
This flaw allows macros to write more macros. Although this Macro-based self-replicating technique is not new, Microsoft has already introduced a security mechanism. In MS Office, that, by default, limits this functionality. The researcher has discovered a simple technique that could allow anyone to bypass Microsoft’s security. Control and create and spread self-replicating malware while hiding behind unsuspecting MS Word documents. Also, using a patch management tool is critical to patch this vulnerability.
How Attack Works:
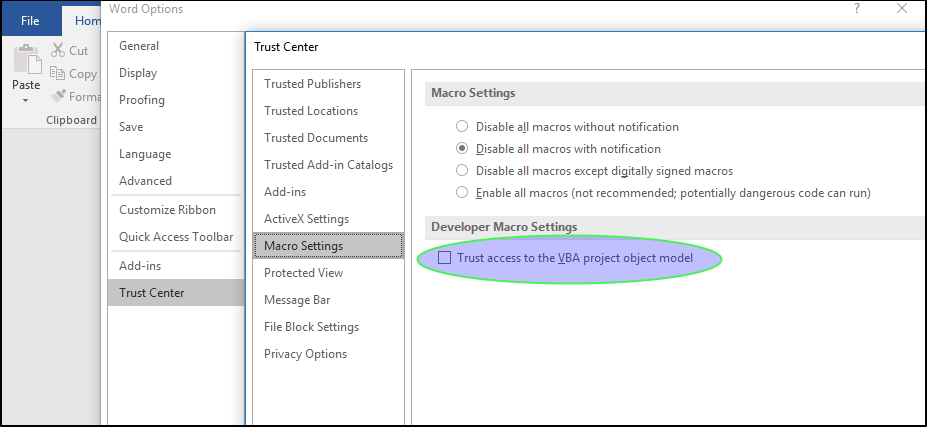
By default, Microsoft has disabled external (or untrusted) macros. To restrict default programming access to the Office VBA project. Object model users can manually enable “Trust access to the VBA project object model” whenever the requirement arises. When this setting enables, MS Office will trust all macros and run any code without showing a security warning or requiring the user’s permission.
Buono has created a PoC video demonstrating how an MS Word document embedding malicious VBA code could be used to deliver self-replicating multi-stage malware. i.e. It first enables macros by updating Windows registry entries and then injects malicious macro payload (VBA code) into every doc file the victim interacts with.
Mechanism:
A new macro-based self-replicating ransomware using the above-described attack technique has been recently reported by Trend Micro, which has been called “qkG“. This ransomware employs Auto Close VBA macro. This technique allows the execution of malicious macro when the victim closes the document. According to researchers, this ransomware is more of an experimental project or a proof of concept (PoC) rather than malware using actively. qkG is the first ransomware that scrambles one file type or file. It is one of the few file-encrypting malware written in Visual Basic for Applications macros. Also, it is unique because, unlike regular ransomware, that only uses macros to download ransomware. It employs malicious macro codes, a technique used by .lukitus, a variant of Locky ransomware.
Though this method hasn’t been in use by attackers as yet. If they do, it will become very difficult to deal with Self-Replicating Malware the situation as the attack method exploits a legitimate MS Office feature, and most antivirus software doesn’t issue a warning or block VBA code-based MS documents.
According to a researcher, Microsoft doesn’t consider it a security issue. And instead, Microsoft claims that the feature is of design to function like this. All external and untrusting macros will be disable by default as per the latest change in the settings of macros. This limits the macro’s default access to the Office VBA project model. Users must manually enable external macros by clicking “Trust access to the VBA project object model“. This setting allows MS Office to automatically trust all macros and run the code without displaying a security warning or asking for the user’s permission to run it.
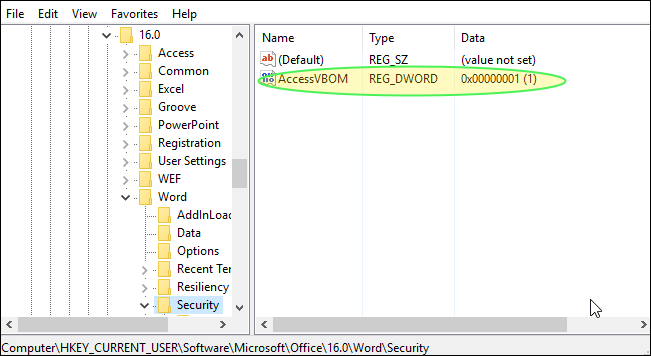
Buono suggests, “In order to (partially) mitigate the vulnerability, it is possible to move the “AccessVBOM” registry key from the HKCU hive to the HKLM, making it editable only by the system administrator.”
Impact:
This technique of bypassing default Microsoft Office settings can be useful. Trusting external or untrusting macros and automatically running any code without showing a security warning or requiring the user’s permission. Also, any victim who mistakenly allows the malicious doc file to run macros once his/her system remains open to macro-based attacks. However, the victim will unknowingly spread the same malicious code to other users by sharing infected office files from his/her systems.
Solution:
Currently, there is no solution to address this particular attack. We need to wait and see how Microsoft addresses this attack. Do they consider Buono’s suggestion to move particular registry keys under HKLM, or do they address it differently?
The best way to be safe from such malware attacks is to be suspicious of unusual documents. Receive via email and never click links inside those documents unless the source is adequately verified.
