Any program intended to disrupt computer or network operation, gather sensitive information, or gain access to private computer systems or networks is malware. Virus, Spyware, Worm, Adware, Trojan horse, Rootkit, Scareware are all examples of malware. Malware analysis is an art of dissecting the malware in order to understand how it works, and how to defeat or eliminate it. We don’t have to worry about malware if we have a vulnerability management tool.
There are two fundamental approaches to malware analysis:-
- Static analysis, which involves examining and analyzing the malware without executing it.
- Dynamic analysis, which involves executing the malware on the system and analyzing it.
Static Analysis approach:
- A very first step to malware analysis is to run malware through multiple antivirus programs, which may already have identified it. It can save us from lot of time and work. Moreover, A free online service that analyzes files enabling the identification of viruses, worms, trojans and other kinds of malicious content detected by various antivirus engines and website scanners is available at https://www.virustotal.com
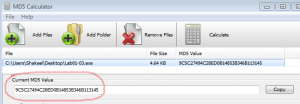
- Next, people use the Hashing technique to uniquely identify malware. They run the malicious software through a hashing program that produces a unique hash to identify that malware. To see if the file has already been identified, one can search for that hash online, which can again save a lot of effort. You may find one of the online malware hash databases at https://isc.sans.edu/tools/hashsearch.html
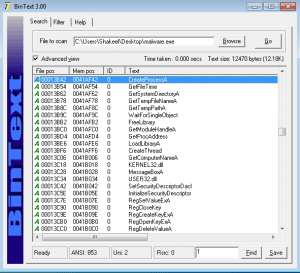
- Use any Strings program like BinText or Strings to display all the strings within executable. A program contains strings if it prints a message, connects to a URL, or copies a file to a specific location. These strings can give us an idea of working of executable. However, packing or obfuscating the executable will result in the inability to see any useful strings. In that case dynamic analysis is the option.
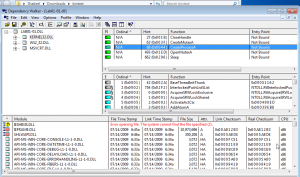
- Check the dynamically linked list in the executable with any of the tools available. The libraries used and functions calls are often the most important parts of a program, and identifying them is particularly important, because it allows us to guess at what the program does. One of the commonly used tools is Dependency Walker, which lists all dependent modules within the executable.
- Assembly-level disassemblers like IDA Pro allow you to use the most essential and valuable static malware analysis technique, disassembling the executable. IDA Pro is a multi-platform assembly level disassembler that translate machine executable code into assembly language source code. You can use it to run in either text mode or graph mode. Text mode simply arranges source code into assembly level code and then while as in graph mode code is divided into blocks and arranged according to the logic program uses while executing, highlighting jumps and branches. Other useful windows IDA Pro provides include Functions window, Strings window, Names window, Exports window, Imports window and then Structures window.
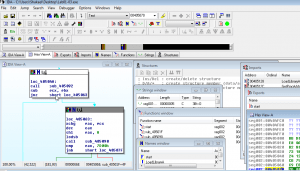
IDA Pro This is the first step to approach malware analysis.
Dynamic Analysis approach:
-
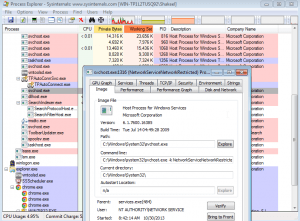
Check for the File system and process activity using procmon or proc explorer or any other available tool. Procmon monitors all system calls it can gather as soon as possible. In contrast, Process Explorer monitors the processes running on a design and shows them in a tree structure that displays child and parent relationships.
-
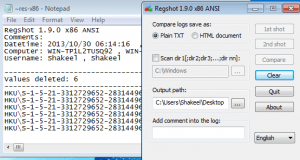
Determine the recent Registry activities and identify the recently added or deleted keys. Regshot is a good tool for this purpose. Regshot provides comparison of registry entries before and after running executable.
-
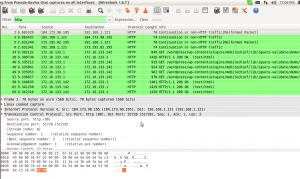
Monitor for Network activity using apate DNS, or wireshark. Users can utilize Apate DNS to check the DNS requests made by malware, while they can use Wireshark for packet sniffing.
-
Test or examine the execution of malware by means of any low level debugger like Ollydbg or Windbg. A programmer uses a debugger to test or examine the execution of another program. Low level debugger traces registers, recognizes procedures, API calls, switches, tables, constants and strings, as well as locates routines from object files and libraries. It also provides the function to pause the execution of program under test and check its state. Below is snapshot of Olly in action.
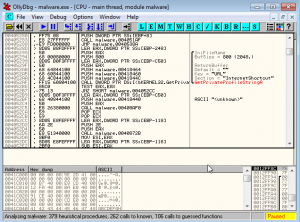
Olly Debugger This is the second step to approach malware analysis.
- Shakeel

Nice post!! thanks