WannaCry (also known as Wana Decrypt0r 2.0, Wannacryptor, WannaCrypt, wana Decryptor) ransomware disrupts 2-3 million devices in around 150 countries, taking important files hostage and demands a ransom of $600 worth of bitcoins. Vulnerability Management Software can tackle these issues.
The ransomware uses the old SMB vulnerability (MS17-010 released in April 2017) to spread across devices. There was no second doubt that crooks would find a way to weaponize the leaked NSA tool in April 2017. A good vulnerability management tool can solve these problems.
Image explanation:
When a mysterious group called Shadow Broker leaked the NSA tool, Microsoft provided a patch (MS17-010) for the affected operating systems. But organizations running older, unsupported versions of Windows (such as Windows XP) could not apply the update because Microsoft no longer supplies security patches for those versions of Windows.
How does it work?
Most ransomware is spread through vulnerabilities, hidden within Word documents, PDFs and other files normally sent via email, or through a secondary infection on computers already affected by viruses that offer a back door for further attacks. However, WannaCry is using the already available and publicly exposed NSA tool, which exploits MS17-010 vulnerability to deliver the ransomware to vulnerable devices around the globe.
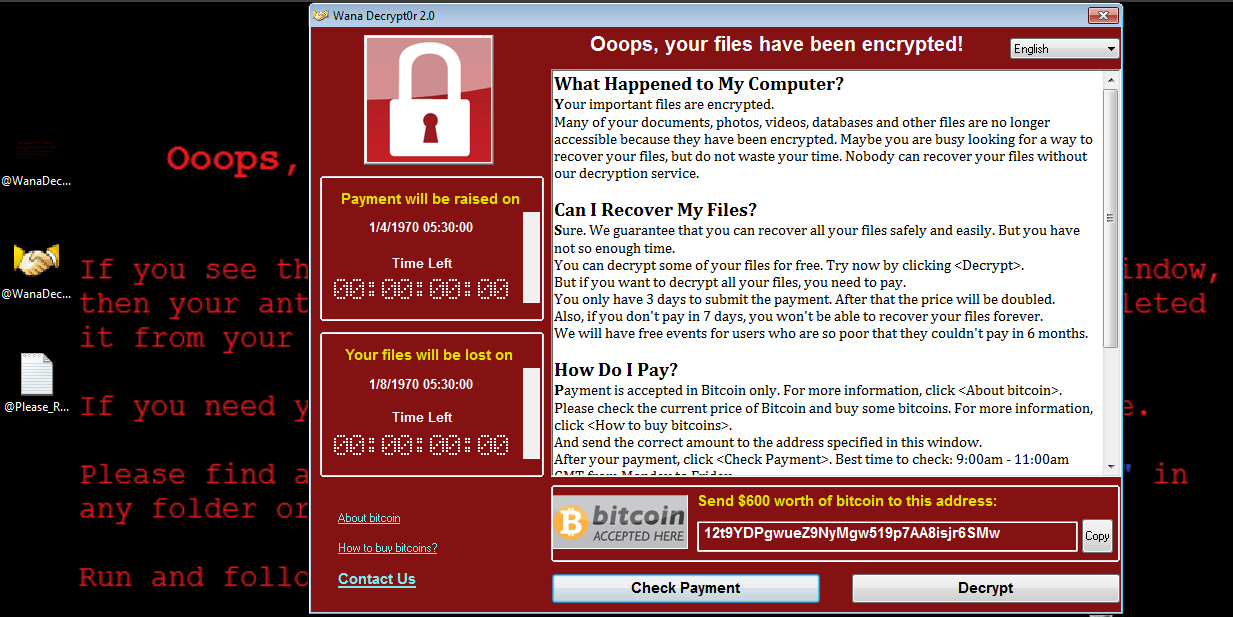
Once the ransomware executes, it encrypts documents which include important files, images, pdf files, and word documents, and delivers a ransom note in the form of a README file (@[email protected]). It also changes the victim’s wallpaper to a message demanding payment to return the files.
Below is a screenshot of the ransom note (@[email protected]).
