Successful exploitation of RCE Vulnerability will allow an attacker to execute arbitrary code in the security context of the LocalSystem account and take control of the system, which is pretty close to full admin. It could install further malicious code and create accounts with maximum privileges. The vulnerabilities are tracked as CVE-2017-11937 and CVE-2017-11940 . Vulnerability management software can resolve these issues.
How to trigger the vulnerability:
Malware Protection Engine scans all the new files to check for threats or malware. This is the default behavior. To exploit this vulnerability an attacker has to convince the user to download or copy the crafted file to the local system in any location. The file can be in any form and with any extension. Unfinished download, temporary internet files cached by the browser, unopened email attachments are few examples. If real-time scanning is enabled, Malware Protection Engine starts scanning the crafted file as soon it appears on the local system. In case real-time scanning is disabled the vulnerability will be triggered when scheduled or manual scan is triggered. Thus it makes little easy for an attacker to exploit this vulnerability.
Malicious file delivery methods:
1) Send an email with malicious file as an attachment.
2) Send it through Instant Messenger service
3) Convince the user to download or copy the crafted file to the local system from USB or from website.
These are few easy ways to deliver the malicious file.
Affected Versions:
The Windows Malware Protection Engine will be enabling by default. And it is in use by Microsoft antivirus and antimalware software implemented in its solutions, including Windows Defender and Microsoft Security Essentials along with Endpoint Protection, Forefront Endpoint Protection, and Exchange Server 2013 and 2016, impacting Windows 7, Windows 8.1, Windows 10, Windows RT 8.1, and Windows Server.
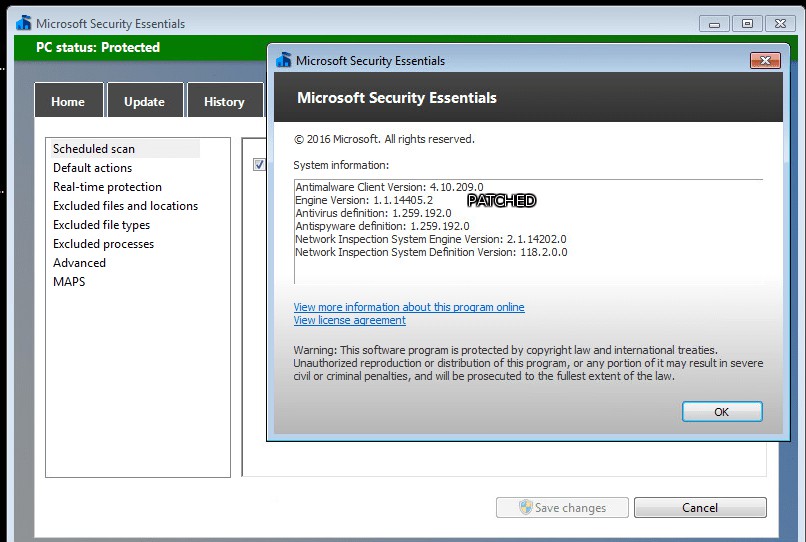
The latest version of Microsoft Malware Protection Engine affected by this vulnerability is 1.1.14306.0. And the first version of the Microsoft Malware Protection Engine with this vulnerability addressed is 1.1.14405.2.
The screenshot below shows Microsoft Security Essentials with a patched version of Microsoft Malware Protection Engine (1.1.14405.2).
Affected Products:
- Windows Defender - Microsoft Exchange Server 2016 - Windows Intune Endpoint Protection - Microsoft Forefront Endpoint Protection 2010 - Microsoft Security Essentials - Microsoft Exchange Server 2013 - Microsoft Endpoint Protection - Microsoft Forefront Endpoint Protection
Solution:
- Upgrade the Microsoft Malware Protection Engine version to 1.1.14405.2 or later for the affected software.
- Microsoft pushing out a hotfix which should be automatically fetching and applying to the products who use Malware Protection Engine. The update will be receiving automatically for all users if they are not opting to block MMPE updates by tweaking registry keys or via group policies.
- Manual installation of MMPE update needs in case if users are opting to block MMPE updates.
Immediate installation of new security patch is the recommendation for all users.
SecPod SanerNow detects these vulnerabilities and hence, automatically fixes it by applying security updates. Therefore, download Saner now and keep your systems updated and secure.