single tool/console to get a visibility into all modules. It’s easy to identify, detect, and patch at the same time.
– Sumit Birajdar
Infosec Manager, Acko General Insurance

“SanerNow’s patch management capabilities stand out from the competition since it can patch all the discovered vulnerabilities and perform other system-hardening actions. Even if no direct remediation is available, SanerNow applies security controls that provide workarounds for the vulnerabilities.”
– Swetha Krishnamoorthi, Senior Industry Analyst, Cybersecurity, Frost & Sullivan
Awards and Recognition







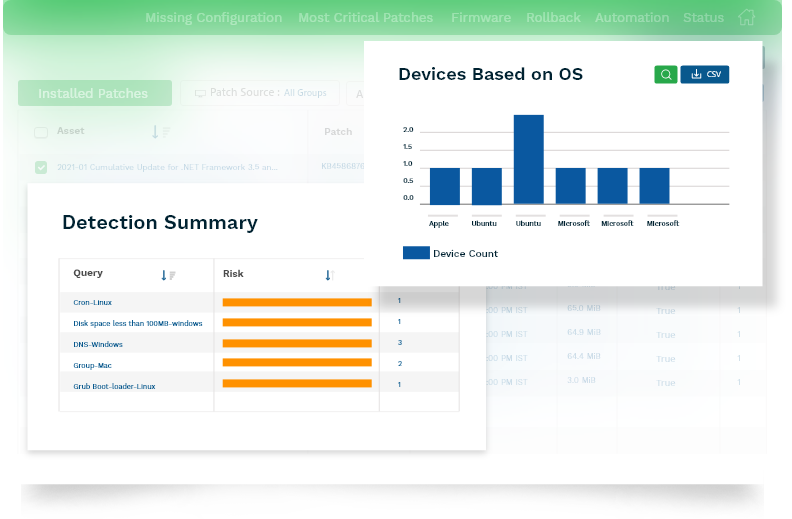
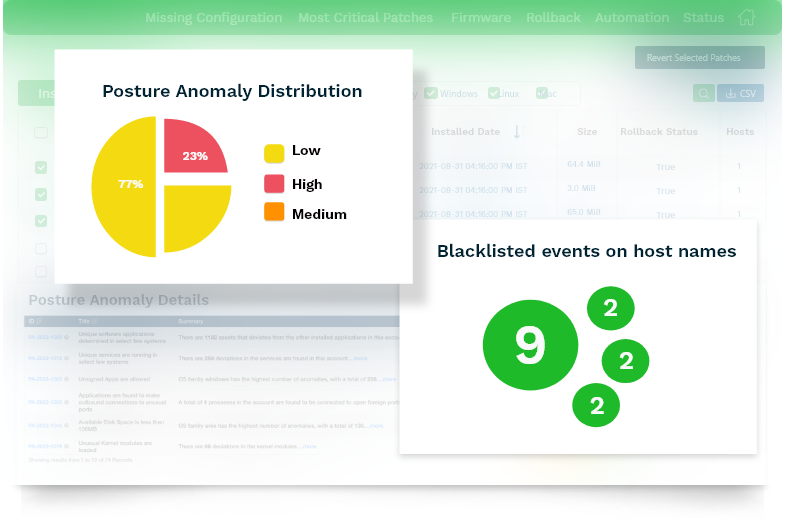
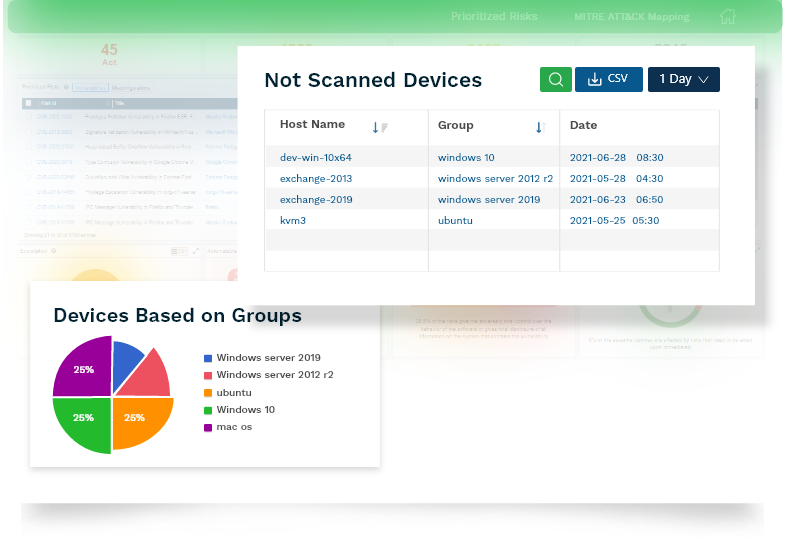
Monitor All Your IT Assets Continuously
Eliminate Anomalies with Holistic Cyber Awareness into Your IT
Gain collective and deeper visibility over your IT infrastructure. With intelligent insights, discover the most obvious outliers, aberrations, and deviations that are threatening security and eliminate the attack vectors instantly.