Indicators of Compromise:
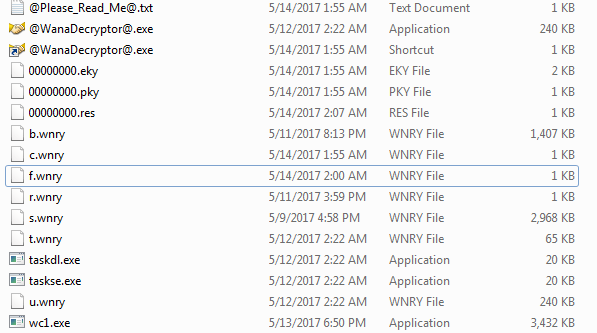
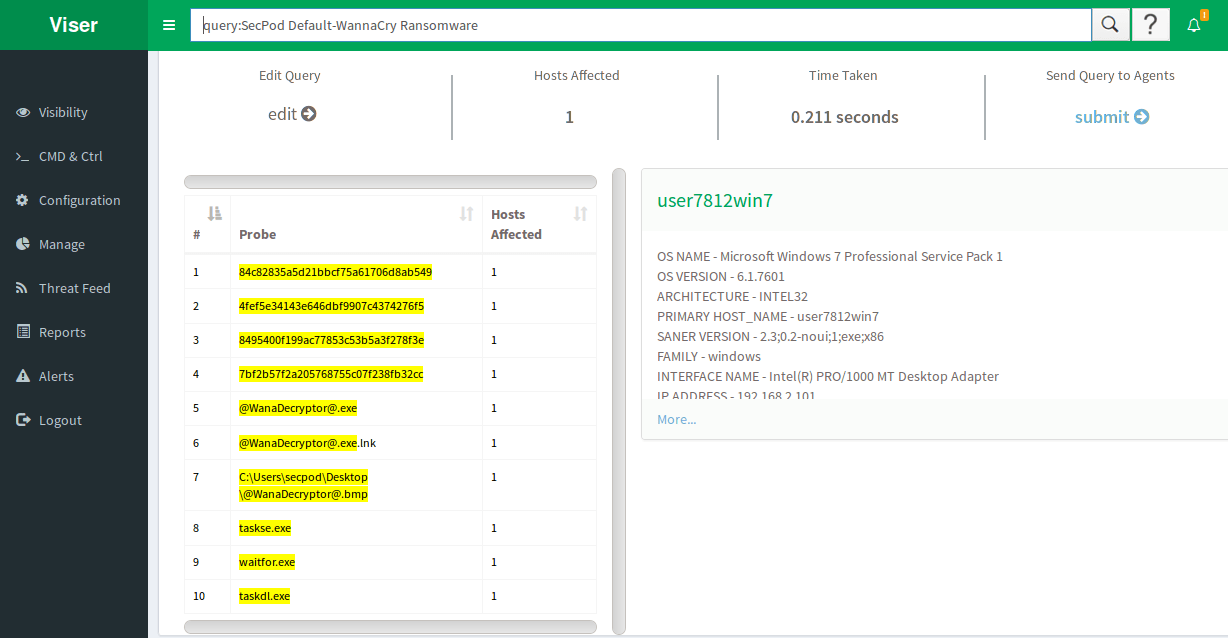
The ransomware creates the below files in the directory it is executed from.
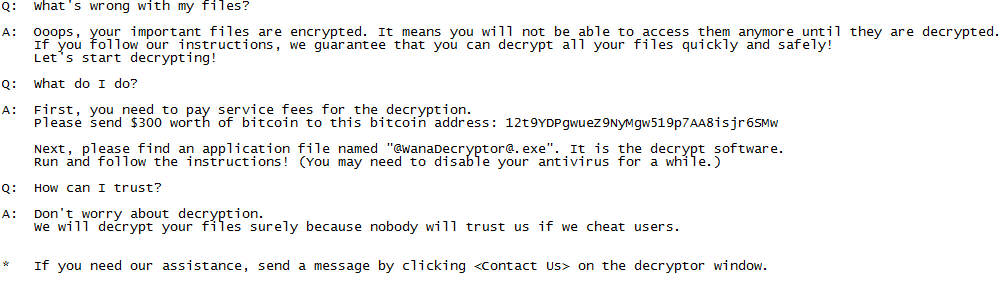
In addition to encrypting files, it also drops two executable taskdl.exe and taskse.exe. @[email protected] will help in getting back the files by providing info on payments. Click here to see what @[email protected] has to show.
File Extentions: “wnry”, “wncry”, “wcry’.
Also, a registry entry is upon execution i.e.,
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WannaDecrypt0r\wd
Who is affected by WannaCry Ransomware?
