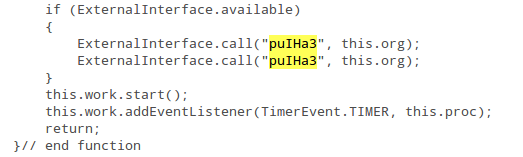
A use-after-free vulnerability is present in Microsoft Internet Explorer 10 ( CVE-2014-0322 ), which allows remote attackers to execute arbitrary code.
This vulnerability exploited in the wild as a Watering hole attack, in which the attacker injects a javascript or hidden iframe into a website, which will redirect to a malicious page. Therefore, a good vulnerability Management Tool can resolve these issues.
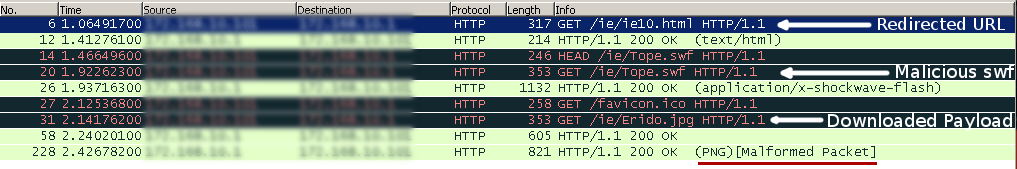
In this attack, users who visited the compromised site will encounter an iframe that redirects to the malicious page in the background. However, the below image shows the Wireshark captured traffic of the redirected URL. Vulnerability Management System can prevent these attacks.
Wireshark:
The Redirected page embeds a Flash file, which in turn executes the malicious code.
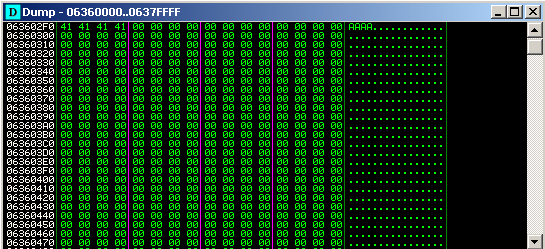
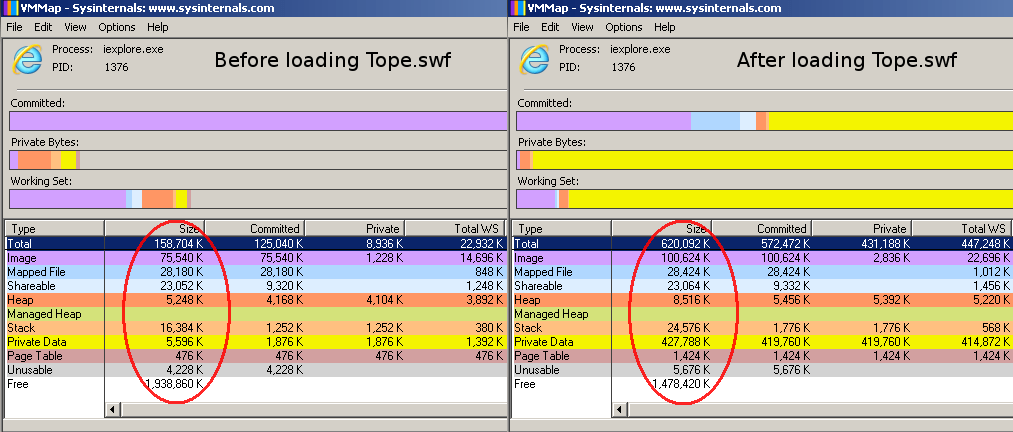
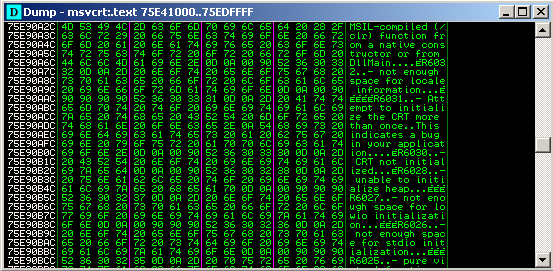
The loaded Tope.swf file will cause heap sprays with the below data repeatedly.