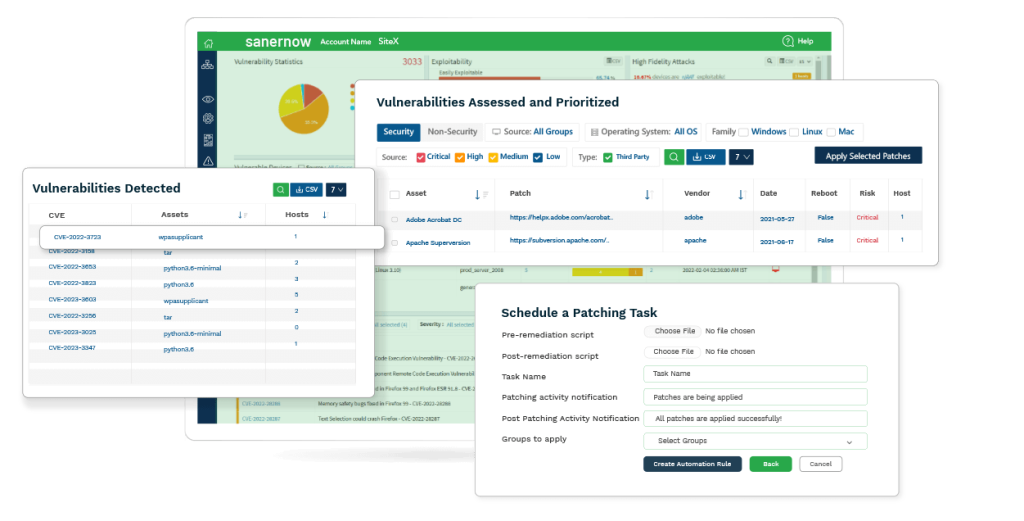
Detect Vulns, Exposures and Other Security Risks
Respond at the speed of threat to reduce your risk exposure with continuous scans to detect, assess, prioritize, and remediate vulnerabilities across your organization’s devices. Leverage the world’s largest SCAP vulnerability database with 175,000+ security checks.
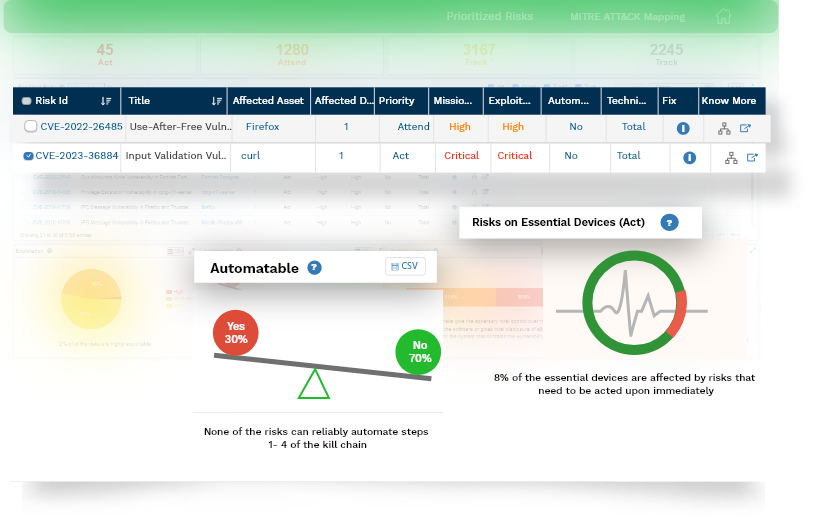
Prioritize Security Risks
World’s first SSVC-CISA framework implemented a prioritization model, powered by in-house vulnerability intelligence and unique risk categorization algorithms, effortlessly prioritizes the security risks based on upon their business context, exploitability, automatability, high-fidelity attacks, and more.
