A new flash zero-day (CVE-2014-0515) exploit exists in the wild and used to target Flash Player users on Windows systems. The vulnerability discovered by Kaspersky Lab in Mid-April. Therefore, a good vulnerability management tool can prevent these attacks and become the shield of your cyber defense arsenal.
There is a buffer overflow vulnerability in the Pixel Bender component designing for video and image processing that can be of use to execute arbitrary code. This flaw allows attackers to take complete control of the systems remotely. An attack is conducting by convincing users to visit a specially crafted website hosted by an attacker. Hence, a Vulnerability Management System can prevent these attacks and keep your organization’s infrastructure secure and safe.
According to the Kaspersky Lab blog, they found two new SWF exploits in mid-April. These exploits stored as movie.swf and include.swf at an infected site. The only difference between the two pieces of flash zero-day malware is their shellcodes. The Action Script code inside was neither obfuscated nor encrypted.
Affected versions are Adobe Flash Player 13.0.0.182 and earlier on Windows, 13.0.0.201 and earlier on Mac, and 11.2.202.350 and earlier on Linux systems.
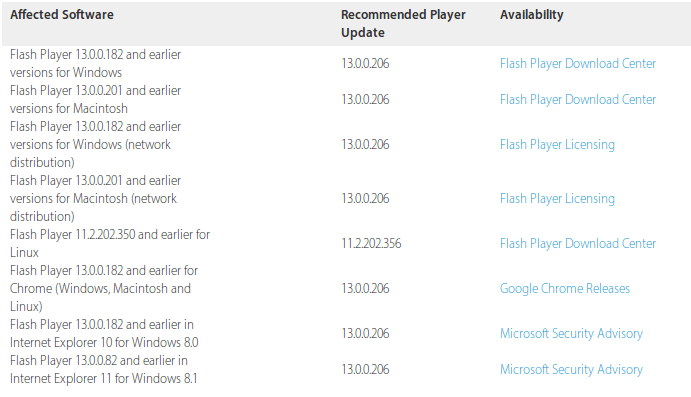
Adobe released a security bulletin APSB14-13 addressing CVE-2014-0515 vulnerability.
SecPod Saner helps fix these issues by upgrading the Adobe Flash Player to a non-vulnerable version, through its easy-to-use interface.
Download Saner now and keep your systems updated and secure.
- Veerendra GG