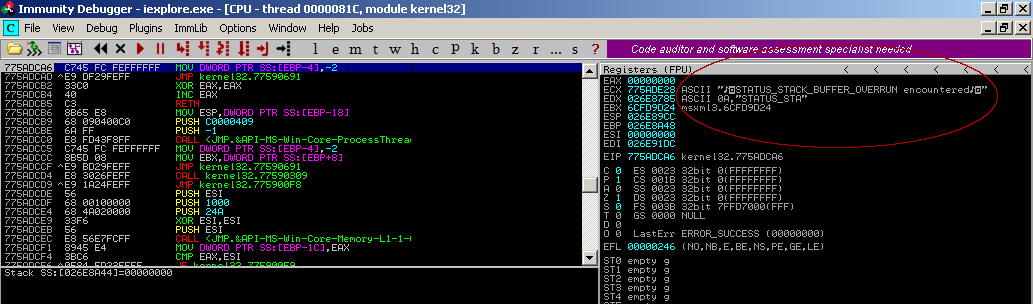
The below image shows the heap before and after the Heap spray.
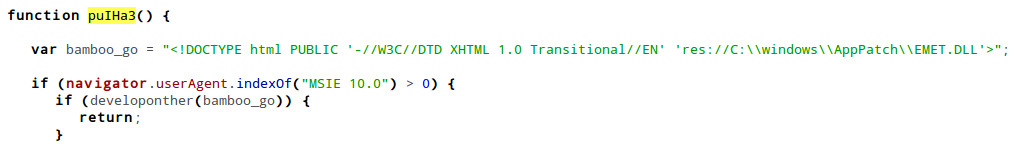
The control then is transferred to the javascript from flash file, defined in the tope.as3(Action Script of the Flash file)
Then the javascript will check for EMET.DLL (The Enhanced Mitigation Experience Toolkit) and Internet Explorer 10 from user agent. It will exit the process if the file is present or if it’s not Internet Explorer 10.
Then the control is transferred back to the swf, which will download the payload as tope.jpg and extract two files to the temporary folder.
- sqlrenew.txt
- stream.exe (md5: c869c75ed1998294af3c676bdbd56851)
Tope.swf will load the contents of the sqlrenew.txt into memory and this helps in the execution of stream.exe
That stream.exe is creating three more files,
- stream.exe
- MediaCenter.exe
- regsvr32.exe
- cmd.exe
- MediaCenter.exe
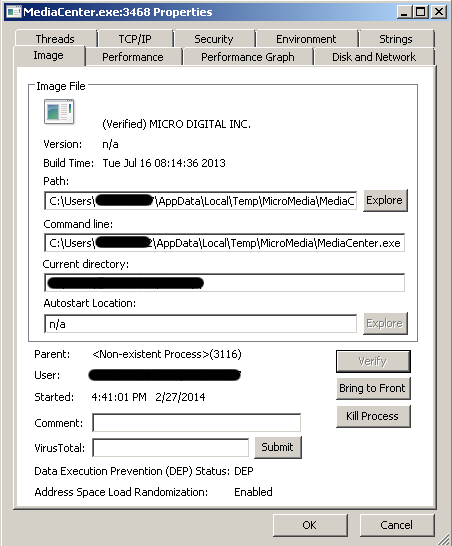
Next, MediaCenter.exe and cmd.exe processes are getting created, as shown in the below picture.

And MediaCenter.exe looks like a legitimate file and is also digital sign and verified as MICRO DIGITAL INC.
This will finally contact a remote server, oa.ameteksen.com (198.2.209.211), and is in use to send sensitive information.
- Thanga Prakash