Achieve Compliance with Regulatory Standards
Patch OSs and Third Party Applications
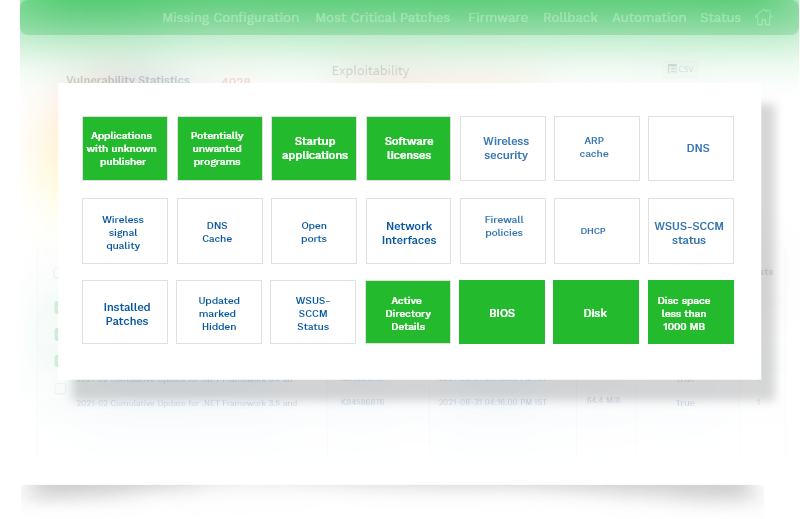
Mitigate Risks with 100+ Security Controls
Monitor and manage your endpoints and strengthen your security posture with real-time monitoring of 100+ endpoint metrics and security controls, threat detection and response, software deployment, application and device control and much more. Ensure system health with ongoing checks and updates to address misconfigurations and missing configurations.
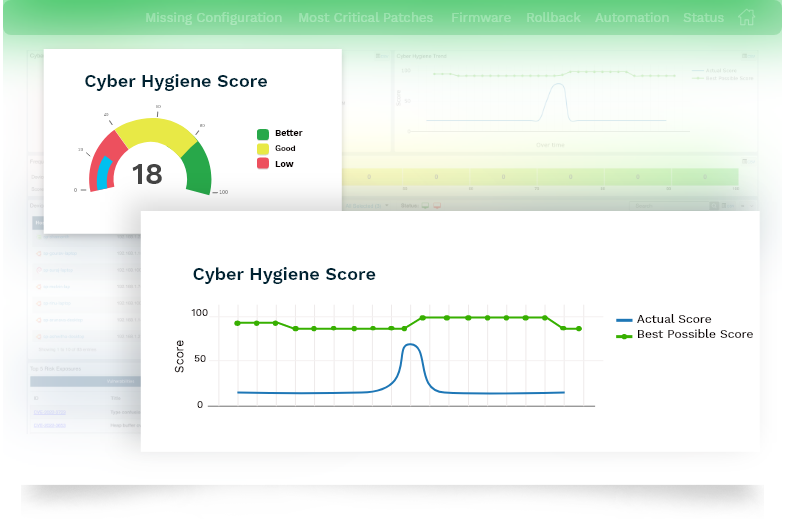
Quantify and Improve Cyber Hygiene
Measure your organization’s attack surface, quantify cyber hygiene, and fine-tune your remediation strategies. Leverage a data-driven proprietary scoring model to improve the cyber hygiene of your organization.
Key Resources
Experience the Impact of Continuous Vulnerability and Exposure Management on Your Cyberattack Prevention Strategy
Request a product walkthrough demo with one of our solution experts.