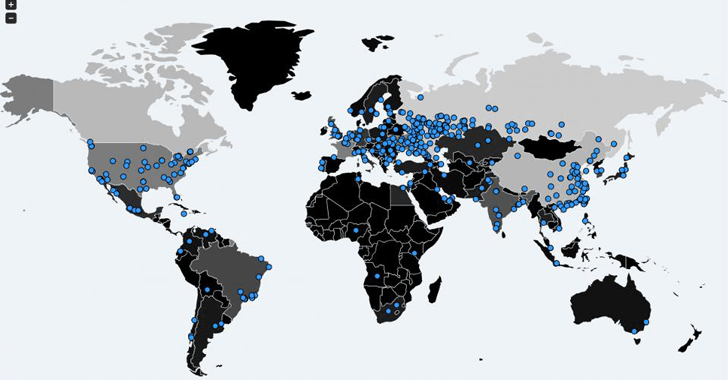
This is big, the impact is biggest ever in ransomware history, around the world, doctors and nurses are scrambling to treat patients without their digital records or prescription dosages. Ambulances are being rerouted. Millions of devices in around 150 countries are hit by the digital storm, which includes United Kingdom Hospitals, Russian banks, German national railway, Spain’s Telefonica, Mobile companies like MTS, Megaphone, FedEx, and users across countries. Recent victims also include Andhra Police computers in India.
Below is a screenshot of WannaCry Ransom-affected countries.
ImageSource: thehackernews
What makes WannaCry Ransomware so special?
The main reason why the ransomware is spreading wildly is because of its capability to penetrate through unpatched devices using SMBv1 protocol. MS17-010, known as the ETERNALBLUE exploit, is in use as a weapon to target the unpatched Windows older operating systems. Though the ransomware has clear IoC’s and is easy to debug, this ransomware stands aside as a giant because of the capability it carries.
Even if one system in an organization is in expose to this attack, the MS17-010 exploit would infect all other systems within the organization within minutes.
Mechanism of WannaCry Ransomware:
Since the targeted systems were those with SMB vulnerability, Microsoft has released an emergency patch for its unsupported Windows XP, Vista, Windows 8, Server 2003, and 2008 Editions. Organizations which are still using these unsupported versions are highly exploitable.
A British researcher known as “MalwareTech” came up with the idea of a ‘kill switch’. In this case, the ransomware tries to contact a domain. If the domain name were active, the malware would assume it was a false positive. WannaCry design is to shut itself down when it finds the domain active. Since only a single domain name hardcoding into the ransomware meant that registering that domain name had the effect of shutting down WannaCry, thus slowing down the infection rate.
The infection rate has reduced. A kill switch is just a band-aid, not a solution.
Moreover,
"The exploit code used by WannaCrypt was designed to work only against unpatched Windows 7 and Windows Server 2008 (or earlier OS) systems, so Windows 10 PCs are not affected by this attack," Microsoft says.
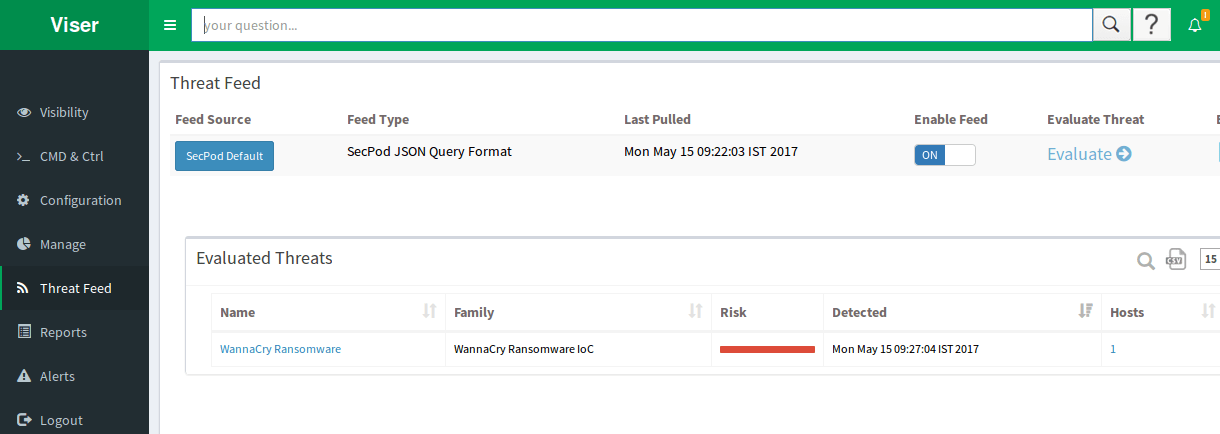
Saner in Action:
Below is a screenshot of WannaCry Ransomware Detection by Saner.
WannaCry marks are in this screenshot.
It is in confirmation that three Bitcoin addresses associated with WannaCry, as of 14th May, have had 103 confirmed payments. These bitcoin accounts have received a whopping 15 bitcoins, approx.
If you don’t want to cry over WannaCry, trust SecPod Saner updates and patch this emergency patch by applying security updates. Download Saner now and keep your systems updated and secure.
You’re only safe if you patch ASAP.